Process details
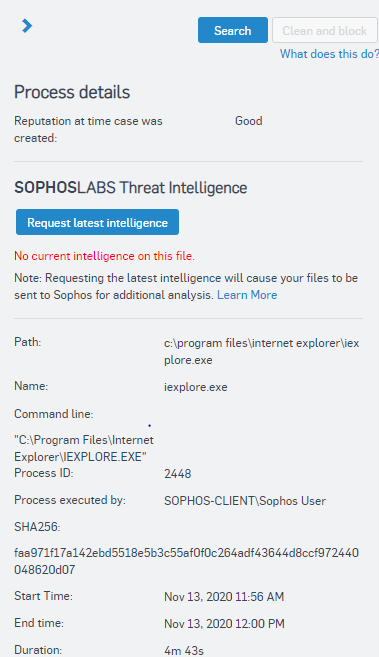
When you click an affected file in a threat graph, the Process details pane shows the latest details of the file.
These include the global reputation of the file, path, name, command line, process ID, executing user, SHA256, start and end time, and duration. The following screenshot shows the details of a process associated with Internet Explorer 11:
Request latest intelligence
If the file has not been submitted to Sophos for additional analysis, you see the text No current intelligence on this file.. If the file hasn't been submitted, or you want to see if there's any updated intelligence, click Request latest intelligence. This sends a request to the computer to upload the file to SophosLabs.
When the file has been analyzed, you see the latest information about the file's global reputation and whether you need to investigate.
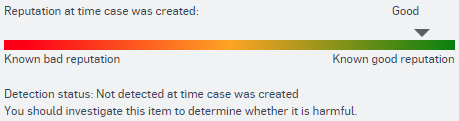
The reputation score shows the trustworthiness of the file. Sophos scores the reputation on a scale from red (bad) to green (good). Known clean files are shown in the green range of the scale and known malicious files are shown in the red range.
The reputation score goes up or down for many reasons, including when and how many times the file was seen by Sophos and the static/behavioral properties of the file. When the file is seen for the first time, it may get a score in the orange range (unknown) because it is a new file. After Sophos has analyzed it, the score may move to the known bad or known good range.
If you have Sophos XDR, you also see more information and options, as follows.
Report summary
Under Report summary, you can see the file's reputation and prevalence and the results of our machine learning analysis, which indicate how suspicious the file is.
Machine learning analysis
| Setting | Description |
|---|---|
| Prevalence | Indicates how often SophosLabs has seen the file. |
| First seen | When SophosLabs first saw the file in the wild. |
| Last seen | When SophosLabs last saw the file in the wild |
| Machine learning analysis | Summarizes how suspicious the file is. |
Machine learning analysis
Under Machine learning analysis, you can see full results of our analysis.
Attributes shows a comparison of the file's attributes with those in millions of known bad and known good files. This enables you to determine how suspicious each attribute is and therefore whether the file is likely to be good or bad. You may see the following attributes:
- Imports describes the functionality that the file uses from external DLLs.
- Strings describes the most significant strings in the file.
- Compilers specifies what was used to compile the source code, for example C++, Delphi, Visual Basic, .NET.
- Mitigation describes techniques that the file uses to avoid being exploited.
- Resources specifies a resource that seems to be compressed or encrypted.
- Summary often relates to build or compilation dates, for example.
- Packer often specifies something of note about a specific section of the file, for example a suspicious section name or the fact that a section is both writable and executable.
- Peid refers to the output of PEiD, a third-party tool that scans a PE file against various malware signatures.
- Btcaddress shows any valid Bitcoin address that is found in the file.
- Findcrypt shows any suspicious cryptographic constants.
Code similarity shows a comparison of the file with millions of known bad and known good files, and lists the closest matches. Other matches count toward the result and may affect the rating for the file. The more bad files the file matches and the more closely it matches them, the more suspicious the file is.
File properties
Under File properties, you can see key information about the file itself, for example product, type, copyright information, version, company name, size, and timestamp.
File breakdown
PE file sections shows information about each section of the file, for example code, data, or resources. Section names may indicate specific packers, compilers, or functionality, for example. Malware can make itself obvious by including strings that include expletives, slang, and so on.
There is also information about the size of the sections, on disk and in memory. Sometimes, a section is very small or very big, and sometimes only on disk or in memory. You can see the entropy of the section, and whether it's readable, writable, or executable. All of this helps you to determine whether a section is packed, contains data, contains code, or is unusual.
For more information about file sections, see Section Table (Section Headers).
PE imports shows which DLLs the file uses and, if you expand each one, which APIs are imported from them. You can see DLLs used for network activity or APIs that may help with password extraction. The DLL names may be really common. Alternatively, they may be unusual enough that an internet search indicates that they're suspicious or malicious, and therefore that the file importing from them is too. For more information about PE imports, see Import Library Format.
You may also see PE exports, which shows what code the file makes available for other files to use. This may appear to be harmless or obviously bad. For more information about PE exports, see The .edata Section (Image Only).
Search
Click Search to find more examples of the file on your network.
Clean and block
If the file is suspicious, you can use Clean and block.
This cleans up the file (and associated files and keys) on any device it's already on. It also adds it to a blocked list so that it can't run on other devices. You can see blocked items under General Settings > Blocked Items.