Use Microsoft Entra ID as an identity provider
You can use your Microsoft Entra ID instance to verify the identities of your administrators and users when they sign in to Sophos Central products. You need to add Microsoft Entra ID as an identity provider to do this.
If you want to use Microsoft Entra ID as an identity provider, find your Tenant ID for your Microsoft Entra ID instance. We need this to verify your users and administrators.
Requirements
You must verify a domain first. See Verify a federated domain.
You must be a Super Admin.
Warning
If you want to use federated sign-in as your sign-in option, you must ensure that all your administrators and users are assigned to a domain and have an identity provider.
You must do the following before you can add Microsoft Entra ID as an identity provider:
- Ensure you have a Microsoft Entra ID account with Microsoft. Microsoft Entra ID is Microsoft’s cloud-based identity and access management service.
- Get consent and authorization from your Microsoft Entra ID admin to use your organization's Microsoft Entra ID with Sophos Central.
- Ensure you have a Sophos Central account that matches your Microsoft Entra ID account (the emails must match).
Set up Microsoft Entra ID in the Azure portal
To set up Microsoft Entra ID in the Azure portal, you must do as follows:
- Create an Azure application.
- Set up authentication for the application.
- Set up token configuration.
- Assign application permissions.
Create an Azure application
To create an Azure application, do as follows:
- Sign in to your Azure portal.
- Search for
App registrations. -
In the left pane, click App registrations.
-
In the right pane, click New registration.
-
Enter a name for the application.
-
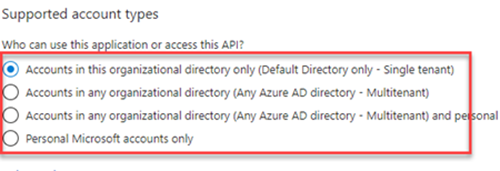
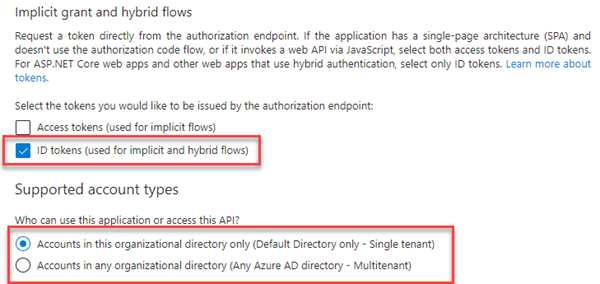
Under Supported account types, select Accounts in this organizational directory only (Default Directory only - Single tenant).
-
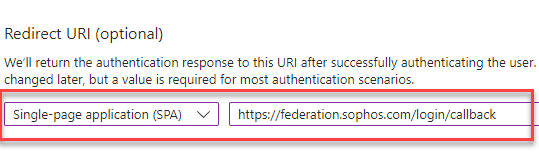
Under Redirect URI (optional), select Single-page application (SPA) and enter
https://federation.sophos.com/login/callback. -
Click Register.
Set up authentication for the application
To set up authentication for the application, do as follows:
- In the application you created, click Authentication.
- Under Implicit grant and hybrid flows, select ID tokens (used for implicit and hybrid flows).
- Under Supported account types, select Accounts in this organizational directory only (Default Directory only - Single tenant).
-
Click Save.
Set up token configuration
To set up token configuration, do as follows:
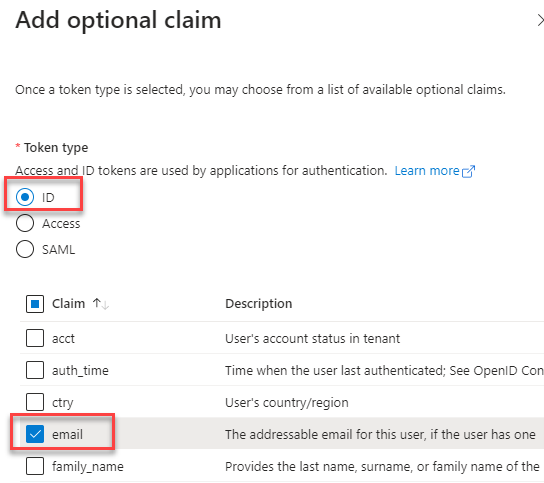
- In the application you created, click Token configuration.
- Under Optional claims, click Add optional claim.
-
Under Token type, select ID and then select email.
-
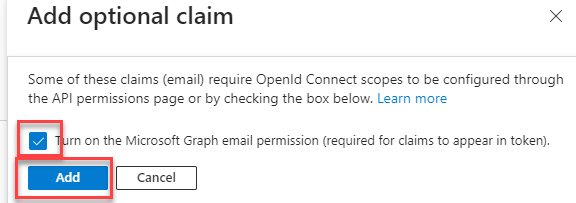
Click Add.
-
In the pop-message, click Turn on the Microsoft Graph email permission.
-
Click Add.
Assign application permissions
To assign application permissions, do as follows:
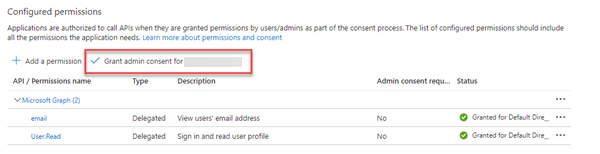
- In the application you created, click API permissions.
-
Under Configured permissions, click Grant admin consent for <account>.
-
Click Yes.
Microsoft Entra ID consent
A Microsoft Entra ID administrator must grant consent (permission) to use the credentials stored in your organization's Microsoft Entra ID tenant to sign in to Sophos Central.
This consent applies to all Sophos Central products.
When a Microsoft Entra ID administrator gives consent, it means your Microsoft Entra ID tenant trusts Sophos Central, and you can add Microsoft Entra ID as your identity provider.
For help with granting consent in Microsoft Entra ID, see Understanding Microsoft Entra ID application consent experiences.
Find your Tenant ID
You need to know the Tenant ID before you can add Microsoft Entra ID as an identity provider.
To find your Tenant ID, do as follows:
- From the Microsoft Azure portal menu, select Microsoft Entra ID. The Overview page appears.
-
In the Basic information section, find your Tenant ID. This is the ID for your tenant domain.
You'll need to enter it when you set up Microsoft Entra ID as an identity provider.
To add Microsoft Entra ID as an identity provider, see the following topics:
- If your users' email address and UPN are the same, see Add the identity provider (Entra ID/Open IDC/ADFS).
- If your users' email address and UPN are different, see Configure Microsoft Entra ID to allow users to sign in using UPN.
Set up Microsoft Entra ID as an identity provider in Sophos Central
You can use Microsoft Entra ID as an identity provider.
To do this, do as follows:
-
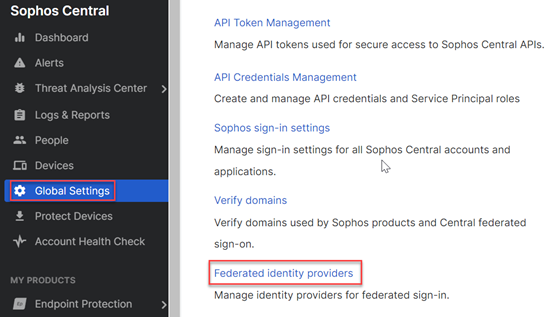
In Sophos Central, go to Global Settings > Federated identity providers.
-
Click Add identity provider.
- Enter a Name and Description.
- Click Type and choose OpenID Connect.
- Click Vendor and choose Microsoft Entra ID.
- Skip Step A: Setup OpenID Connect because you've already set up Microsoft Entra ID in the Azure portal.
-
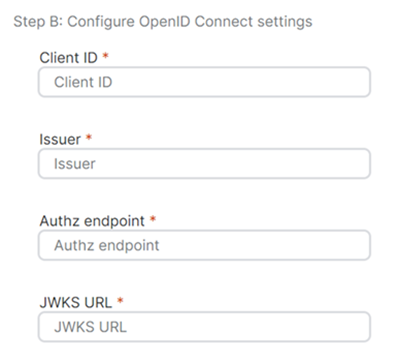
For Step B: Configure OpenID Connect settings, do as follows:
-
For Client ID, enter the client ID of the application you created in Azure.
To find this, do as follows:
- In the Azure portal, go to App registrations.
- Select the application you created.
- Copy the ID in Application (client) ID and paste it in Client ID in Sophos Central.
-
For Issuer, enter the following URL:
https://login.microsoftonline.com/<tenantId>/v2.0Replace
<tenantId>with the tenant ID of your Azure instance.To find this, do as follows:
- In the Azure portal, go to App registrations.
- Select the application you created.
- Copy the ID in Directory (tenant) ID and replace
<tenantId>with it in the URL.
-
For Authz endpoint, enter the following URL:
https://login.microsoftonline.com/<tenantId>/oauth2/v2.0/authorizeReplace
<tenantId>with the tenant ID you copied in step b. -
For JWKS URL, enter the following URL:
https://login.microsoftonline.com/<tenantId>/discovery/v2.0/keysReplace
<tenantId>with the tenant ID you copied in step b.
-
-
Click Select a domain and choose your domain.
You can add more than one domain. You can only associate a user with one domain.
-
Select whether you want to turn on IDP-enforced MFA. Select one of the following:
- IdP enforced MFA
- No IdP enforced MFA
-
Click Save.
You can now add Microsoft Entra ID as an identity provider. See Add the identity provider (Entra ID/Open IDC/ADFS).
Configure Microsoft Entra ID to allow users to sign in using UPN
You can configure Microsoft Entra ID to allow users to sign in using their User Principal Name (UPN) if it's different from their email address.
To sign in using your UPN, do as follows:
-
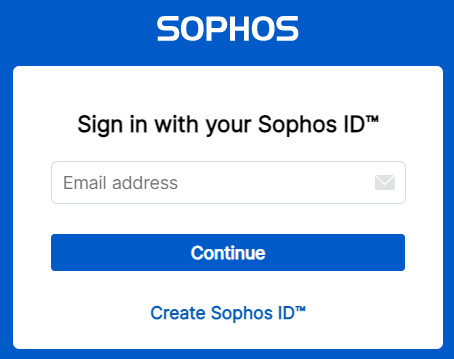
Users and administrators sign in with their associated email address in Sophos Central.
-
They see a screen depending on the selections in Sophos sign-in settings.
-
If you selected Sophos Central Admin or Federated credentials in My Products > General Settings > Sophos sign-in settings, users and administrators can sign in with either option.
To sign in using UPN, they must do as follows:
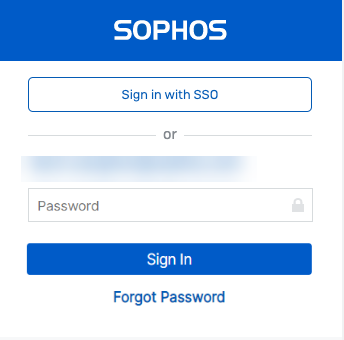
-
Click Sign in with SSO.
They're shown the Microsoft Azure sign-in page.
-
Enter the UPN and password.
-
-
If you've chosen Federated credentials only in My Products > General Settings > Sophos sign-in settings, they're shown the Microsoft Azure sign-in page where they can enter the UPN and password.
-