Removal of inactive devices
You must be an Admin or Super Admin to use this feature.
You can configure Sophos Central to remove devices automatically if they've been inactive for a specified time.
Removing devices means they'll no longer be listed on the Computers and servers page and won't be managed by Sophos Central.
Removal doesn't delete Sophos software from the devices. You can do that before removal or afterward. If you do it after removal, you need a password. See Delete Sophos software left on devices.
Note
Deleting and removing Windows devices removes all active Sophos software. For more information, see Deleted and expired devices.
You might need to remove devices because they're not used anymore, because users have left the organization, or because you've set up devices for testing only.
You set up automatic removal separately for endpoint computers and servers. The instructions here apply for both.
About removal rules
You can set up two kinds of removal rule:
- Targeted rules: Rules that remove inactive devices in selected groups.
- Global rule: The rule that removes all inactive devices, except devices you exclude.
You can use both kinds of rule, but configure them to run after different periods of inactivity. Doing this lets you use them for different purposes. For example, you could do as follows:
- Use a targeted rule to remove devices in a test group after 14 days.
- Use the global rule to clean up all devices on the network that haven't been used for 180 days.
Remove inactive devices in selected groups
Set up targeted rules for automatic removal of devices in groups you select.
You can set up two targeted rules. For example, one rule to remove virtual desktops after a few days, and another rule to remove other devices after a month.
To set up a rule, do as follows:
- Click the General Settings icon
 .
. - Under Endpoint Protection or Server Protection, click Removal of Inactive Devices.
-
Go to Removal rules and click Add.
-
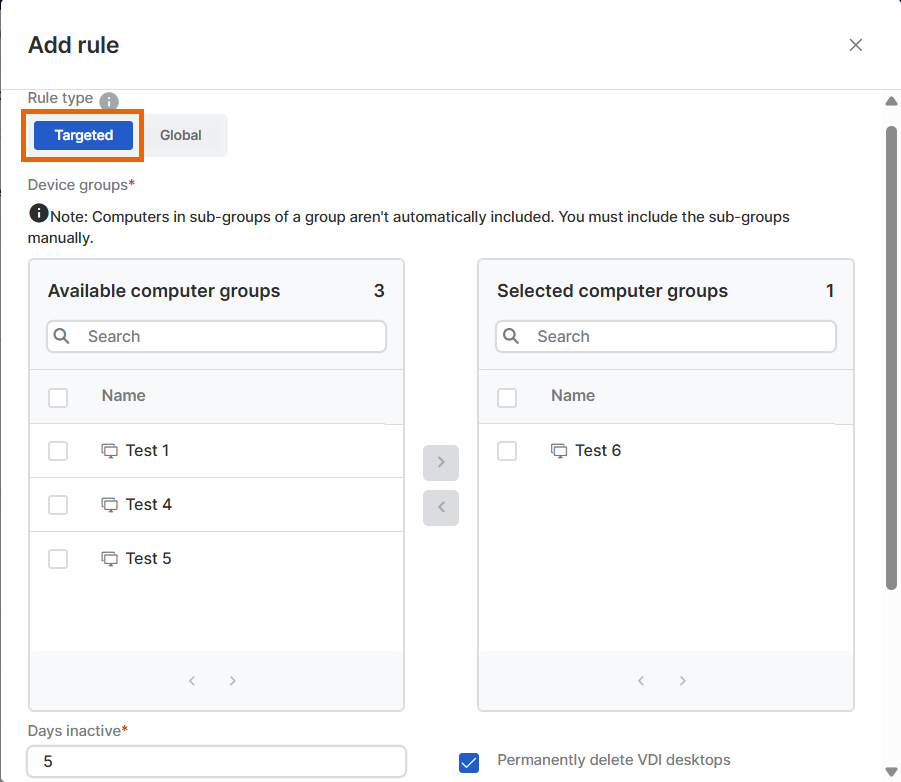
In Add rule, do as follows:
-
In Rule type, click Targeted.
-
In Device groups, find available groups where you want to apply the rule and move them to the list of selected groups.
-
In Days inactive, enter the number of days that devices must be inactive before we remove them.
If you're an MSP or Marketplace customer, you must enter 31 days or more.
-
(Optional) Select Permanently remove VDI desktops to remove virtual desktops. You can't restore them later.
If you cloned devices from a gold image installed using the
--nonpersistentparameter, this setting lets Sophos Central remove them. See Gold image nonpersistent. -
(Optional) In Comments, add comments. For example, add reminders of why you selected these settings.
-
-
Click Add.
We'll now check for inactive computers every 24 hours, at midnight, for the data region your account uses. We'll remove all that match your settings the same night, if possible.
Remove all inactive devices
Set up a global rule for removal of all inactive devices.
Before you start, consider whether there are devices you don't want to remove. For example, you might have devices used as an update cache or message relay. You can exclude devices from removal. See Exclude devices from removal.
To set up the global rule, do as follows:
- Click the General Settings icon
 .
. - Under Endpoint Protection or Server Protection, click Removal of Inactive Devices.
-
Go to Removal rules and click Add.
-
In Add rule, do as follows:
-
In Rule type, click Global.
-
In Days inactive, enter the number of days that devices must be inactive before we remove them.
You must select a number of days that is greater than the number of days for your targeted rules. Otherwise, the targeted rules will never be triggered.
If you're an MSP or Marketplace customer, you must enter 31 days or more.
-
(Optional) Select Permanently remove VDI desktops to remove virtual desktops. You can't restore them later.
If you cloned devices from a gold image installed using the
--nonpersistentparameter, this setting lets Sophos Central remove them. See Gold image nonpersistent. -
(Optional) In Comments, add comments. For example, add reminders of why you selected these settings.
-
-
Click Add.
We'll now check for inactive computers every 24 hours at midnight for the data region your account uses. We'll remove all devices that match your settings the same night, if possible.
Exclude devices from removal
You can exclude devices from your global rule.
You can't exclude devices from removal by your targeted rules.
If you have devices that you don't want to remove, put them in a special group or groups and exclude those groups.
Excluding a group doesn't automatically exclude its sub-groups. You must exclude sub-groups manually.
You can exclude up to four groups. Sub-groups count towards the maximum of four.
To exclude a group, do as follows:
- On the Removal of Inactive Devices page, make sure you've set up and turned on the Global rule.
- Go to Exclusions.
-
Click Add exclusion.
-
Find the group in the list of available groups and move it to the list of selected groups.
-
Click Add.
Check which devices were removed
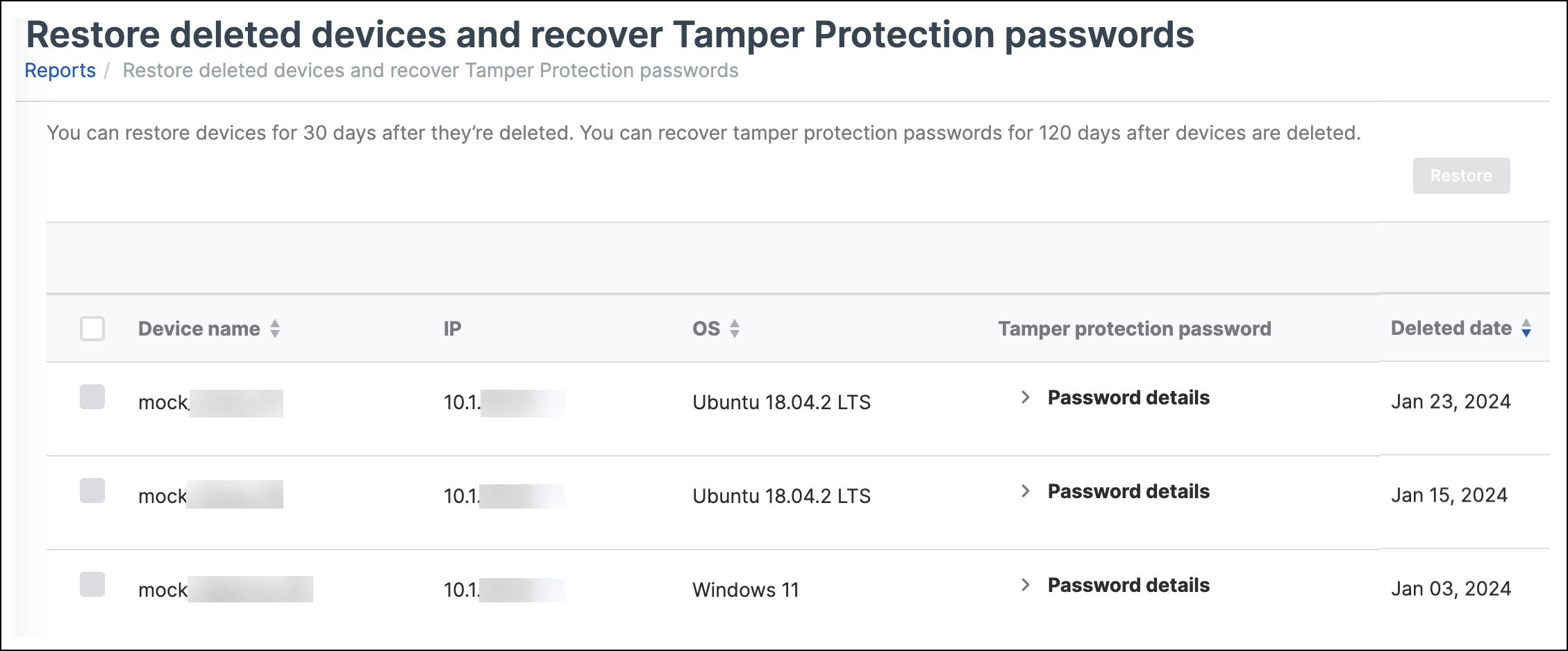
To see devices that were removed, go to Reports > Reports > Endpoint & Server Protection and click Restore deleted devices and recover Tamper Protection passwords.
The list shows devices removed automatically, as well as devices removed by admins.
Devices stay in the list for 120 days. You can restore them for the first 30 days.
Delete Sophos software left on devices
To delete Sophos software you've left on removed devices, you need the Tamper Protection password for each device. You can recover the password for 120 days after removal.
Note
You don't need to recover Tamper Protection passwords to uninstall Sophos software on Windows 10 and later, or Windows Server 2016 and later devices. This also applies to deleted devices and devices with expired licenses. For more information, see Deleted and expired devices.
To recover the password, do as follows:
- Go to Reports > Reports > Endpoint & Server Protection and click Restore deleted devices and recover Tamper Protection passwords.
- Find the devices.
- In the Tamper Protection password column, click Password details to see the password.
Restore removed devices
You can restore devices for up to 30 days after removal.
Note
This feature doesn't restore update caches or message relays that were on the devices. You can reinstall them after you restore the devices.
To restore devices, do as follows:
- Go to Reports > Endpoint & Server Protection > Restore deleted devices and recover Tamper Protection passwords.
- Select the devices and click Restore.