Use agentless and agent-based ZTNA in the office
You can access internal applications through ZTNA from inside your office, with agentless access or using the ZTNA agent.
Use agentless ZTNA in the office
Users in the office normally access internal applications by FQDN, so their requests are sent to the internal DNS server.
The internal DNS server has A records for the internal applications, so the user goes directly to the applications, which means they don't go through the ZTNA gateway.
You can send users through ZTNA in the following ways:
- Point users to an external DNS server.
- Add an alternative DNS record for the internal application on the DNS server.
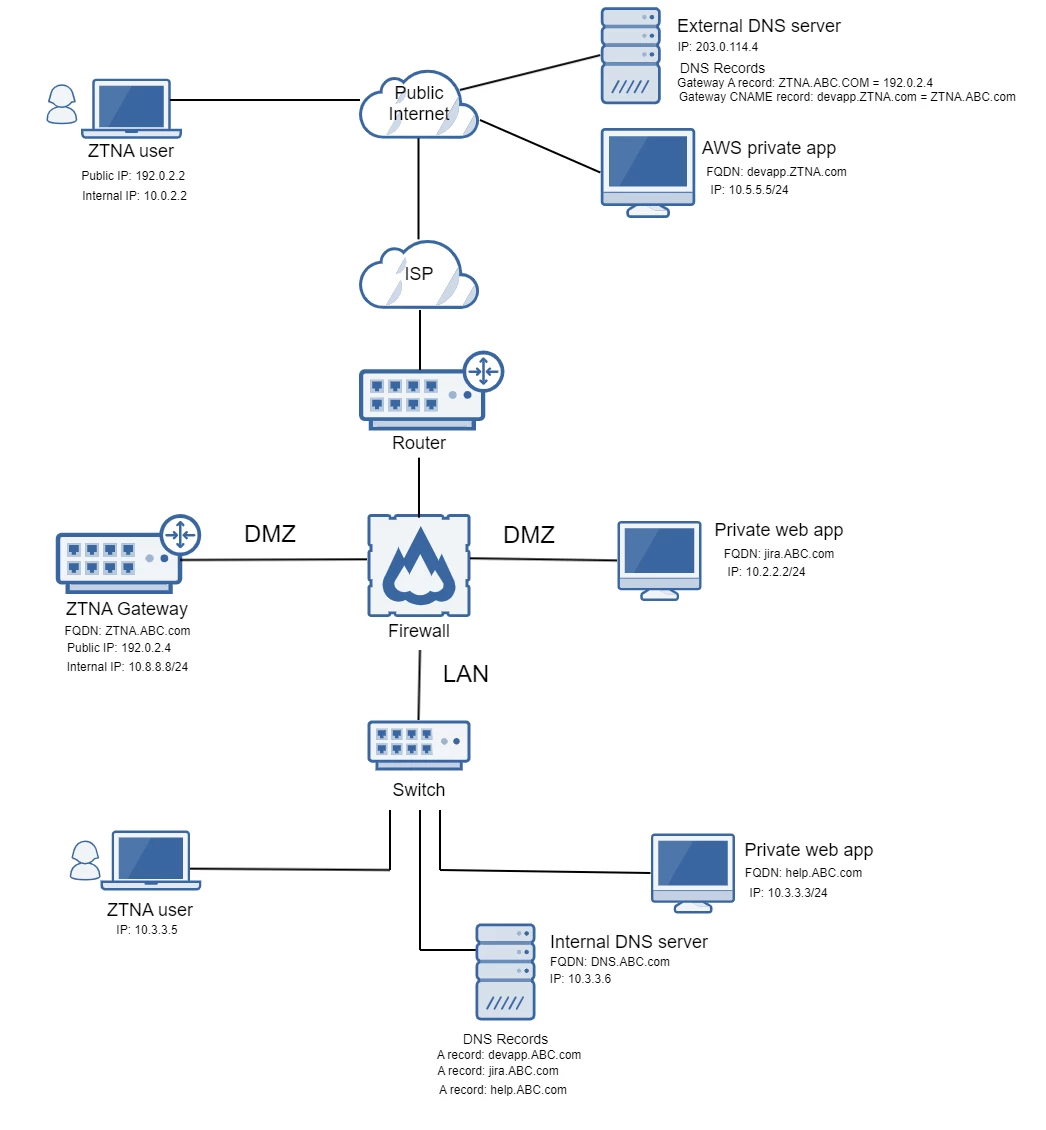
Network diagram
Here's an example network diagram. The following examples are based on this network setup.
Point users to the external DNS server
The simplest way to ensure that users go through ZTNA is to configure the users' devices to always point to the external DNS server's IP address.
This is what happens when the user attempts to access the internal resource:
- The user attempts to access an internal application,
help.ABC.com, through their browser. - The DNS request goes to the external DNS server,
203.0.114.4. - The external DNS server resolves the application,
help.ABC.com, to the ZTNA gateway,ZTNA.ABC.com. - The user connects to the ZTNA Gateway to access the internal application.
Add DNS records to your internal DNS server
If you want to point users to the internal DNS server's IP address, you must make sure the DNS server has the following DNS records:
- A CNAME record that points the external FQDN of the internal application to the FQDN of the ZTNA gateway. Example:
help.ABC.comresolves toZTNA.ABC.com. - If the application's internal and external FQDNs are the same, you must change the internal FQDN and update it in the resource settings in Sophos Central. For example, if the internal and external FQDNs are both
help.ABC.com, change the internal FQDN tohelp.in.ABC.com. For information about creating resource records, see Add resources.
This is what happens when a user attempts to access the internal resource:
- The user attempts to access an internal application,
help.ABC.com, through their browser. - The DNS request goes to the internal DNS server,
DNS.ABC.com. - The internal DNS server resolves the application,
help.ABC.com, to the ZTNA gateway,ZTNA.ABC.com. - The ZTNA gateway forwards the request to the application using its second A record entry,
help.in.ABC.com. This prevents a loop (help.ABC.comtoZTNA.ABC.comand then back tohelp.ABC.com). - The user connects to the ZTNA Gateway to access the internal application.
Use the ZTNA agent in the office
Users in the office normally access internal applications by FQDN, so their requests are sent to the internal DNS server.
However, when users have the ZTNA agent installed on their endpoint devices, the ZTNA agent intercepts the DNS request, which is sent to the ZTNA gateway.
IP-based access
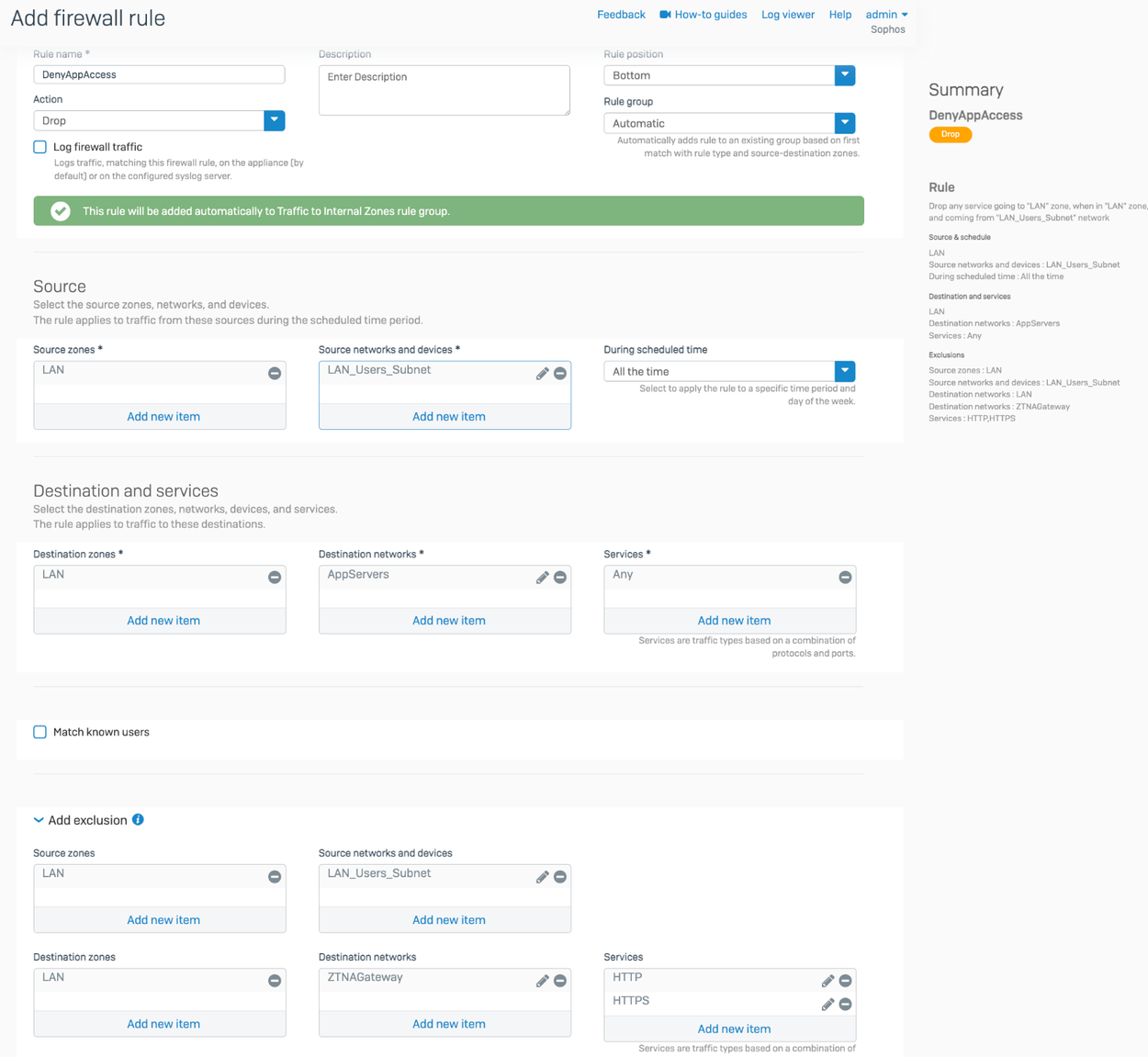
If a user attempts to access an internal resource by typing its IP address into the browser, the user goes directly to the resource, bypassing ZTNA. To ensure users access the internal resource by FQDN, you can add firewall rules.
Here's an example of a firewall rule configured on Sophos Firewall.
This rule allows users to access the ZTNA gateway from any zone and denies them access to any other application servers. This means they must go through ZTNA to access applications servers that host their resources.
This rule applies in agent and agentless cases when a user tries to access a resource directly using an IP address.