Requirements
Before you set up ZTNA, check that you meet all of the following requirements.
Wildcard certificate
You need a wildcard certificate for the ZTNA gateway. Use one of the following:
- A certificate issued from Let's Encrypt.
- A certificate issued by a trusted certificate authority.
Note
We support only RSA and ECDSA certificates with the below exceptions:
- ECDSA: P-384 and P-521 aren't supported.
- RSA: Key size less than 2048 isn't supported.
This guide tells you how to get a certificate. See Get a certificate.
Gateway host
You can host the ZTNA gateway on an ESXi or Hyper-V server or set up a Sophos Cloud gateway. See Add a gateway.
Note
If you're deploying multiple gateway nodes, make sure that the network in which they're connected has minimal latency.
Sophos Firewall
To integrate your Sophos Firewall with ZTNA, you must meet the following requirements:
- Your firewall must be on version 19.5 MR3 or later.
- Your firewall must be managed by Sophos Central.
You can integrate ZTNA with all types of firewalls: Hardware, cloud, virtual, and software.
ESXi server
If you host the gateway on an ESXi server, make sure the VMware vSphere hypervisor (ESXi) version is 6.5 or later.
For stable and reliable performance, make sure the system meets the following minimum specifications:
-
CPU: 2 cores
-
Memory: 4 GB RAM
-
Storage: 80 GB
Note
We recommend using SSDs for faster and more consistent disk I/O performance.
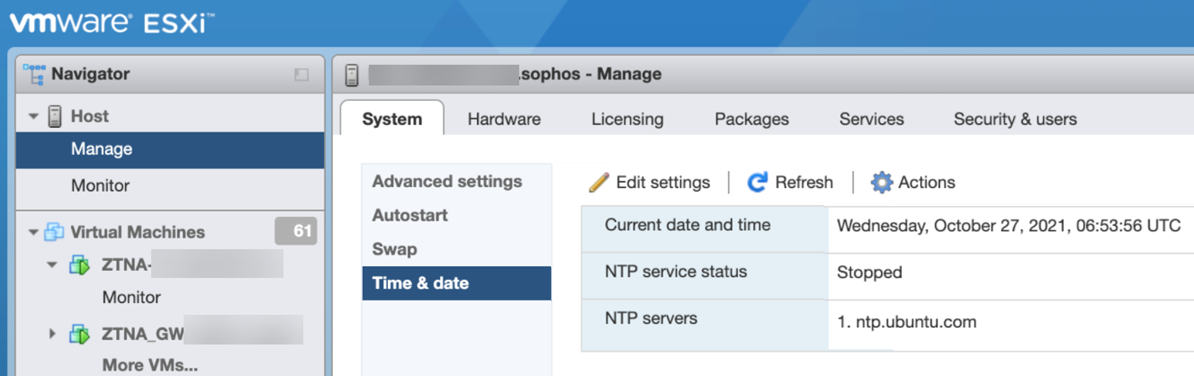
Make sure that the correct date and time are set. The ZTNA gateway synchronizes with the host's time and encounters issues if it isn't correct.
Note
You must set the time zone to UTC.
On your ESXi host, go to Manage > System > Time & date and click Edit settings to set the time.
Hyper-V server
If you host the gateway on a Hyper-V server, make sure the Hyper-V server is running on Windows Server 2016 or later.
For stable and reliable performance, make sure the system meets the following minimum specifications:
-
CPU: 2 cores
-
Memory: 4 GB RAM
-
Storage: 80 GB
Note
We recommend using SSDs for faster and more consistent disk I/O performance.
Make sure that the correct date and time are set. The ZTNA gateway synchronizes with the host's time and encounters issues if it isn't correct.
Note
You must set the time zone to UTC.
DNS management
You must configure your DNS server settings. See Add your DNS settings.
Directory service
You need a directory service to manage the user groups that ZTNA will use. You can use Microsoft Entra ID (Azure AD) or Active Directory. See Set up directory service.
Microsoft Entra ID (Azure AD)
You need a Microsoft Entra ID (Azure AD) account with user groups configured and synced with Sophos Central. This guide tells you how to set up and sync these groups. See Sync users in Sophos Central.
Your user groups must be security-enabled. Groups created in Microsoft Entra ID (Azure AD) are automatically security enabled, but groups created from the Microsoft 365 portal or imported from AD aren't.
You can also use Microsoft Entra ID (Azure AD) as your identity provider. See Set up an identity provider.
Active Directory
You need an Active Directory account with user groups configured and synced with Sophos Central. See Set up synchronization with Active Directory in the Sophos Central admin help.
You can also use Active Directory as your identity provider. See Set up an identity provider.
Identity provider
You need an identity provider to authenticate your users. You can use the following solutions:
- Microsoft Entra ID (Azure AD)
- Okta
- Active Directory (on-prem)
This guide tells you how to configure them for use with ZTNA. See Set up an identity provider.
Allowed websites
If the gateway is behind a firewall, you must give access to the required websites (on port 443, unless otherwise stated). In the list below, *.domain indicates that multiple levels of subdomains are allowed.
Note
This only applies to on-premises gateways.
The required websites are as follows:
sophos.jfrog.iojfrog-prod-use1-shared-virginia-main.s3.amazonaws.com*.amazonaws.comproduction.cloudflare.docker.com*.docker.io*.sophos.comlogin.microsoftonline.comgraph.microsoft.comztna.apu.sophos.com(Port 22)sentry.io*.okta.com(If you use Okta as an identity provider)wsserver-<customer gateway FQDN>- ZTNA gateway FQDN (the domain you configured in the ZTNA gateway settings)
Exclusions
Suppose SSL/TLS decryption is enabled on an upstream firewall. In that case, you must add the ZTNA gateway's external FQDN to the firewall's exclusion list in the following format: wsserver-<customer-gateway-fqdn>. For information, see Exceptions.
Supported app types
ZTNA can control access to both web-based and local apps. Control of local apps requires the ZTNA agent.
ZTNA doesn’t support apps that depend on dynamic port allocation or use a wide range of ports, for example older VOIP products.
For information about adding apps and web pages, see Add resources.
Sophos ZTNA agent
You can install the ZTNA agent on the following operating systems:
-
Windows 10.1803 or later
-
macOS BigSur (macOS11) or later
For more information, see Install the ZTNA agent.