Microsoft 365 integrations
You can integrate Microsoft software and services with Sophos Central.
Configure integrations
To configure an integration, click Threat Analysis Center > Integrations > Marketplace, and click the integration name.
For details of how to configure each integration, see the following pages:
- Microsoft 365 Management Activity
- Microsoft 365 Response Actions
- Microsoft Graph security API (Legacy)
- MS Graph security API V2
This video guides you through configuring all the Microsoft integrations.
How the integrations work
The Sophos XDR platform integrates with Microsoft using the Microsoft Management Activity API and the Microsoft Graph Security API. Sophos uses both APIs independently to detect threats in the Microsoft 365 environment.
M365 Management Activity
Using the Management Activity API, the Sophos XDR platform ingests audit logs from the Microsoft 365 environment. Sophos uses these audit logs both for threat detection and for collecting additional supporting information for analysts during an investigation. These audit logs are available to all Microsoft 365 customers, regardless of the licensing used in their environment.
The Management Activity API provides access to M365 audit logs, including logs for the following activities:
- File and folder access, downloads, edits, and deletions
- Sharing activities
- Changes in settings
- User sign-ins
- Administrative actions, such as changes to tenant configuration settings
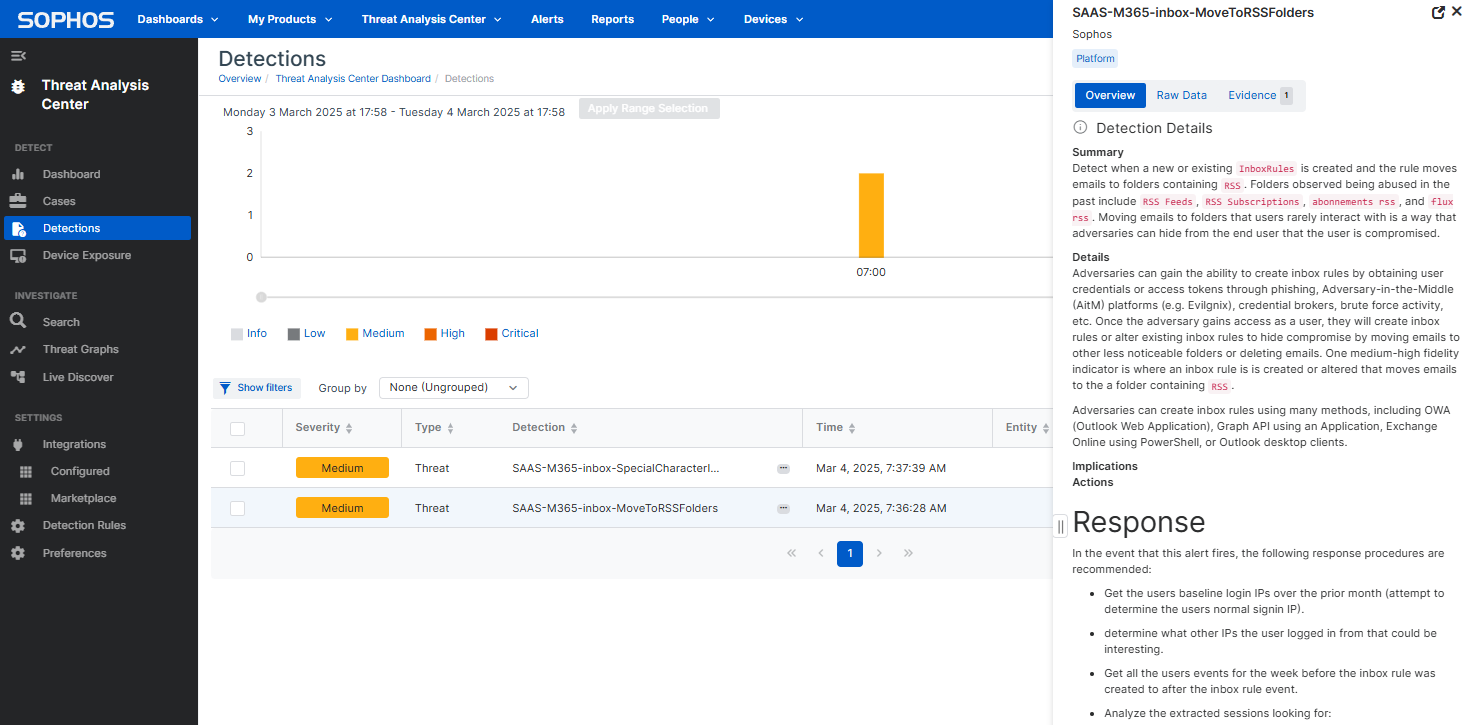
The Sophos detection engineering team regularly creates detection rules based on these audit logs from Microsoft. These detection rules allow analysts to investigate scenarios that could indicate Account Compromise or Business Email Compromise (BEC). Example indicators include inbox rule manipulation, session token theft, Man-in-the-Middle attacks, malicious application consent, and more.
You can see Sophos-based M365 detections in your environment by going to the Detections page in Threat Analysis Center. The detections are labeled as SAAS-M365-xxxxx and are included in the "Platform" category. You can filter on this category as seen in the example below:
With the Microsoft Management Activity API audit logs stored in the Sophos Data Lake, analysts can use them when investigating incidents in an environment. For example, a user's sign-ins can be reviewed to confirm or identify suspicious sign-in events, or to investigate account activity in the Microsoft 365 environment while the account was compromised.
For more information on which data Microsoft provides via the Management Activity API, see Audit log activities.
M365 Response Actions
You can integrate Microsoft 365 Response Actions with Sophos Central. This lets you take action to address issues detected in data sent to Sophos by the M365 Management Activity integration.
In the Cases section of Sophos Central's Threat Analysis Center, you'll be able to look at the detection and take the following actions:
- Block or allow user sign-in. This helps stop unauthorized access to your systems.
- Disconnect or revoke all current sessions. This helps isolate compromised accounts and stops lateral movement of threats.
- Turn off inbox rules for the user. This helps stop malicious forwarding of sensitive emails, security evasion tactics, deletion of evidence, and more.
For information on how cases work, see Cases. For information on response actions, see Respond to cases.
MS Graph security API V2
This integration is for the MS Graph security API Alerts v2 (Incidents and Alerts) service. We recommend you use this version of MS Graph security API.
Using the MS Graph security API, Sophos ingests detection events generated by Microsoft, based on telemetry observed in the Microsoft ecosystem. Depending on the severity of these Microsoft detection events, cases are created for analysts to investigate and respond to.
The components, or "providers", that generate detection events to the Graph security API are as follows:
- Entra ID Protection
- Microsoft Defender 365
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Microsoft Purview Data Loss Prevention
- Microsoft Purview Insider Risk Management
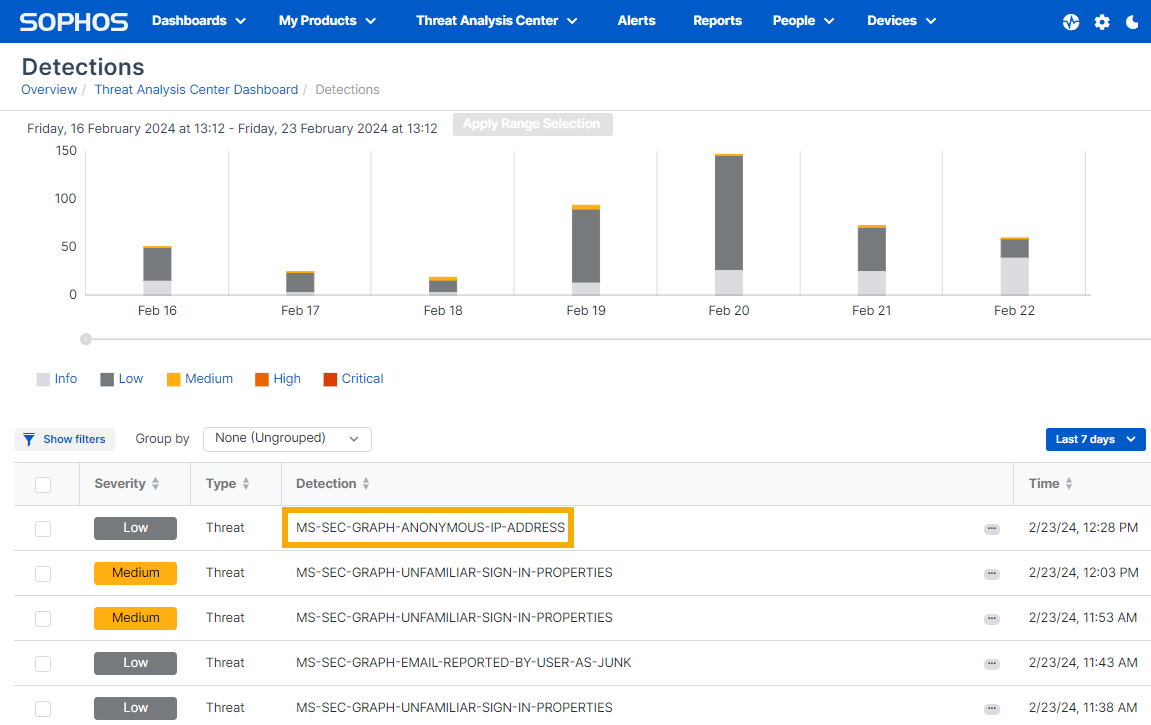
You can see detection events received by the Microsoft Graph security API on the Detections page in Sophos Central. The detections are labeled MS-SEC-GRAPH-xxxxx, as seen in this example:
The specific Microsoft detection events generated by these products and available for ingestion via the Graph security API depend on the Microsoft 365 licensing used in the environment. This can include the individual per-user plan, and any additional add-ons or bundles added to users or the Microsoft 365 tenancy.
We recommend that you consult your Microsoft 365 licensing specialist to understand which providers, detection events, and alerts are included in each plan, add-on or bundle. However, we can provide the following guidance:
- The Microsoft 365 E5 plan or E5 Security Add-on includes all Microsoft detection events that are used to create cases to be investigated.
- For Entra ID Protection-based identity alerts, you need Entra ID P2 plans (bundled with the E5 plans mentioned above).
- For other components, consult your Microsoft licensing expert to understand which Microsoft bundles or individual SKUs you need to access those components and their Graph Security detection events.
For more information about the Graph security API and alerts generated by specific providers, see Alerts and incidents.
MS Graph security API (Legacy)
This integration is for MS Graph security API, which uses the MS Graph legacy alerts service. Microsoft have deprecated this version and will remove it by April 2026.
We recommend that you integrate the MS Graph security API v2 (Alerts and Incidents) service instead. See Microsoft Graph security API V2 integration.