AWS Security Hub
-
AWS integration update
This AWS integration will be retired in the future and should no longer be used. We recommend that customers migrate to Sophos Cloud Optix to take advantage of its advanced capabilities.
Use Sophos Cloud Optix to integrate AWS to Sophos Central. For more information, see Sophos Cloud Optix.
MSP Flex customers must have the Public Cloud integrations license pack to use this feature.
You can integrate AWS Security Hub with Sophos Central so that it sends alerts to Sophos for analysis.
Before you start
You need to enable AWS Security Hub in the environment you want to integrate before you can continue.
During the integration we give you commands to copy and run. You must run these commands in AWS CLI or AWS CloudShell, from an IAM user with the "Administrator" role. To find out how to set up AWS CLI, see Getting started with the AWS CLI.
If you don't have access to an appropriate account, you can create a custom role with specific permissions. The permissions you need are in Custom role permissions.
Setup AWS Security Hub integration
To integrate your AWS environment, do as follows:
- In Sophos Central, go to Threat Analysis Center > Integrations > Marketplace.
-
Click AWS Security Hub.
If you've already set up connections to AWS environments, you see them here.
-
Click Add.
-
The Integration steps assistant takes you through the process of connecting to your AWS environment. To do this, do as follows:
- Copy the curl command.
-
Go to AWS CLI or AWS CloudShell and run the curl command.
The integration script is downloaded.
-
Go back to Sophos Central and copy the second command shown in Integration steps.
- Go to AWS CLI or AWS CloudShell and run the integration command.
-
Return to Sophos Central.
The AWS environment appears in the list.
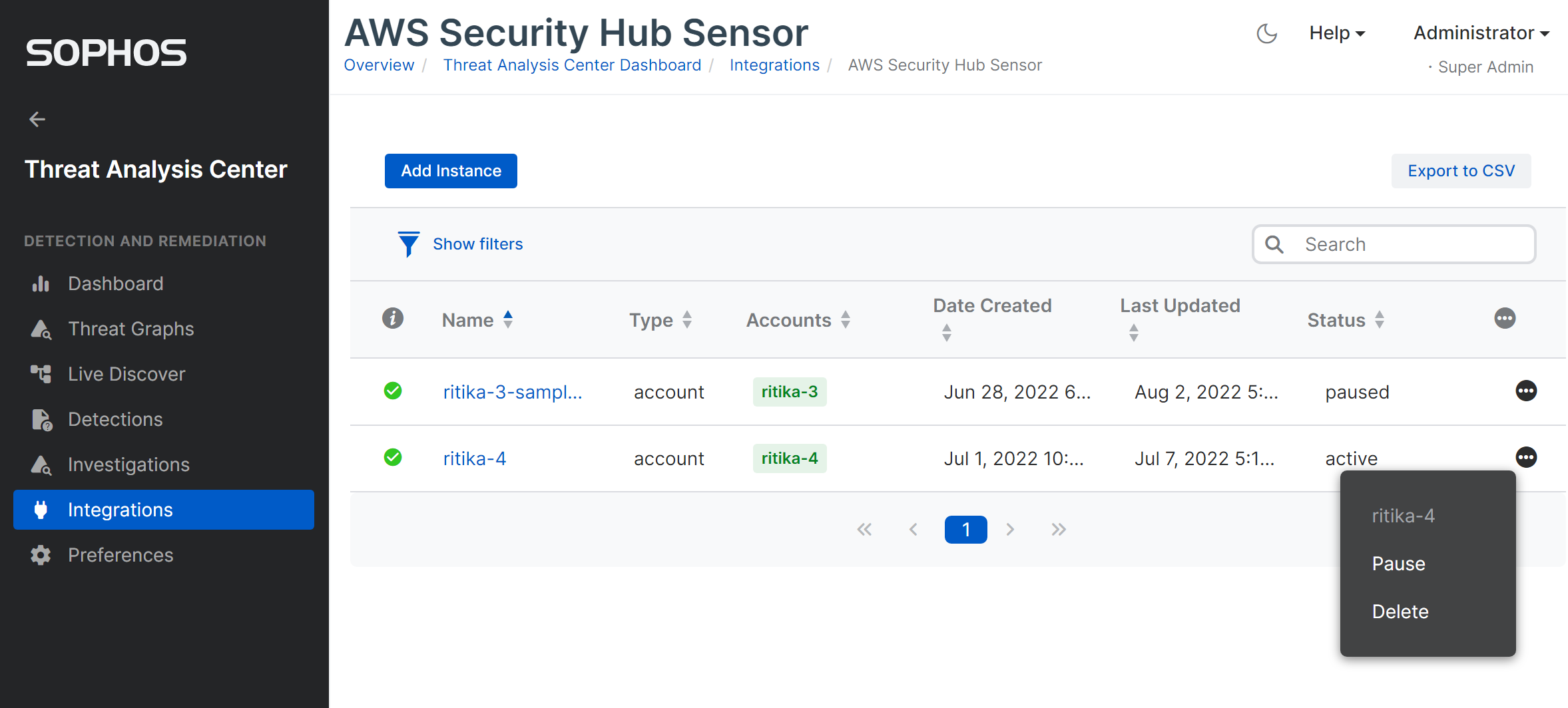
Manage AWS Security Hub integrations
You can click the name of the AWS environment to edit settings.
Status shows the status of the integration with an AWS environment. This can be paused, active, disconnected or deleted.
You can click the three dots icon and select actions, depending on the current status.
To delete a connection, click Delete. An assistant takes you through the process of deleting the connection, using AWS CLI commands.
If your Sophos license expires, your connections are paused. When you renew your license, the connections automatically become Active.
Include AWS Organizations accounts
If you're using AWS Organizations, you can choose which accounts to include in data collection.
- In Sophos Central, go to Threat Analysis Center and click Integrations.
-
Click AWS CloudTrail.
A list of your integrations appears.
-
Click the name of the integration you want to change.
If you've many integrations, use the filter to list the integrations that use AWS Organizations.
-
In Edit Details > Accounts you can add a comma separated list of account IDs for which you want to collect data.
- Click Save.
We now only collect data from the AWS accounts in the list.
Custom role permissions
You can run the AWS commands we give you from an IAM user with the "Administrator" role.
If you want to set up a custom role instead, use the following permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
'events:DeleteRule',
'events:ListRules',
'events:ListTagsForResource',
'events:ListTargetsByRule',
'events:PutRule',
'events:PutTargets',
'events:RemoveTargets',
'events:TagResource',
'events:UntagResource',
'ec2:DescribeRegions',
'iam:AttachRolePolicy',
'iam:CreatePolicy',
'iam:CreateRole',
'iam:DeleteRole',
'iam:DeleteRolePolicy',
'iam:GetPolicy',
'iam:GetPolicyVersion',
'iam:GetRole',
'iam:GetRolePolicy',
'iam:ListAttachedRolePolicies',
'iam:ListPolicyTags',
'iam:ListRoleTags',
'iam:PassRole',
'iam:PutRolePolicy',
'iam:TagPolicy',
'iam:TagRole',
'iam:UntagPolicy',
'iam:UntagRole',
'lambda:AddPermission',
'lambda:CreateFunction',
'lambda:DeleteEventSourceMapping',
'lambda:DeleteFunction',
'lambda:GetFunction',
'lambda:GetFunctionConfiguration',
'lambda:GetPolicy',
'lambda:ListEventSourceMappings',
'lambda:ListTags',
'lambda:TagResource',
'lambda:UntagResource',
'lambda:UpdateFunctionConfiguration',
'logs:CreateLogGroup',
'logs:DeleteLogGroup',
'logs:DeleteLogStream',
'logs:DeleteRetentionPolicy',
'logs:PutRetentionPolicy',
'sqs:AddPermission',
'sqs:CreateQueue',
'sqs:DeleteQueue',
'sqs:GetQueueAttributes',
'sqs:GetQueueUrl',
'sqs:ListQueueTags',
'sqs:ListQueues',
'sqs:RemovePermission',
'sqs:SetQueueAttributes',
'sqs:TagQueue',
'sqs:UntagQueue',
'sts:GetCallerIdentity',
'tag:TagResources'
],
"Resource": "*"
}
]
}