Troubleshooting
Setup
Gateway on ESXi doesn't show as ready to approve
Issue
Gateway hosted on ESXi doesn't show an "Approve" button in Sophos Central after deployment.
What to do
-
Check whether your gateway can connect to the following URLs. If it can't, allow them. Use port 443 unless otherwise stated.
sophos.jfrog.io\*.amazonaws.comproduction.cloudflare.docker.com\*.docker.io\*.sophos.comlogin.microsoftonline.comgraph.microsoft.comztna.apu.sophos.com(Port 22)sentry.io\*.okta.com(If you use Okta as an identity provider)
-
Make sure that ESXi has the latest firmware version.
-
Make sure the ISO files are loaded.
Note
When you configure the ESXi server, you must turn off the option for automatic power-on (the default on ESXi) or prevent the ZTNA gateway from booting after you finish. If you don't, the gateway will boot without the ISO files and you'll have to start again.
-
Make sure that the time is set correctly to GMT on ESXi.
- Make sure that the CD-ROM is attached. If it isn't, power the VM off and reattach it. If that fails, recreate the gateway VM.
- Run a TCP probe on internal interface:6443 to make sure K3S is running.
- If your gateway is behind Sophos Firewall, sign in to the firewall, go to Diagnostics > Packet Capture and turn packet capturing on, or set up web filtering, to see which requests fail. You can also do this on a third-party firewall.
No user groups are available to be given access to resources
Issue
When you add a resource to ZTNA, there are no user groups that you can allow to access it.
What to do
Check that your directory service (Microsoft Entra ID (Azure AD) or Active Directory) has user groups and that they're synchronized in Sophos Central.
The certificates aren't shown on the 'Edit gateway' page
Issue
When you open the Edit gateway page, you don't see the certificates you uploaded when you added the gateway.
What to do
This is as designed. You can't view the current certificates there.
The domain name isn't validated when you create resources.
Issue
Creating ZTNA agentless resources fails. The message shown is: "Domain is not validated". This is because resources are added with the gateway FQDN name instead of the domain name.
What to do
When you create resources, use the domain name, not the gateway FQDN name. For example, use test123.local instead of ztna.test123.local.
Microsoft AD (on-prem) identity provider
The IdP connection test fails for an on-prem AD user, which means the user can't access resources.
Issue
If the on-prem AD user belongs only to the primary group on the AD server, the group verification on the ZTNA server fails, and the user can't access resources.
What to do
Add the user to other AD groups and configure these groups to access resources on ZTNA.
Primary AD server error. Reason: host unreachable. Check configuration.
Issue
The primary AD server and ZTNA gateway aren't connecting.
What to do
Check that your primary AD server is reachable from the ZTNA gateway and that you have configured its hostname, IP, and port correctly.
Primary AD server error. Reason: invalid admin credentials. Check configuration.
Issue
Your primary AD server settings aren't correct.
What to do
- Check your Bind DN and Bind password settings are correct.
- Check the LDAP port is TLS enabled. Normally, port 389 is used for making unsecured LDAP connections, and port 636 is used for making secured LDAP connections.
Primary AD server error. Reason: invalid user search configuration. Check configuration.
Issue
This error may be caused by a typo in the Base DN, misconfigured advanced settings, incorrect test settings, or incorrect primary AD server settings.
What to do
- Check your settings for User and User group are correct.
- Check that the user you tested with exists on the AD server.
- Check whether the email field for the user on the primary AD server contains a valid email address. If the email address entered for a user is blank or invalid, then the test connection fails.
- If you entered an email address for your user in advanced settings, test the connection with the email address rather than the username.
- Check that your primary AD server is reachable from the ZTNA gateway and that you have configured its hostname, IP, and port correctly.
- Make sure your users are members of another user group in addition to the primary user group on the primary AD server.
ZTNA Gateway <gateway_name> lost connection to <IDP_name_and_IP> IDP
Issue
The primary AD server health check fails when users attempt to access an app.
What to do
- Check the user exists on the AD server.
- If you used the advanced configuration default settings when you set up AD on-prem as your IdP, sign in with your username without adding the domain name.
Internal Server Error. Login error: host unreachable.
What to do
Check that your primary AD server is reachable from the ZTNA gateway and that you have configured its hostname, IP, and port correctly.
Internal Server Error. Login error: ldap.
What to do
Check your settings for User and User group are correct.
Internal Server Error. Login Error.
What to do
Check whether the mail, name, and ID values you set in the advanced configuration are also set on the AD server.
ZTNA Gateway <gateway_name> not able to send email OTP via AD Server <SMTP_server_name_and_port_number>
Issue
The ZTNA gateway can't connect to the SMTP server.
What to do
If you don't receive a confirmation code for MFA, check your SMTP server configuration.
ZTNA on endpoints
ZTNA is shown as 'Not Configured' on endpoints
Issue
When you open Sophos Endpoint on a device managed by Sophos Central, the Status page shows "Zero Trust Network Access: Not configured".
What to do
Go to Devices > Computers (or Servers). Check whether the ZTNA agent is installed on the device. If it's installed, you see a green checkmark. If it isn't, you see a plus sign. Click to install ZTNA.
ZTNA is shown with the warning 'Zero Trust Network Access: Error' on endpoints
Issue
When you open Sophos Endpoint on a device managed by Sophos Central, the Status page shows "Zero Trust Network Access: Error". This indicates that there's a connection problem.
What to do
-
Check that a ZTNA policy has been set up in Sophos Central.
-
Check that the gateway FQDN can be resolved.
-
Check whether Sophos TAP adapter configuration failed.
-
Turn off the IPv6 network interface on the agent. The tunnel will then be established.
User groups
User groups lose access
Issue
Users in an Microsoft Entra ID (Azure AD) user group that previously had access to an app can no longer access it.
Cause
If you change the name of an Microsoft Entra ID (Azure AD) user group that's been given access to an app, the Assigned User Groups list in ZTNA isn't updated to reflect the change. Users won't be able to access the app.
What to do
-
Go to Zero Trust Network Access > Resources & Access.
-
On the Resources & Access page, find the app and click it to edit its details.
-
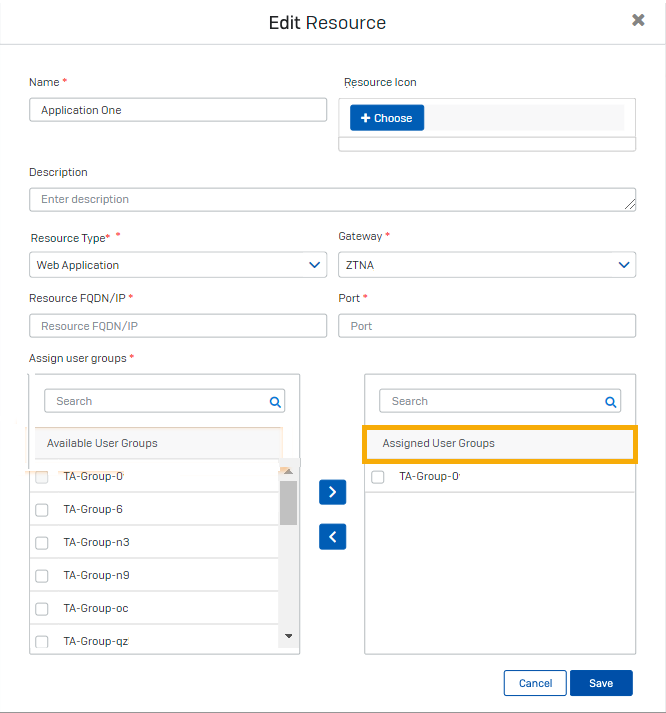
In the Edit Resource dialog, do as follows:
- Go to the Assign User Groups section.
- In Available User Groups, find the renamed user group and select the checkbox next to it.
- Move the group to Assigned User Groups and select the checkbox next to it.
- Click Save.
User's been added to an allowed user group but can't access the app
Issue
You've added a user to an allowed user group for an app but the user sees a 403 Access Denied error.
What to do
If the user's been added recently, ask them to try again later. Changes to user groups can take up to an hour to take effect.
Alternatively, if it's a web app, tell the user to go into Incognito or Private mode in their browser and then try again.
User's been removed from an allowed user group but can still access the app
Issue
You've removed the user from an allowed user group for an app but they can still access it.
What to do
Check again later. Changes to the allowed user group can take up to an hour to take effect.
Access issues
User sees a 404 Not Found error when they try to access an agentless app
Issue
When the user tries to access an app that's been set up for agentless access, they see a 404 Not Found error.
What to do
In your DNS management settings, do as follows:
-
Check that you have a CNAME record for the app that points to the gateway's FQDN.
-
Make sure you don't have a CNAME record for any app that's accessed via a ZTNA agent.
User sees a 403 Access Denied error when they try to access an agentless app
Issue
The user sees a 403 Access Denied error when they try to access an agentless app.
What to do
-
Check that you've enabled all the required API Permissions for your identity provider.
For Microsoft Entra ID (Azure AD), you need the following Microsoft Graph API permissions:
- Directory.Read.All (Delegated)
- Directory.Read.All (Application)
- Group.Read.All (Delegated)
- openID (Delegated)
- profile (Delegated)
- User.Read (Delegated)
- User.Read.All (Delegated)
Currently, you also need a Microsoft Entra ID (Azure AD) API permission: Directory.ReadWrite.All (Application).
For Okta:
- okta.groups.read
- okta.idps.read (You only need this if you use AD Sync)
-
Check that the ZTNA policy allows access to the app.
-
Check that the user is in an assigned user group for the app.
-
Check that you have network connectivity to the identity provider:
For Microsoft Entra ID (Azure AD):
login.microsoftonline.comgraph.microsoft.com
For Okta:
*.okta.com
-
The credentials configured on Microsoft Entra ID (Azure AD) may have expired. Check if the certificate or client secret is still valid.
User sees an upstream request error when they try to access an agentless app
Issue
User sees an upstream request error when they try to access an agentless app.
What to do
-
Check that the application is accessible from the network that the ZTNA gateway is on.
-
Check that the application is still running.
-
If the internal FQDN or IP address is shown, make sure it resolves to the app.
-
If you use a private DNS Server, check that it's running and resolves to the app's external FQDN.
-
Check that the port numbers specified for the app are correct.
User is authenticated but can't access an app that needs ZTNA agent
Issue
The user is authenticated but can't access an app.
What to do
-
Check the SNTP logs for errors.
-
Check the certificates are valid in heartbeat.xml.
User loses access to an app accessed via ZTNA agent
Issue
The user could previously access an app but can't do so anymore.
What to do
-
Check the SNTP logs for errors.
-
Check the certificates are valid in heartbeat.xml
-
Check whether ZTNA is shown with "red" health status in the Sophos Endpoint UI.
User doesn’t see the IDP sign-in screen the first time they try to access apps
Issue
The IDP should prompt the user to sign in the first time they try to access apps. If this doesn't happen, the user can't access apps.
What to do
Check that the user's device can contact the ZTNA gateway.
User doesn't see a sign-in popup when they try to access an app that needs the agent
Issue
The user should see a popup that prompts them to sign in when they try to access an app that needs the ZTNA agent. If they don't, they can't access the app.
What to do
-
Check the SNTP logs for errors.
-
Check the DNS settings. The DNS server must not have a CNAME record for the app.
-
Check the ZTNA agent process is running.
User can access an app but links in that app don't work
Issue
The user can access an app but links there to other apps don't work.
What to do
Add the other apps to ZTNA as described in Add resources. This lets ZTNA give the user access when they click on the links.
User is authenticated but isn't redirected to the app
Issue
The user sees the sign-in screen and is authenticated but isn't redirected to the app they tried to access.
What to do
-
Check that you specified the correct redirect URI in the identity provider (IdP) settings.
- If Microsoft Entra ID (Azure AD) is the IdP, you specified the Redirect URI when registering the ZTNA app. See Register the ZTNA app.
- If Okta is the IdP, you specified the Sign-in redirect URI when you created an app integration in Okta. See the Okta instructions in Set up an identity provider.
-
If Okta is the IdP, check that you entered the "Groups claim expression" with the correct capitalization. This expression is case-sensitive.
User sees a 403 Access Denied error when they try to access an internal resource
Issue
The user sees a 403 Access Denied error when they try to access an internal resource, for example, an internal webserver.
What to do
- Make sure the user is part of a user group mapped to the resource.
- Make sure the group configuration is correct in the directory service settings. For example, in Microsoft Entra ID (Azure AD), make sure that your imported user groups are security-enabled.
- Make sure you turn the ZTNA policy on in Sophos Central.
ZTNA users receive authentication prompts several times daily when the same user logs in from multiple devices simultaneously.
Issue
If the identity provider is on-premises Active Directory (AD), a user can only be authenticated on one device at a time.
When the same user logs in from multiple clients concurrently, the older session's access token is rewritten with a new access token. The users are logged out of the older sessions after the older access token expires (after one hour).
What to do
In this scenario, ZTNA users must authenticate again whenever they use a different device. This is expected behavior.
Users can't access resources, even after configuring the domain controller as a resource
Issue
The domain controller is defined as an agent-based resource, but users can't access resources behind it.
What to do
- Make sure the domain controller is added as an agent-based resource and the corresponding DNS-SRV records are updated with the domain name in advanced settings. See Domain controller as an agent-based resource.
- Add additional SRV records, if needed. Make sure you enter the port numbers.
- Make sure the domain controller can connect to the ZTNA gateway.
-
If user still can't access resources after the SRV records are added, do as follows:
- Use a packet capture tool, such as Wireshark, on the endpoint when attempting to access resources, and filter the packet using the following filter
dns.qry.type == 33. - Check the packet capture to verify whether the DNS SRV records have the same format as the records added in advanced settings.
- If the SRV records differ, edit the advanced settings, and add the DNS-SRV records in the correct format.
- Use a packet capture tool, such as Wireshark, on the endpoint when attempting to access resources, and filter the packet using the following filter
Users can't access resources when they disable and re-enable Sophos Central firewall management
Issue
After disabling and then re-enabling Sophos Central firewall management on Sophos Firewall, the connection to the ZTNA gateway isn't restored.
What to do
After re-enabling Sophos Central firewall management, edit the ZTNA gateway configuration in which the firewall was previously linked and select the firewall again.
Denied resource access report
This section describes reasons users are denied access to ZTNA resources, as shown in the Denied resource access report.
No Access
What to do
This issue occurs when a user isn't a member of a user group assigned to the ZTNA resource.
You can check the SNTP logs for errors.
The IT administrator must add the user to a user group that's assigned to the resource. If the user is already a member of the user group, make sure the user group has a security-enabled flag set in Microsoft Entra ID. See Microsoft Entra ID (Azure AD).
For Microsoft Entra ID, check you have the following Microsoft Graph API permissions:
- Directory.Read.All (Delegated)
- Directory.Read.All (Application)
- Group.Read.All (Delegated)
- openID (Delegated)
- profile (Delegated)
- User.Read (Delegated)
- User.Read.All (Delegated)
Currently, you also need a Microsoft Entra ID API permission: Directory.ReadWrite.All (Application).
Device Health
What to do
This issue occurs when a user tries to access a ZTNA resource from a device that doesn't meet the health status requirements defined in the ZTNA policy. The user must resolve the device health issues. See Computer Status.
Policy Off
What to do
This issue occurs when the ZTNA policy assigned to a resource is turned off by an administrator in Sophos Central. Go to My Products > ZTNA > Policies, click the policy name to open it, and make sure Policy is enforced is turned on.
ZTNA user portal
User can't see apps in the ZTNA user portal
Issue
The user can't see any apps in the ZTNA user portal.
Note
Currently the portal doesn't show apps that are accessed via the ZTNA agent. Users only see agentless apps.
What to do
-
Check that you've enabled all the required API Permissions for your identity provider.
For Microsoft Entra ID (Azure AD), you need the following Microsoft Graph API permissions:
- Directory.Read.All (Delegated)
- Directory.Read.All (Application)
- Group.Read.All (Delegated)
- openID (Delegated)
- profile (Delegated)
- User.Read (Delegated)
- User.Read.All (Delegated)
Currently, you also need a Microsoft Entra ID (Azure AD) API permission: Directory.ReadWrite.All (Application).
For Okta, you need the following permissions:
- okta.groups.read
- okta.idps.read (You only need this if you use AD Sync)
-
Ensure that your imported user groups are security-enabled.
-
Go to Resources & Access and click an app to edit its settings.
-
Check that the user is in assigned user groups for the apps they need. Users can only see apps that they are authorized to access.
-
Check that the admin selected Show resource in user portal when they added the apps.
User signs in but isn't given access to the ZTNA user portal
Issue
The user tries to access the ZTNA user portal and is shown the identity provider's sign-in screen. After they sign in, they're not returned to the user portal.
What to do
Check that you specified the correct redirect URI in the identity provider (IdP) settings.
If Microsoft Entra ID (Azure AD) is the IdP, you specified the Redirect URI when you registered the ZTNA app. See Set up directory service.
If Okta is the IdP, you specified the Sign-in redirect URI when you created an app integration in Okta. See the Okta instructions in Set up an identity provider.
DNS issues
DNS lookups fail after you install the ZTNA agent
Issue
After you install the ZTNA agent, if you use nslookup to do a DNS lookup, it sometimes fails.
What to do
Specify the network adapter for the lookup to use.
Installing the ZTNA agent changes the default TAP adapter. If you use nslookup to do a DNS lookup, it now uses the ZTNA TAP adapter by default. Lookups of apps that aren't behind the ZTNA gateway will fail.
To avoid this issue, add the correct adapter to your nslookup command. For example:
nslookup <FQDN-to-be-resolved><DNS-Server>
ZTNA diagnostics
This section describes the reasons a gateway may fail the diagnostic tests and the steps you can take to fix the issue.
Network diagnostics
Not able to read interface configuration
What to do
Verify that the ISO file downloaded from Sophos Central is attached.
Interface eth0 did not receive IP
What to do
Verify the network interface configuration. If you need to edit the gateway's network settings, create a new instance of the gateway on Sophos Central and download a new ISO file.
Interface eth1 did not receive IP
What to do
Verify the network interface configuration. If you need to edit the gateway's network settings, create a new instance of the gateway on Sophos Central and download a new ISO file.
DNS diagnostics
ZTNA Gateway could not resolve ntp.ubuntu.com
What to do
Check your DNS server configuration and make sure ntp.ubuntu.com can be resolved.
ZTNA Gateway could not resolve Sophos Central
What to do
Check your DNS server configuration and make sure sophos.jfrog.io can be resolved.
Network Connectivity diagnostics
Failed to contact ntp.ubuntu.com on port 123
What to do
Verify the network interface configuration. If ntp.ubuntu.com is unreachable, ZTNA services won't start.
Failed to contact sophos.jfrog.io on port 443
What to do
Make sure all the URLs mentioned in the ZTNA requirements are allowed: Allowed websites.
Sophos Services Diagnostics
Note
When you encounter errors in the Sophos services diagnostics, wait for 5-10 minutes then rerun the diagnostics. If the same error is encountered, restart the gateway. If the same error occurs after following both steps, contact Sophos support.
Kubernetes service is not running
What to do
It may take up to 10 minutes for the service to start after the gateway starts. Follow the steps below if the service doesn't start after 10 minutes.
Ensure the time on the gateway is synchronized with the time in Kubernetes. Also, ensure that the timezone is UTC.
Ensure the gateway can connect to the internet.
If you configure your gateway cluster in DHCP mode, ensure the IP addresses of your gateways haven't changed.
If the gateway platform is VMware ESXi, ensure the CD-ROM is attached to the VM instance when you start it.
Ensure at least half the nodes in your gateway cluster are active.
If the service still doesn't start, contact Sophos Support for help.
Redis Pod is not running
What to do
Contact Sophos Support for further help.
Cluster pods are not in running state
What to do
Contact Sophos Support for further help.
Gateway not registered with Sophos Central
What to do
Check connectivity to Sophos Central.
Failed to find Gateway details
What to do
Verify that the gateway has succesfully registered and check connectivity to Sophos Central.
Please wait for the Gateway to register and connect to Sophos Central
What to do
Approve the gateway on Sophos Central.
The gateway can't be managed by Sophos Central because services aren't running. Error: <cloud agent name>: crashloopback off <node number>: pending
What to do
Check the ISO that's mapped when booting up the gateway. Ensure the latest ISO is used and redeploy the gateway.
Unable to resolve Sophos Central FQDN
What to do
Verify that the firewall settings are updated to make sure that the dynamic URL displayed gets resolved.
Note
Dynamic URLs (For example: https://ztna-proxy.cloudstation.eu-west-1.prod.hydra.sophos.com) are generated based on the region where the user’s account is located. The dynamic URL is displayed in the gateway console’s error message.
Unable to connect to Sophos Central dynamic URL on port 443
What to do
Check connectivity to Sophos Central.
Note
Dynamic URLs (For example: https://ztna-proxy.cloudstation.eu-west-1.prod.hydra.sophos.com) are generated based on the region where the user’s account is located. The dynamic URL is displayed in the gateway console’s error message.
Time Diagnostics
Kubernetes Cluster time and Local time have a difference greater than 60 seconds
What to do
Verify the settings on the gateway platform. A time mismatch leads to connectivity issues.
NTP time and local time have a difference greater than 60 seconds
What to do
Verify the settings on the gateway platform. A time mismatch leads to connectivity issues.
Let's Encrypt
Internal Server Error
What to do
- Make sure the Let's Encrypt certificate is not generated for the same set of domains more than five times in one week.
-
Make sure you add CNAME entries for all of your domains on the DNS server.
If you attempt to generate a certificate but don't add a CNAME entry in the DNS server for one of your domains, the certificate renewal process will not work. Even if the certificate was previously generated, we will not renew it until CNAME entries for all domains have been added. Certificates can typically be generated for multiple domains; however, if even one domain is in a failed state due to a missing CNAME entry, the renewal will be skipped.
If you've attempted to generate the certificate incorrectly by not adding a CNAME entry on the DNS server, and have tried this more than five times within an hour, you'll get the internal server error.