Stop detecting an exploit
You can exclude an application from exploit detection, either in response to a detection or in advance of any detection.
Warning
Think carefully before you add exclusions because it reduces your protection.
You can set exclusions for a specific event, a specific exploit, or all exploits associated with an application.
If you want to exclude applications from exploit protection for some users or devices you can do this using an Endpoint Threat Protection policy, see Threat Protection Policy.
If you want to exclude applications from exploit protection for some servers you can do this using a Server Threat Protection policy, see Server Threat Protection Policy.
As adding exclusions reduces your protection, we recommend that you use policies to target users and devices where the exclusion is necessary rather than using the exclusion options that apply to all your users and their devices.
Stop detecting an exploit that's been detected (using events list)
If an exploit is detected on an application, but you're sure the detection is incorrect, you can stop it happening again using options available in your events list.
This applies to all your users and computers.
As adding exclusions reduces your protection, we recommend that you use policies to target users and devices where the exclusion is necessary rather than using this global option.
To stop detecting an exploit, do as follows:
- Go to My Environment > Computers & Servers.
- Find the computer where the detection happened and click it to view its details.
- On the Events tab, find the detection event, and click Details.
-
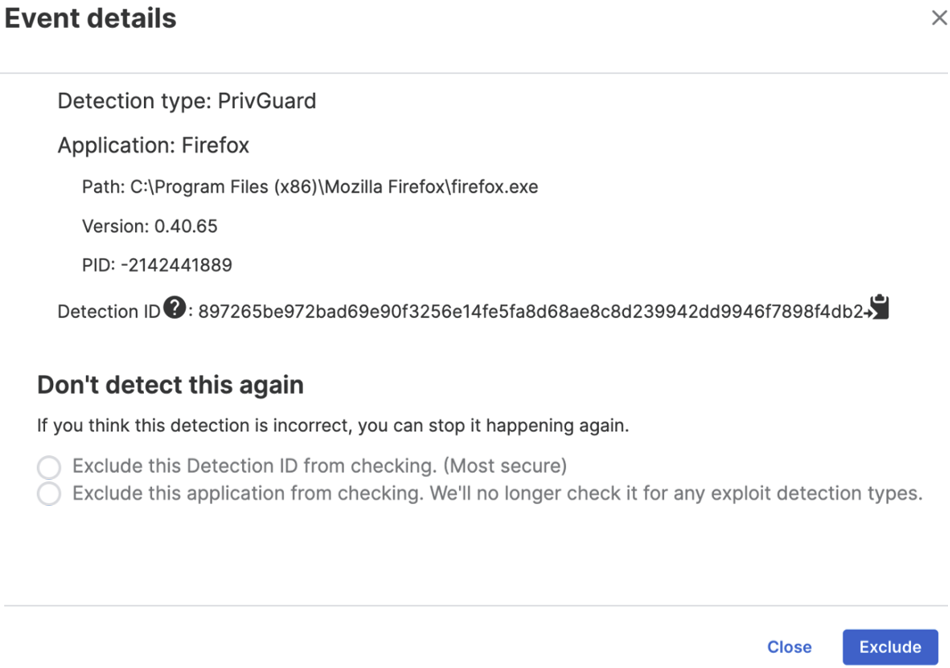
In Event details, under Don't detect this again, select one of the following options:
- Exclude this Detection ID from checking. prevents this detection on this application. It adds an exclusion for the Detection ID associated with this specific detection. If the same behavior occurs again on your estate, this doesn't trigger a detection. However, if the behavior is different, for example different paths or files, the Detection ID is different and requires a separate exclusion.
- Exclude this application from checking. prevents any checks for any exploits on this application. This carries the most risk, and therefore you should only use this as a last resort.
Note
We recommend you exclude the Detection ID first. If the same detection happens again, exclude the application.
-
Click Exclude.
We'll add your exclusion to a list.
Detection ID exclusions go into the Global Exclusions. Application exclusions go into the Exploit Mitigation Exclusions.
Stop detecting an exploit that's been detected (using policy settings)
If an exploit is detected on an application, but you're sure the detection is incorrect, you can stop it happening again by using options available in the threat protection policy.
You can also use a threat protection policy to exclude Windows applications from protection against security exploits.
Adding exclusions reduces your protection. We recommend that you use policies to add exploit mitigation exclusions because you can target them to specific users and devices. You can assign the policy only to those users and devices where the exclusion is necessary.
If you use a policy to stop detecting an exploit, we'll continue to check for other exploits that affect this application.
To stop detecting the exploit, do as follows:
- Go to My Products > Endpoint or Server.
- In Policies, find the Threat Protection policy that applies to the devices.
- Under Settings, find Exclusions and click Add Exclusion.
- In the Exclusion Type box, select Detected Exploits (Windows/Mac).
- Select the exploit and click Add.
- Check that the policy is assigned to the appropriate users and devices.
You can also use a policy to stop detecting exploits on all applications of a specific type. To do this, go to the threat protection policy and turn off exploit mitigation (which is under Runtime Protection) for that application type.
Warning
We don't recommend turning off exploit mitigation.
Stop checking for a specific exploit on an application
Suppose a detection has not occurred for an application, but it has been identified that the application needs to be excluded from a specific mitigation. In that case, you can proactively stop checking for a specific exploit.
If you use this method, we'll continue to check for other exploits that affect this application.
As adding exclusions reduces your protection, we recommend that you use policies to target users and devices where the exclusion is necessary rather than using this global option.
To stop checking for a specific exploit, do as follows:
- Click the General Settings icon
 .
. - Under General, click Global Exclusions.
- Click Add Exclusion.
- Under Exclusion Type, select Exploit Mitigation and Activity Monitoring (Windows).
-
In Exclude Application by Path, enter an application's file path to exclude it.
You can use wildcards and variables when you specify the file path. See Exploit mitigation or ransomware wildcards and variables.
-
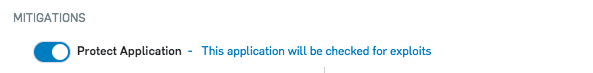
Under Mitigations, turn off the mitigation from which you want to exclude the application.
- Click Add, and then click Save.
Stop checking for all exploits on an application
If an application generates many unexpected exploit detections or suffers from performance issues when exploiting mitigation is turned on, you can stop checking for all exploits on the application.
If you use this method, we won't check the application for exploits but will still check it for ransomware behavior and for malware.
As adding exclusions reduces your protection, we recommend that you use policies to target users and devices where the exclusion is necessary rather than using this global option.
To stop checking for all exploits on an application, do as follows:
- Click the General Settings icon
 .
. - Under General, click Global Exclusions.
- Click Add Exclusion.
- Under Exclusion Type, select Exploit Mitigation and Activity Monitoring (Windows).
-
In Exclude Application by Path, enter an application's file path to exclude it.
You can use wildcards and variables when you specify the file path. See Exploit mitigation or ransomware wildcards and variables.
-
Under Mitigations, turn off Protect Application.
-
Click Add, and then click Save.