Investigate cases
This page is only for "Self-managed" cases.
You can investigate cases using information and tools available in the Case details page, as described on this page.
We also recommend that you use our AI assistant to find out more about the detection and get suggestions for taking action. See AI assistant.
Keep a record of your investigation on the Notebook tab in a case's details pages.
In some cases, you can also respond to cases. See Respond to cases.
Investigate a case
To start your investigation, do as follows:
-
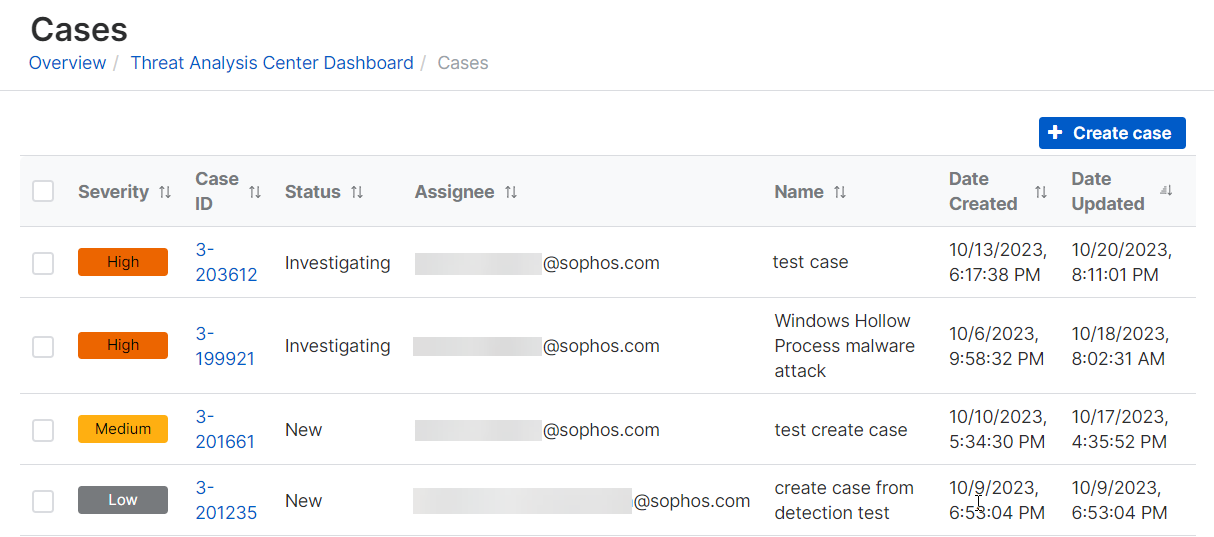
Go to the Cases page.
-
Click the Case ID of the case.
-
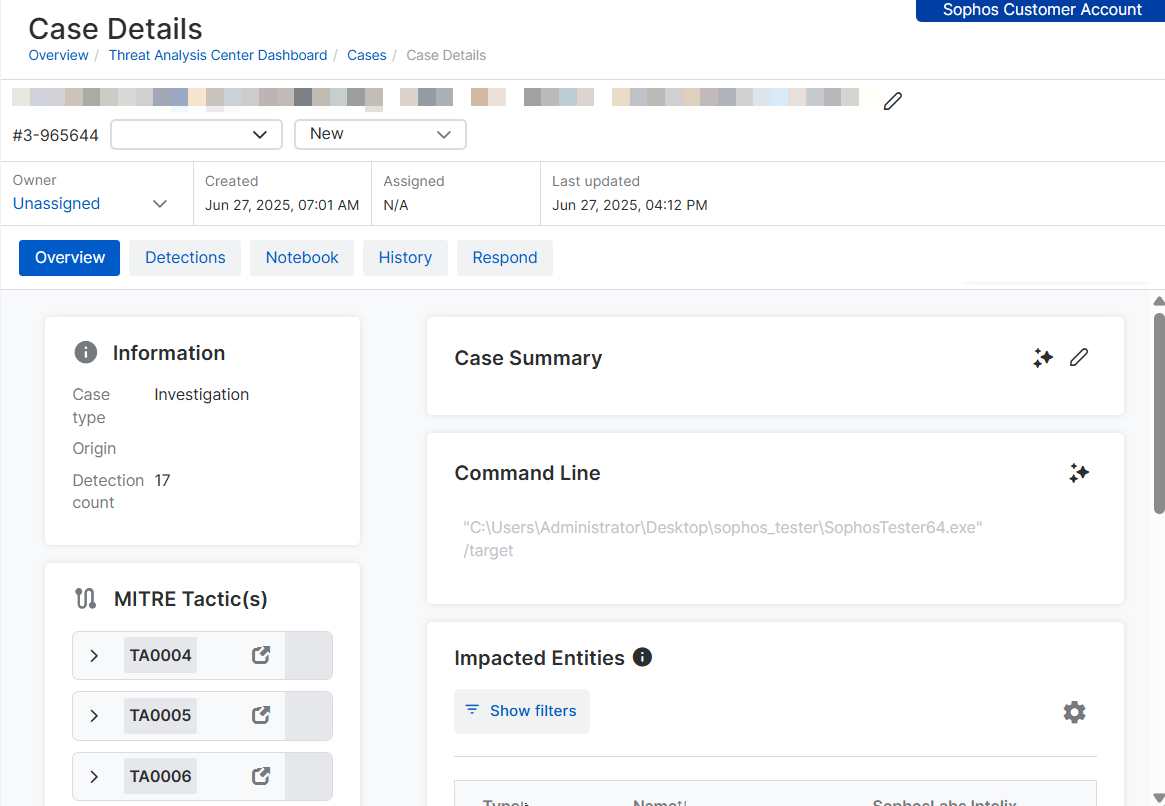
On the Overview tab, you can find information about the detection that generated the case and start your analysis using Sophos AI tools.
You can do as follows:
- Use the Sophos AI assistant to investigate. See Ask Sophos AI.
- Summarize information about the case. See Case summary.
- Analyze the command line run by the threat. See Command line analysis.
- Check which devices and users were affected. See Impacted entities.
- Find out the attack tactics and techniques used. See MITRE tactics or look in the detection details.
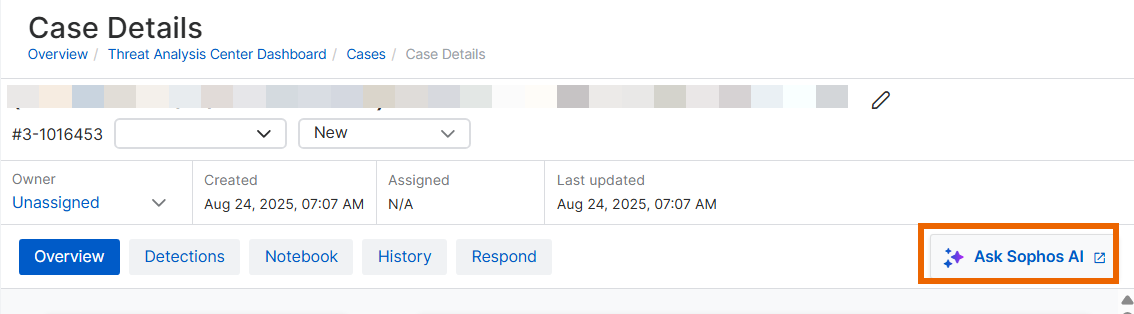
Ask Sophos AI
Click Ask Sophos AI on the right of the page if you want to use the Sophos AI assistant to investigate the case. For help with using the assistant, see AI assistant.
Note
The Ask Sophos AI option is available whichever tabbed page you're on.
Case summary
You can use Sophos AI to generate a case summary for you.
-
In Case Summary, click the AI icon.
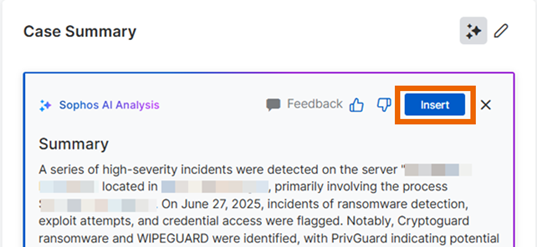
Sophos AI analyzes the case and summarizes the details.
-
If you want to save the summary, click Insert. To discard it, click the "X".
If you save the summary, you can click the Edit icon
 and make changes to it.
and make changes to it.
Alternatively, you can summarize the case manually. Click the Edit icon ![]() and enter your summary.
and enter your summary.
Command line analysis
You can use Sophos AI to analyze the command line run by the threat that generated the case.
In Command Line, click the AI icon.
Sophos AI analyzes the command line to discover the threat's intentions and possible impact. If necessary, it de-obfuscates code, minimizing the effort needed to assess the threat.
Impacted entities
Impacted Entities lists the devices, users, files, IP addresses, and processes affected by the detected threat.
Click a device name to see its full details in the Computers & Servers page.
Restriction
Impacted entities might not be shown for cases created manually because we don't get the initial detection details.
MITRE tactics
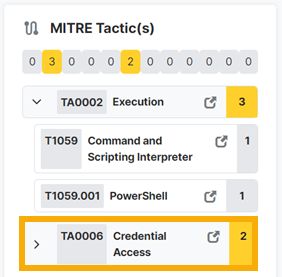
The MITRE tactics pane lists any MITRE ATT&CK tactics and techniques we detected.
Click the fold-out arrow beside a tactic to see the technique.
Click the link beside any tactic or technique, for example Credential Access, to go to its details on the MITRE website.
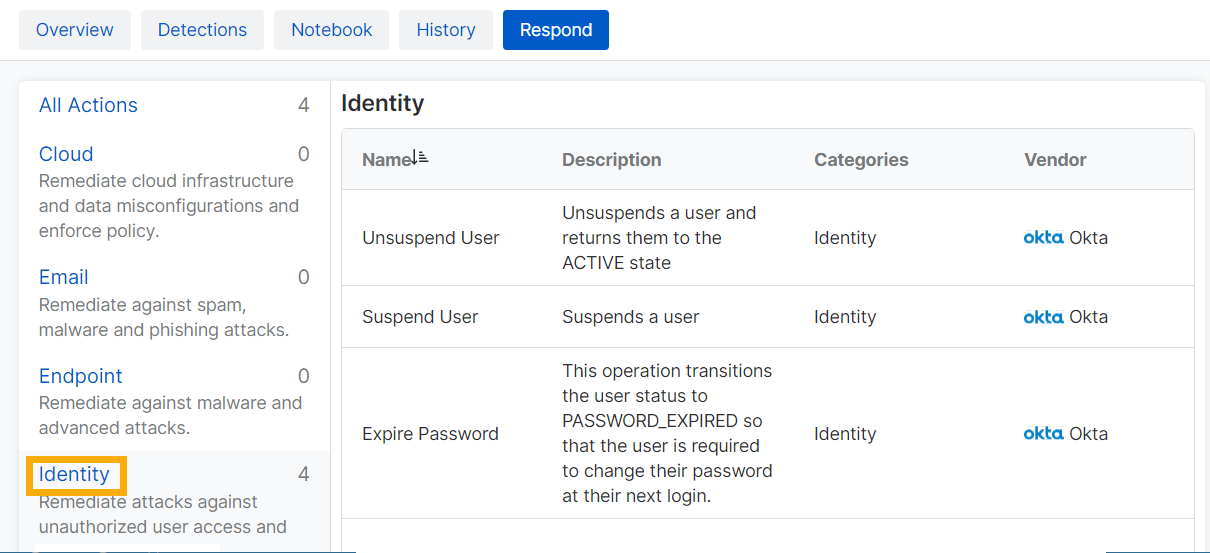
Respond to cases
The Response Action feature is currently not available for most third-party product integrations.
In some cases, you can resolve detected issues via third-party products.
To use this feature, you must set up a Response Action integration with the third-party product you want to use. Go to Products and click your product.
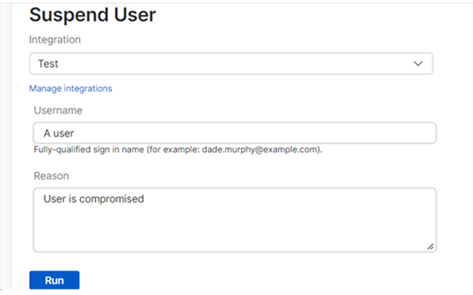
Our example shows how to use a response action to suspend a compromised user. To take action, do as follows: