Intelix reports
SophosLabs Intelix analyzes suspicious files that are submitted to Sophos.
How files are submitted
Sophos software on your devices automatically submits files to Intelix if they need investigation.
You can also submit files to Intelix manually. Go to Threat Analysis Center and submit a file by one of these methods:
- On the Threat Graphs page, select a file and click Request latest intelligence.
- On the Detections page, open the detection's details and find SHA 256. Click the three dots
 beside it, select Enrichments and then Submit to SophosLabs Intelix.
beside it, select Enrichments and then Submit to SophosLabs Intelix.
You can see the Intelix analysis in the detection details, as described in See Intelix verdicts and reports.
How Intelix analyzes files
Intelix tries to determine the origin, workings, and possible impact of suspect or malicious files.
Intelix applies two different methods of analysis:
- Static analysis uses machine learning, file scanning, and reputation to assess suspicious files.
- Dynamic analysis runs suspicious files in a sandboxed environment to observe their behavior.
Each analysis gives a verdict on the risk level of the file. Intelix combines them to give an overall verdict.
See Intelix verdicts and reports
To see Intelix verdicts on a file, do as follows:
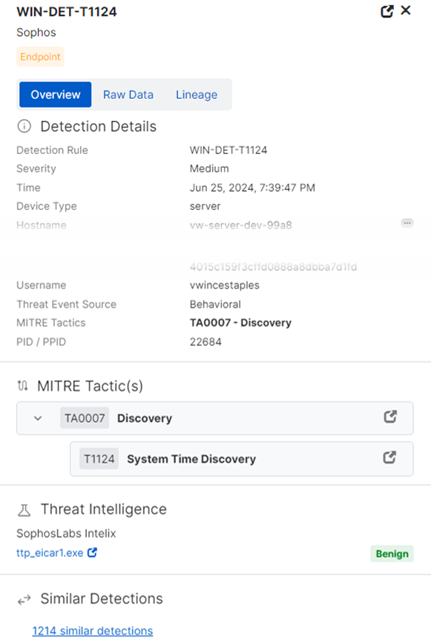
- Go to Threat Analysis Center > Detections.
-
To see detection details, find the detection in the table and click anywhere in its row.
A new pane slides out on the right of the screen.
-
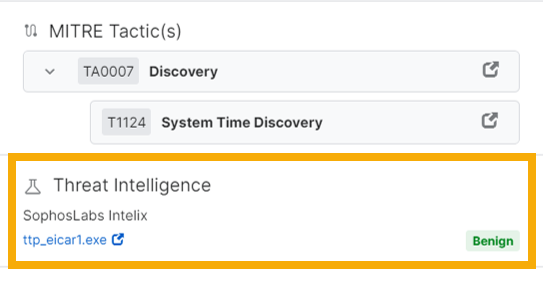
Scroll down to Threat Intelligence. This shows the overall verdict from Intelix, for example Benign.
-
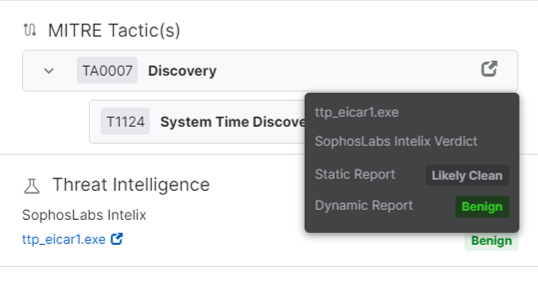
Hover over the overall verdict to see the separate verdicts of the Static Report and the Dynamic Report.
-
To see the full Intelix analyses, click the filename shown in Threat Intelligence.
-
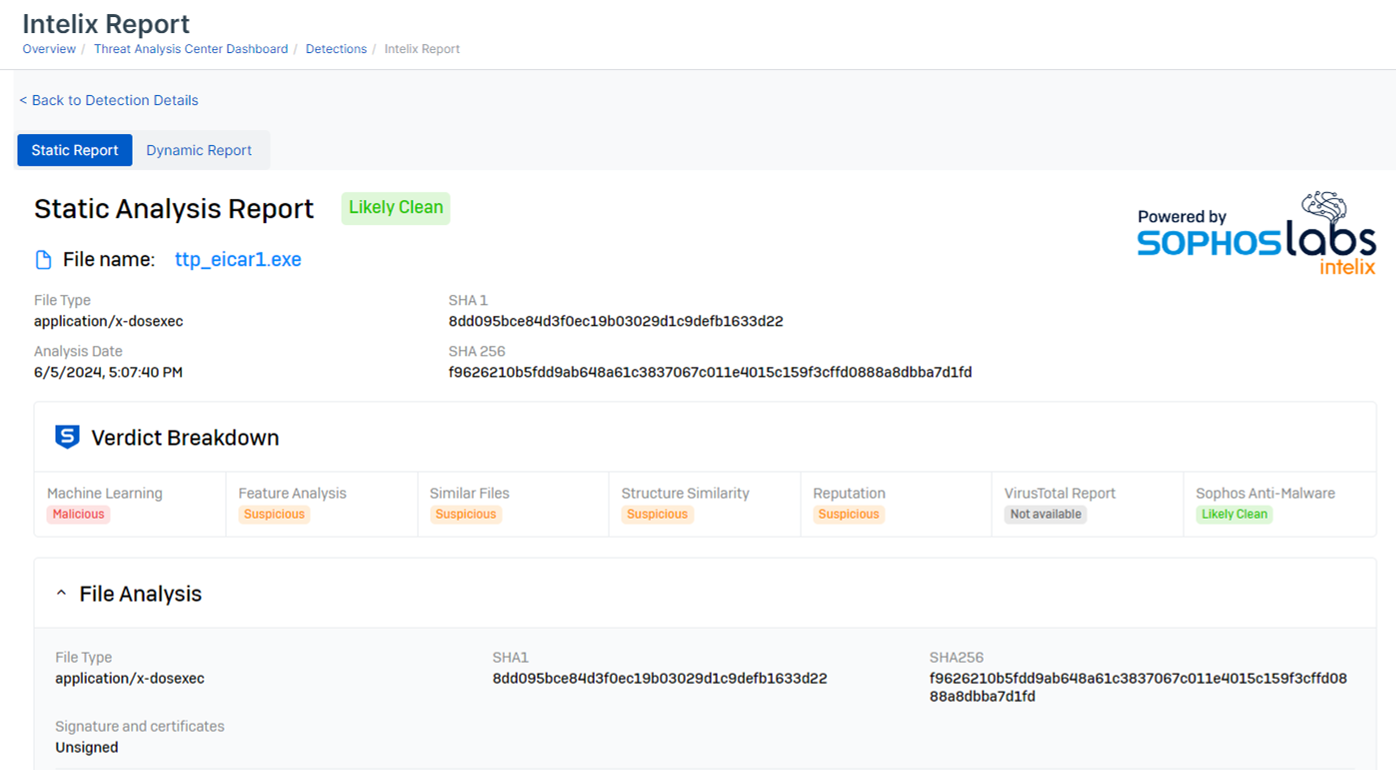
By default, the Static Analysis Report is open. This shows a verdict on the threat risk, as measured by different analyses.
-
Click the Dynamic Report tab to see the Dynamic Analysis Report. If you don't see this tab, no dynamic analysis report is available for this file.
The report shows the following:
- MITRE attack tactics and techniques used by the threat.
- Processes that were run.
- Network activity.