DNS flows
Here's an overview of how DNS works when you access an application using ZTNA. You can access an application with the ZTNA agent or through your browser.
Click the tab for your gateway deployment type below.
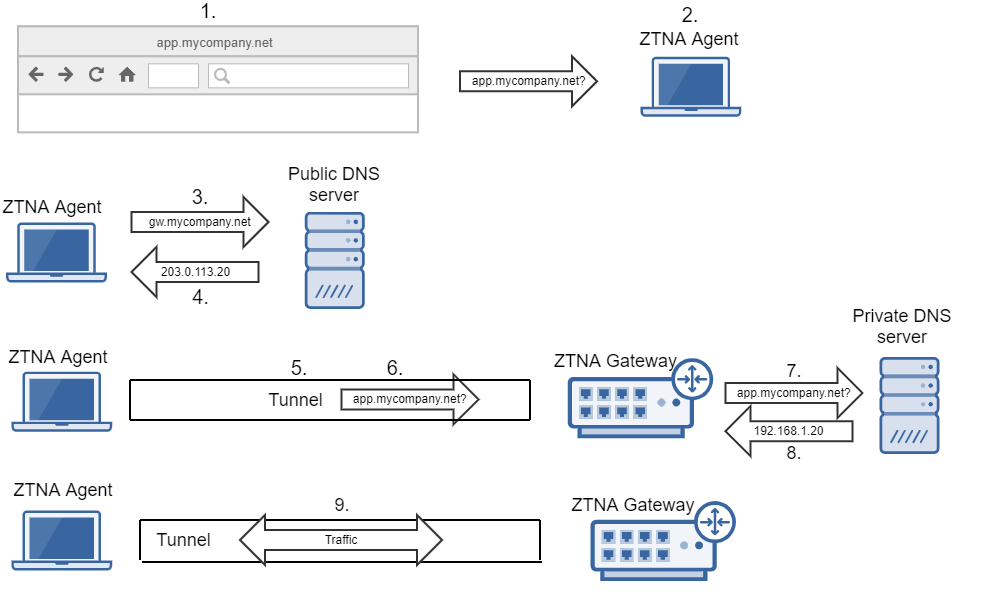
DNS flow with agent
-
The remote user attempts to access a private application,
app.mycompany.net, through their browser. -
The DNS request is intercepted and forwarded to the ZTNA agent.
Note
The ZTNA agent resolves the private application FQDN to the Carrier Grade Network Address Translation (CGN) network IP and also handles all the traffic destined for the private application's FQDN.
- As soon as the DNS request is intercepted, the ZTNA agent leases an IP address in the
100.64.x.xrange to the application. Example:100.64.0.4. - The browser sends a TCP-SYN packet to the application (IP address:
100.64.0.4). - The destination IP of the SYN packet is
100.64.0.4, which falls in the subnet range of the virtual adapter (100.64.x.x), so the SYN packet goes to the virtual adapter.
- As soon as the DNS request is intercepted, the ZTNA agent leases an IP address in the
-
The ZTNA agent sends a DNS request to the public DNS server for the ZTNA gateway's IP address. This is needed to establish the tunnel with the ZTNA gateway.
Note
The public DNS server has an A record entry for the ZTNA gateway that points to the gateway's IP.
-
The public DNS server sends the ZTNA gateway's IP address (
203.0.113.20) back to the ZTNA agent. -
Mutual TLS encryption is performed between the ZTNA agent and the ZTNA gateway, and a tunnel is established. All communication with the ZTNA gateway happens over the secure tunnel.
Note
ZTNA supports TLS 1.2 and later versions, using industry-standard encryption protocols with up to 256-bit key lengths for secure data transmission.
-
The agent sends the application traffic for
app.mycompany.netto the ZTNA gateway through the tunnel. -
The ZTNA gateway sends the DNS query for
app.mycompany.netto the private DNS server to find out where the specific application server IP is. -
The private DNS server returns the application server’s IP address (
192.168.1.20) and traffic is forwarded by the ZTNA gateway to the application server. -
The remote user can access the private application through the tunnel.
Note
The user can only access the private application after authentication and authorization, but they aren't included in this topic.
Note
Installing the ZTNA agent changes the default TAP adapter. If you use nslookup to do a DNS lookup, it now uses the ZTNA TAP adapter by default. Lookups of apps that aren't behind the ZTNA gateway will fail. You need to add the corresponding network adapter to your nslookup command. For example:
nslookup <FQDN-to-be-resolved><DNS-Server>
This applies to both on-premises and remote working scenarios.
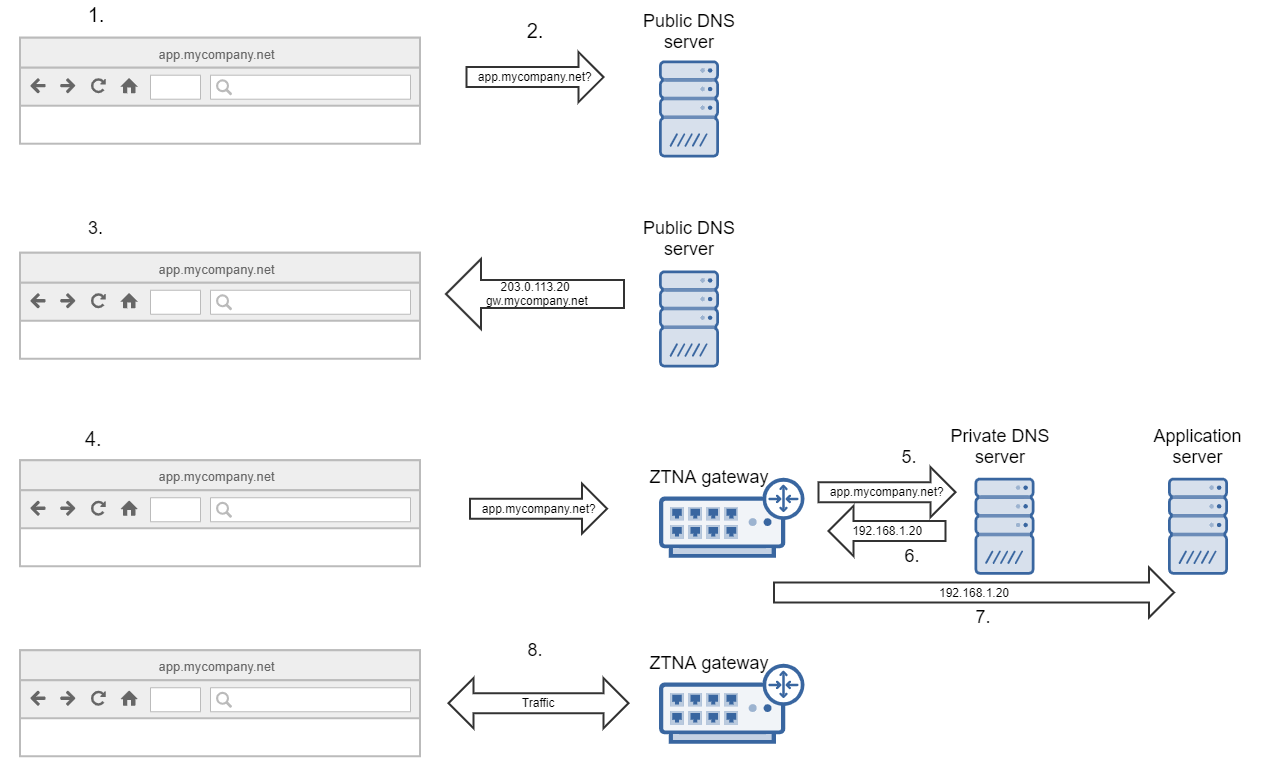
DNS agentless flow
-
The remote user attempts to access a private application,
app.mycompany.net, through their browser. -
The DNS request is sent from the remote user's browser to the public DNS server, which resolves the private application's name to the ZTNA gateway's name and IP address.
Note
The public DNS server has a CNAME record for the private application, which points to the FQDN of the ZTNA gateway. It also has an A record for the ZTNA gateway, which points to the gateway’s IP address.
-
The public DNS server sends the ZTNA gateway’s IP address (
203.0.113.20) back to the user's browser. -
A web request is then sent from the user's browser to the ZTNA gateway.
-
The ZTNA gateway sends the DNS request for
app.mycompany.netto the private DNS server. -
The private DNS server returns the IP address of app.mycompany.net (
192.168.1.20). -
The ZTNA gateway forwards the request (
app.mycompany.net) to the application server. -
The user can connect to the ZTNA Gateway to access the private application.
Note
The user can only access the private application after authentication and authorization, but they aren't included in this topic.
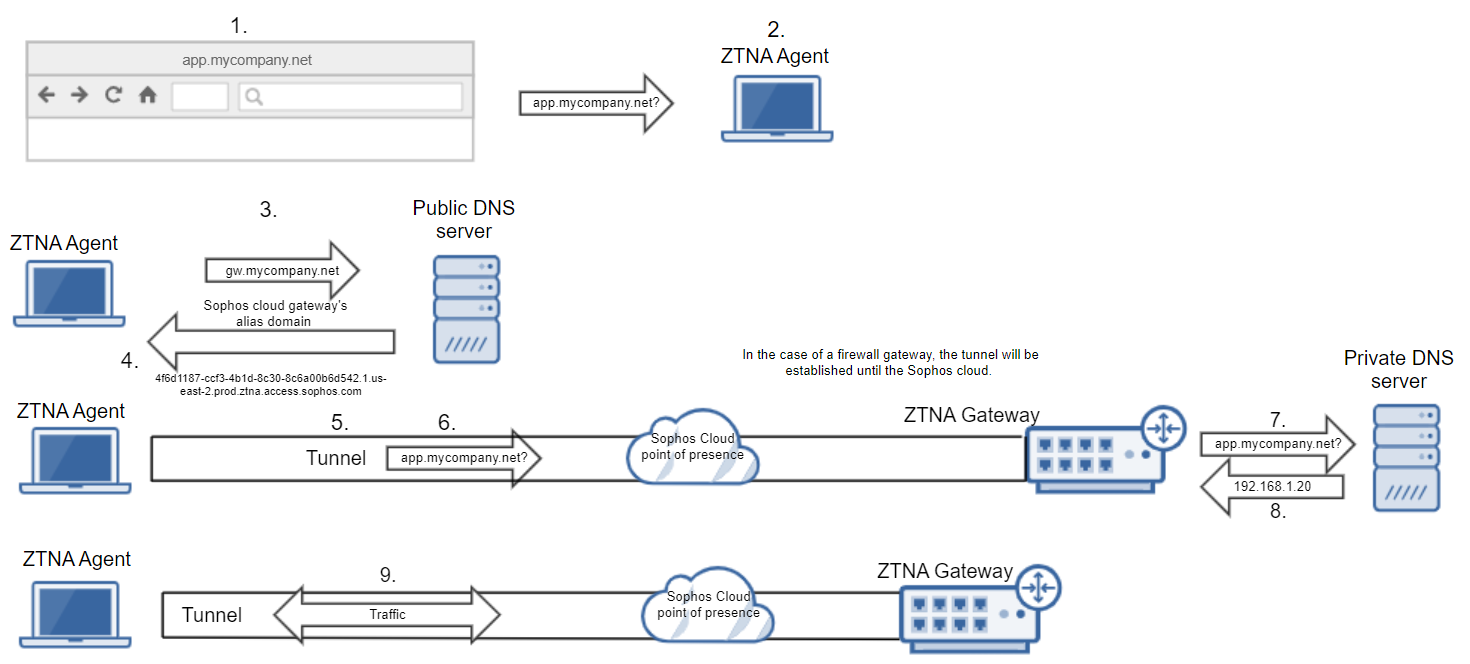
DNS flow with agent
-
The remote user attempts to access a private application,
app.mycompany.net, through their browser. -
The DNS request is intercepted and forwarded to the ZTNA agent.
Note
The ZTNA agent resolves the private application FQDN to the Carrier Grade Network Address Translation (CGN) network IP and also handles all the traffic destined for the private application's FQDN.
- As soon as the DNS request is intercepted, the ZTNA agent leases an IP address in the
100.64.x.xrange to the application. Example:100.64.0.4. - The browser sends a TCP-SYN packet to the application (IP address:
100.64.0.4). - The destination IP of the SYN packet is
100.64.0.4, which falls in the subnet range of the virtual adapter (100.64.x.x), so the SYN packet goes to the virtual adapter.
- As soon as the DNS request is intercepted, the ZTNA agent leases an IP address in the
-
The DNS request is sent from the ZTNA agent to the public DNS server.
-
The DNS server resolves the private application's name to the alias domain it's mapped to.
-
The alias domain redirects the DNS request from the remote user's browser to the Sophos Cloud point of presence, then on to the ZTNA gateway. Mutual TLS encryption is performed between the ZTNA agent and the ZTNA gateway, and a tunnel is established. All communication with the ZTNA gateway happens over the secure tunnel via the Sophos Cloud point of presence.
Note
ZTNA supports TLS 1.2 and later versions, using industry-standard encryption protocols with up to 256-bit key lengths for secure data transmission.
Note
If you have a Sophos Firewall gateway, all security checks, such as authentication and authorization are done in the Sophos Cloud, so the tunnel is established between the ZTNA Agent and the Sophos Cloud point of presence.
-
The agent sends the application traffic for
app.mycompany.netto the ZTNA gateway through the tunnel via the Sophos Cloud point of presence. -
The ZTNA gateway sends the DNS query for
app.mycompany.netto the private DNS server to find out where the specific application server IP is. -
The private DNS server returns the application server's IP address (
192.168.1.20) and traffic is forwarded by the ZTNA gateway to the application server via the Sophos Cloud point of presence. -
The remote user can access the private application through the tunnel.
Note
The user can only access the private application after authentication and authorization, but they aren't included in this topic.
Note
Installing the ZTNA agent changes the default TAP adapter. If you use nslookup to do a DNS lookup, it now uses the ZTNA TAP adapter by default. Lookups of apps that aren't behind the ZTNA gateway will fail. You need to add the corresponding network adapter to your nslookup command. For example:
nslookup <FQDN-to-be-resolved><DNS-Server>
This applies to both on-premises and remote working scenarios.
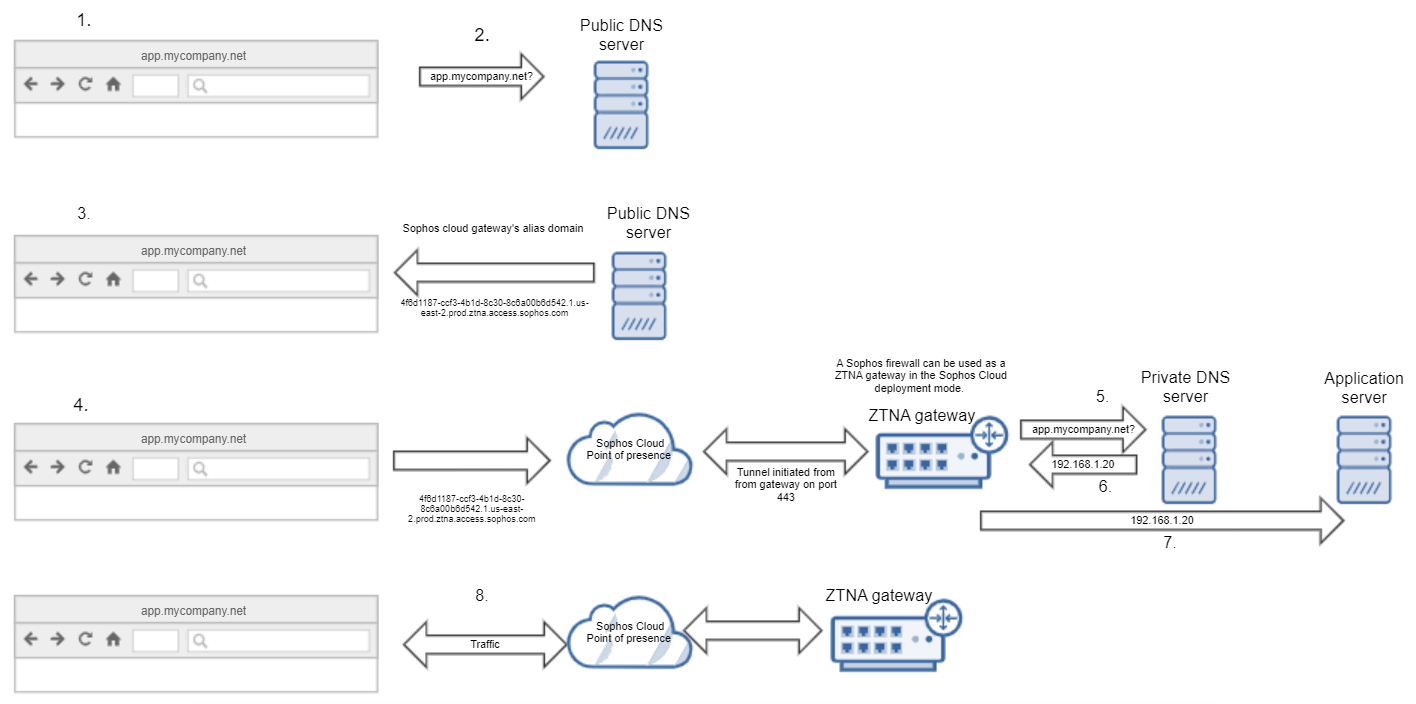
DNS agentless flow
-
The remote user attempts to access a private application,
app.mycompany.net, through their browser. -
The DNS request is sent from the remote user's browser to the public DNS server, which resolves the private application's name to the alias domain it's mapped to.
-
The public DNS server sends the resource's alias domain back to the user's browser.
-
The alias redirects the DNS request from the remote user's browser to the Sophos Cloud point of presence.
Note
When you add an agentless resource, a new tunnel is established between the ZTNA gateway and the Sophos Cloud point of presence. The tunnel is initiated from the ZTNA gateway on port 443. A new tunnel is established for each new resource.
-
The Sophos point of presence sends the DNS request through the tunnel to the relevant gateway using the information from the alias domain.
-
The ZTNA gateway sends the DNS request for
app.mycompany.netto the private DNS server. -
The private DNS server returns the IP address of app.mycompany.net (
192.168.1.20). -
The ZTNA gateway forwards the request (
app.mycompany.net) to the application server. -
The user can connect to the ZTNA Gateway via the Sophos Cloud point of presence to access the private application.
Note
The user can only access the private application after authentication and authorization, but they aren't included in this topic.