Integrate an existing AWS CloudTrail
-
AWS integration update
This AWS integration will be retired in the future and should no longer be used. We recommend that you migrate to Sophos Cloud Optix to take advantage of its advanced capabilities.
Use Sophos Cloud Optix to integrate AWS to Sophos Central. For more information, see Sophos Cloud Optix.
MSP Flex customers must have the Public Cloud integrations license pack to use this feature.
If you want to integrate an existing AWS CloudTrail with Sophos Central, you must configure it first.
To check and configure your trail, do as follows.
Review your trail
-
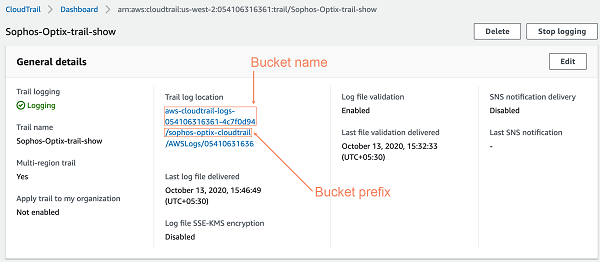
In AWS, go to your CloudTrail dashboard and copy your export bucket name.
This is used to configure the SNS topic and is used in Sophos Central later.
-
You can also copy the S3 bucket prefix to use later. Bucket prefixes are optional.
For more detail on S3 bucket prefixes, see the steps on creating a new bucket in Amazon's help. See Creating a Trail.
The following screenshot shows how to select the bucket name and bucket prefix.
Configure SNS topic and access policy
- In AWS, create an SNS topic in the same region where your S3 bucket is used to export CloudTrail, or edit an existing SNS topic.
- Copy the name of this SNS topic.
-
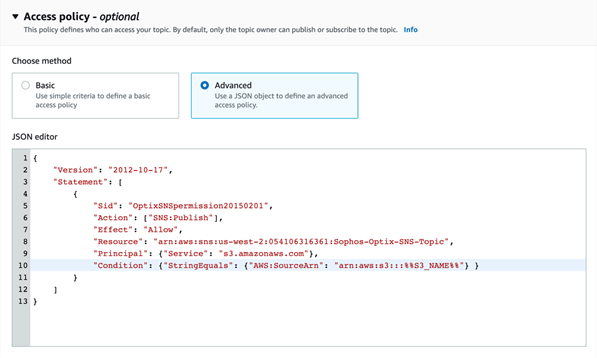
In the JSON editor, specify the access policy as follows:
- Replace the
Resourcevalue with the SNS ARN you are using. -
Replace the bucket name in
Conditionwith the CloudTrail bucket name you copied earlier.The following screenshot shows an SNS topic JSON editor with the lines to be customized.
In AWS the access policy is shown as optional, but it isn't optional with Sophos Central. It is required to set up S3 bucket notifications.
- Replace the
-
Save the SNS topic.
Configure S3 bucket notifications
- In AWS, go to your S3 bucket.
- To set up a new notification event, select Properties > Events > Add notification.
- Check that you don't have any existing notifications set on CloudTrail create events.
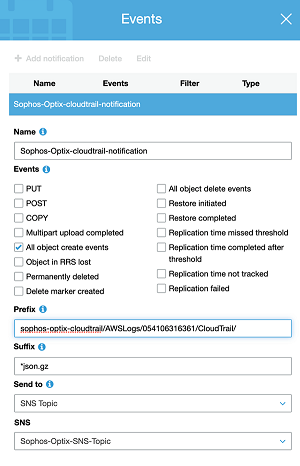
- Enter a name for the notification event.
- Select All object create events.
- Enter :
json.gzas the Suffix value. -
To create your Prefix value, enter the bucket prefix you copied earlier, then
/AWSLogs/, then your account ID, then/CloudTrail/.The format must be:
<Bucket prefix>/AWSLogs/<AccountId>/Cloudtrail/If you're using an AWS Organizations managed CloudTrail, or you're exporting CloudTrails from multiple accounts into a single account, you must create a separate event for each account ID.
-
Set Send to to
SNSand use the name of the SNS topic you created earlier.The following screenshot shows the Events menu settings.
-
Click Save.
Success notifications now appear in your S3 bucket properties.
Go to Sophos Central and continue integrating your AWS CloudTrail.