Add the identity provider (Entra ID/Open IDC/ADFS)
You need to set up an identity provider to use federated sign-in.
Requirements
You must be a Super Admin to use this feature.
-
You must verify a domain first. You can't set up an identity provider if you haven't verified a domain. See Verify a federated domain.
-
Check that you have the information needed to set up your identity provider.
Warning
If you want to use federated sign-in as your sign-in option, you must ensure that all your administrators and users are assigned to a domain and have an identity provider.
You can select Microsoft Entra ID, OpenID Connect, or Microsoft AD FS as your identity provider to verify the identities of your administrators when they sign in. Refer to the following sections for the instructions on configuring your chosen identity provider.
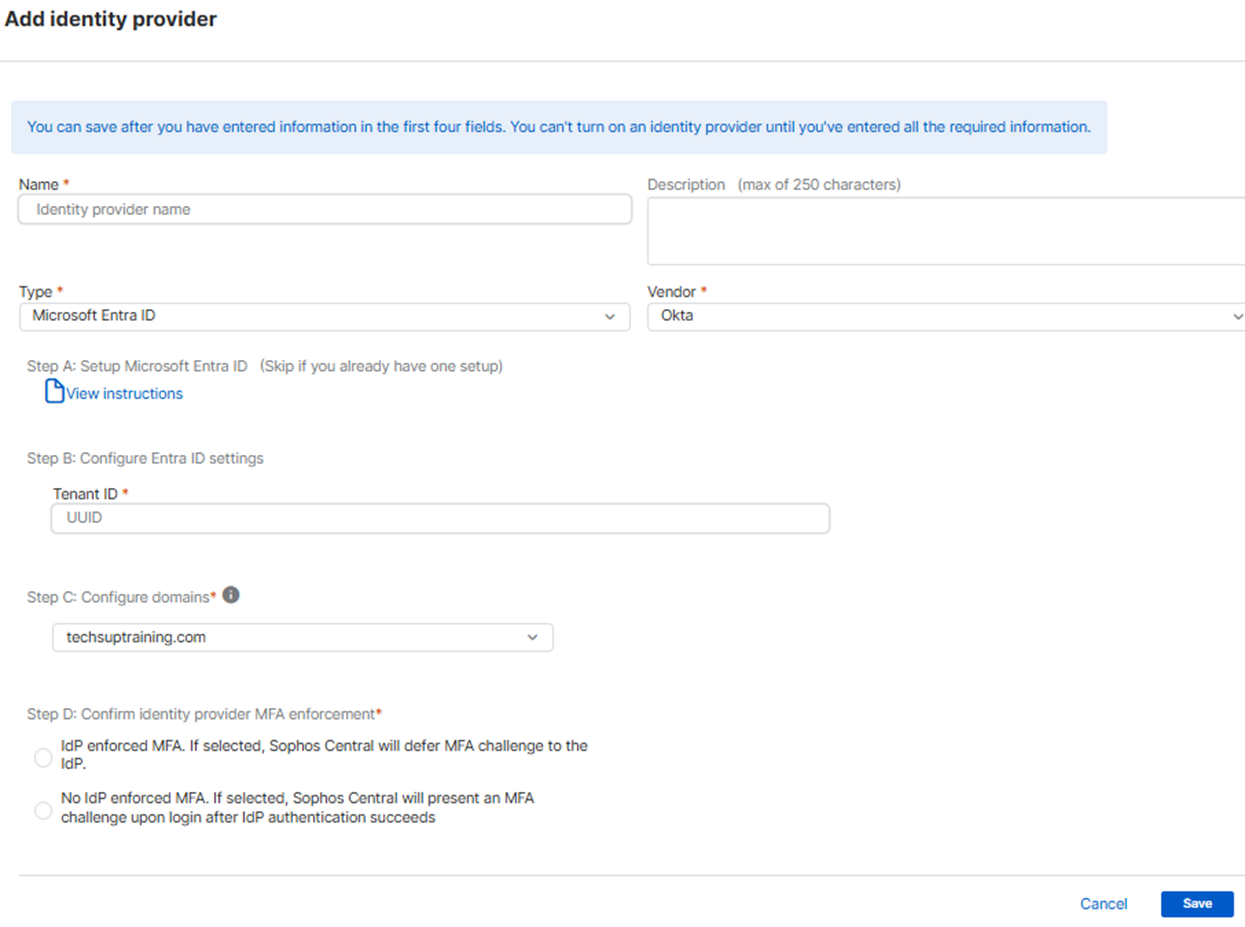
Add Microsoft Entra ID as an identity provider
You can add Microsoft Entra ID as an identity provider.
Before you add Microsoft Entra ID as an identity provider, you must follow the instructions in Use Microsoft Entra ID as an identity provider.
You must have a record of the Tenant ID for your Microsoft Entra ID instance.
To add Microsoft Entra ID, do as follows:
- Click the General Settings icon
 .
. - Under Administration, click Federated identity providers.
- Click Add identity provider.
- Enter a name and description.
- Click Type and select Microsoft Entra ID.
- Click Vendor and select Microsoft Entra ID.
- In Configure Entra ID settings, enter your tenant ID.
-
In Configure domains, click Select a domain and select your domain.
You can add multiple domains, but each user can only be associated with a single domain.
-
In Confirm identity provider MFA enforcement, select one of the following options:
- IdP enforced MFA: Sophos Central allows the identity provider (IdP) to enforce multi-factor authentication (MFA).
- No IdP enforced MFA: Sophos Central enforces MFA after IdP authentication is successful.
-
Click Save.
-
In Federated identity providers, select your identity provider and click Turn on.
Note
You can't turn on your provider if you haven't finished setting it up or if you've given invalid information.
You can now set up your sign-in settings. See Sophos sign-in settings.
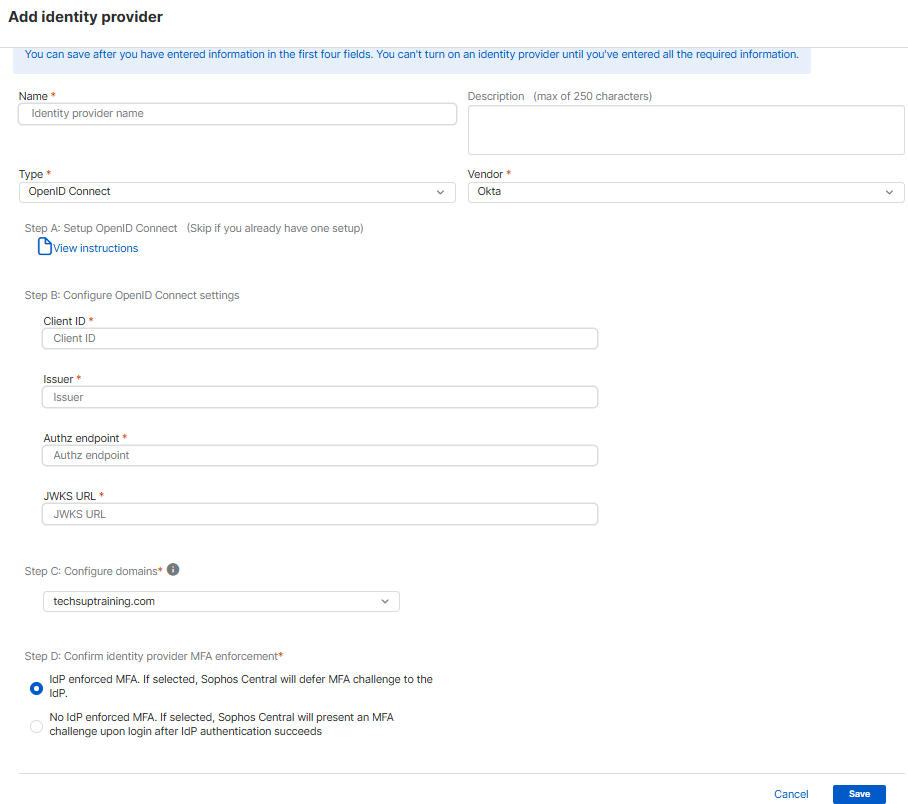
Add Open ID Connect as an identity provider
You can add Open ID Connect as an identity provider.
Before you add Open ID Connect as an identity provider, you must follow the appropriate instructions in Use OpenID Connect as an identity provider.
We've used Okta as our example Open ID Connect provider in the images in these instructions.
To add Open ID Connect, do as follows:
- Click the General Settings icon
 .
. - Under Administration, click Federated identity providers.
- Click Add identity provider.
- Enter a name and description.
- Click Type and select Open ID Connect.
- Click Vendor and select your vendor. For example, Okta.
-
In Configure OpenID Connect settings, enter the following information:
- Client ID: This is the Client ID for your Sophos Central application in Okta.
- Issuer: This is your Configured Custom Domain in Okta. It is
https://${DOMAIN}.okta.com. - Authz endpoint: This is
https://$Issuer}/oauth2/v1/authorize. - JWKS URL: This is
https://${Issuer}/oauth2/v1/keys.
-
In Configure domains, click Select a domain and select your domain.
You can add multiple domains, but each user can only be associated with a single domain.
-
In Confirm identity provider MFA enforcement, select one of the following options:
- IdP enforced MFA: Sophos Central allows the identity provider (IdP) to enforce multi-factor authentication (MFA).
- No IdP enforced MFA: Sophos Central enforces MFA after the IdP authentication is successful.
-
Click Save.
-
In Federated identity providers, select your identity provider and click Turn on.
Note
You can't turn on your provider if you haven't finished setting it up or if you've given invalid information.
You can now set up your sign-in settings. See Sophos sign-in settings.
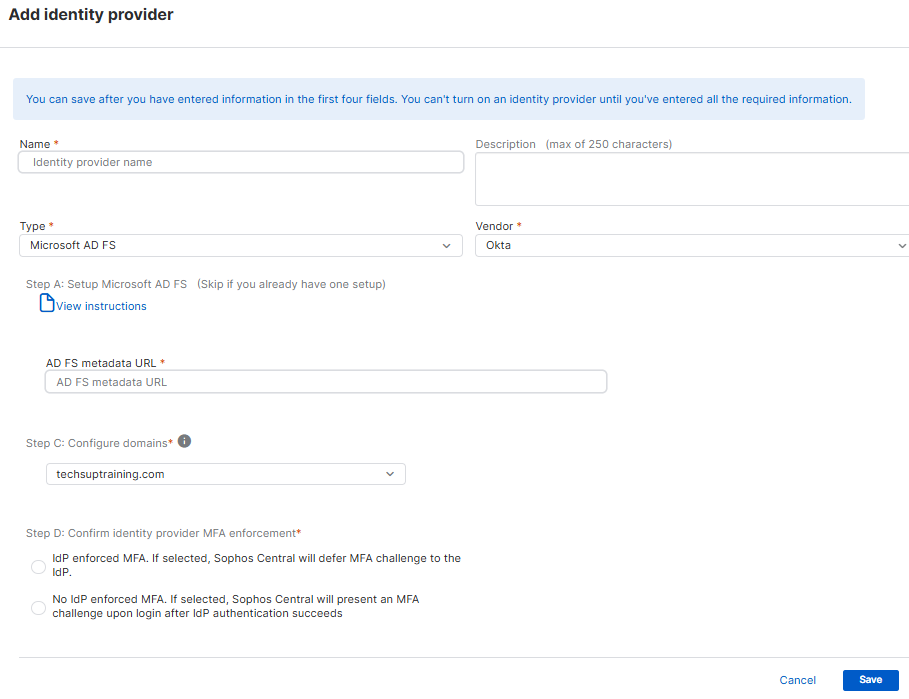
Add Microsoft AD FS as an identity provider
You can add Microsoft AD FS as an identity provider.
Before you add Microsoft AD FS as an identity provider, you must follow the instructions in Use Microsoft AD FS as an identity provider.
You must know your AD FS metadata URL.
To add Microsoft AD FS, do as follows:
- Click the General Settings icon
 .
. - Under Administration, click Federated identity providers.
- Enter a name and description.
- Click Type and select Microsoft AD FS.
- Click Vendor and select your vendor.
- In AD FS metadata URL, enter your AD FS metadata URL.
-
In Configure domains, click Select a domain and select your domain.
You can add multiple domains, but each user can only be associated with a single domain.
-
In Confirm identity provider MFA enforcement, select one of the following options:
- IdP enforced MFA: Sophos Central allows the identity provider (IdP) to enforce multi-factor authentication (MFA).
- No IdP enforced MFA: Sophos Central enforces MFA after the IdP authentication is successful.
-
Click Save.
-
In Federated identity providers, select your identity provider and make a note of the following:
- Entity ID.
- Callback URL.
-
Add your Entity ID and Callback URL to your AD FS configuration.
-
In Federated identity providers, select your identity provider and click Turn on.
Note
You can't turn on your provider if you haven't finished setting it up or if you've given invalid information.
You can now set up your sign-in settings. See Sophos sign-in settings.