Appliance requirements
If your integrations use an appliance, check which platforms are supported and make sure you meet the requirements.
Supported platforms
You can run an integrations appliance on the following software platforms:
- VMware ESXi
- Microsoft Hyper-V
- Amazon Web Services (AWS)
- Nutanix
These platforms can be used for both Sophos NDR and third-party log collector integrations.
Note
This page describes the requirements for VMware ESXi and Microsoft Hyper-V. For AWS requirements, see Add integrations on AWS. For information about Nutanix, see Sophos NDR on Nutanix.
Alternatively, you can run an integrations appliance on the following hardware:
- Dell
- NUC
- OnLogic
These hardware systems can be used for both Sophos NDR and third-party log collector integrations.
For hardware requirements and setup instructions, see Sophos NDR on hardware.
Requirements
These requirements are for VMware ESXi or Hyper-V.
The requirements you must meet include the following:
- Platform version
- Minimum system requirements
- CPU requirements
- VM sizing
- Port and domain exclusions
Platform version
Check your version of VMware ESXi or Microsoft Hyper-V.
VMware ESXi requirements
If you use VMware ESXi, the requirements are as follows:
- VMware ESXi 6.7 Update 3 or later
- VM hardware version 11 or higher
We don't support VMware Cloud deployments.
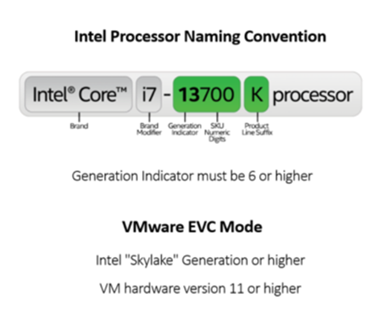
We support VMware Enhanced vMotion Compatibility (EVC) Modes if you meet the CPU requirements. See CPU requirements.
To check your version of VMware ESXi, see these articles:
- Determining the build number of VMware ESX/ESXi and VMware vCenter Server
- Build numbers and versions of VMware ESXi/ESX
Microsoft Hyper-V requirements
If you use Microsoft Hyper-V, the requirements are as follows:
- Hyper-V version 6.0.6001.18016 (Windows Server 2016) or later
We don't support Processor Compatibility Mode.
To check your version of Microsoft Hyper-V, see Identifying your Hyper-V Version.
Minimum system requirements
The minimum system requirements are the same on all platforms.
On VMware, our OVA image is pre-configured to meet the minimum requirements for both Sophos NDR and log collector integrations.
The requirements are as follows:
- 4 CPUs
- 16GB RAM
- 160GB storage
The appliance also requires specific CPU microarchitectures. See CPU requirements.
You may need to resize the VM if your appliance handles a large volume of data or runs multiple integrations. See VM sizing.
CPU requirements
The system running the VM must use one of the CPU microarchitectures shown below.
If you have Sophos NDR, you must also ensure the following CPU flags are set:
pdpe1gb: The packet capture technology needs this.avx2: The Sophos machine learning features need this.
Both flags are available in the Intel and AMD CPUs, as shown in the table below.
NDR can also run on VMs with more current CPUs, such as Intel Core i5, as long as they have the CPU flags set. Any CPU launched since Q1'15 should work.
Intel CPUs
| Name | Generation | Codename | Date |
|---|---|---|---|
| Skylake | 6 | Skylake | Q3 2015 |
| Skylake | 7 | Kaby Lake | Q3 2016 |
| Skylake | 8 | Coffee Lake | Q3 2017 |
| Skylake | 9 | Coffee Lake Refresh | Q4 2018 |
| Skylake | 9 | Cascade Lake | Q2 2019 |
| Skylake | 10 | Comet Lake | Q3 2019 |
| Palm Cove | 10 | Cannon Lake | Q2 2018 |
| Sunny Cove | 10 | Ice Lake | Q3 2019 |
| Cypress Cove | 11 | Rocket Lake | Q1 2021 |
| Golden Cove | 12 | Alder Lake | Q4 2021 |
| Raptor Cove | 13 | Raptor Lake | Q4 2022 |
To help you identify CPUs, Intel's CPU naming conventions are shown below.
VMware EVC mode
If your appliance is on a VMware ESXi host running in an Enhanced vMotion Compatibility (EVC) cluster, you must make sure you've selected:
- Skylake generation or later CPU
- VMware hardware version 11 or later
AMD CPUs
| Name | Generation | Codename | Date |
|---|---|---|---|
| Zen | 1 | Naples | Q2 2017 |
| Zen | 1 | Great Horned Owl | Q1 2018 |
| Zen 2 | 2 | Rome | Q3 2019 |
| Zen 3 | 3 | Milan | Q2 2021 |
| Zen 4 | 4 | Genoa | Q4 2022 |
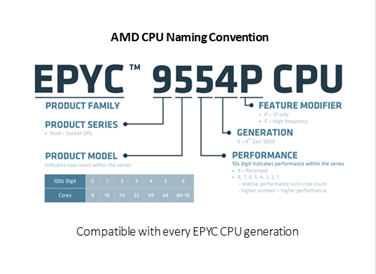
To help you identify CPUs, AMD's CPU naming conventions are shown below.
VM sizing
VM sizing guidelines depend on whether you have Sophos NDR, log collector integrations, or both on the VM.
Sophos NDR only
You might need to configure the VM to ensure that the Sophos NDR virtual appliance gives the best performance and least impact on the network.
Here are our recommendations, based on your network traffic.
-
Medium traffic
- up to 500Mbps
- up to 70,000 packets per second
- up to 1200 flows per second
You can install the virtual machine using the defaults. No changes to VM settings are required.
-
High traffic
- up to 1Gbps
- up to 300,000 packets per second
- up to 4500 flows per second
You should resize your VM to 8 vCPUs.
If your network statistics are higher than those in the High traffic configuration, deploy multiple VMs throughout your network.
The recommendations above are for a VM running Sophos NDR only. If it's also running log collector integrations under heavy load, you might need to add more virtual CPUs. See Sophos NDR and log collector integrations.
Log collector integrations only
You don't usually need to resize a VM if you're running a single log collector integration. The default settings are sufficient.
However, you might need to change settings or add more VMs if you have multiple integrations or a high volume of events is sent to your log collectors.
Memory
You need up to 400MB of memory for each integration.
You can run up to four integrations per log collector. The default maximum memory for the log collector container is 2GB.
If you want to run more integrations, increase the maximum memory. To do this, edit the SYSLOG memory limit in the appliance console. See Syslog memory limit.
Volume of events
The VM can accept a maximum of 8,000 events per second. This applies no matter how many integrations you have on the VM.
If you have multiple integrations and think you'll exceed this limit, deploy multiple VMs.
If a single log collector integration exceeds the limit, use the syslog settings on the source device to try to reduce the number of events.
Sophos NDR and log collector integrations
If you have Sophos NDR and log collector integrations on the same VM, there isn't a single solution for sizing. We recommend you begin with the NDR sizing and then consider what the log collector integrations need.
Here are some factors that may affect your sizing:
- NDR can take over CPUs and set the priority given to other integrations that use it. If you have 4 CPUs, NDR takes over 2. If you have 8 CPUs, NDR takes over 3.
- Even when NDR takes over a CPU, other integrations can still use it and affect how much traffic NDR can handle.
- If you have 16GB of memory, we don’t allow the log collector integration to use more than 2GB. This ensures that NDR has enough memory.
- When a log collector integration processes the maximum number of events, it uses the same processing power as Sophos NDR under a moderately heavy load. This assumes that the VM has the default 4 CPUs.
Port and domain exclusions for Sophos appliances
Make sure the ports and domains below are allowed on your firewall. This lets the Sophos virtual appliance boot and download updates.
The domains you need to allow depend on whether your firewall supports wildcards.
Click the appropriate tab for details.
| Domain | Ports | Protocols |
|---|---|---|
| *.sophos.com | TCP/443, TCP/22 | HTTPS, SSH |
| *.amazonaws.com | TCP/443 | HTTPS |
| *.ubuntu.com | TCP/80, TCP/443, UDP/123 | HTTP, HTTPS, NTP |
| api.snapcraft.io | TCP/443 | HTTPS |
| auth.docker.io | TCP/443 | HTTPS |
| get.k3s.io | TCP/443 | HTTPS |
| github.com | TCP/443 | HTTPS |
| objects.githubusercontent.com | TCP/443 | HTTPS |
| packages.buildkite.com | TCP/443 | HTTPS |
| production.cloudflare.docker.com | TCP/443 | HTTPS |
| raw.githubusercontent.com | TCP/443 | HTTPS |
| registry-1.docker.io | TCP/443 | HTTPS |
| sophossecops.jfrog.io | TCP/443 | HTTPS |
| Domain | Port | Protocol |
|---|---|---|
| api.snapcraft.io | TCP/443 | HTTPS |
| archive.ubuntu.com | TCP/80 | HTTP |
| auth.docker.io | TCP/443 | HTTPS |
| central.sophos.com | TCP/443 | HTTPS |
| changelogs.ubuntu.com | TCP/443 | HTTPS |
| entropy.ubuntu.com | TCP/443 | HTTPS |
| get.k3s.io | TCP/443 | HTTPS |
| github.com | TCP/443 | HTTPS |
| jfrog-prod-use1-shared-virginia-main.s3.amazonaws.com | TCP/443 | HTTPS |
| ndr.apu.sophos.com | TCP/22 | SSH |
| nta-proxy.cloudstation.eu-central-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.eu-west-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.us-east-2.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.us-west-2.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.ca-central-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.ap-northeast-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.ap-southeast-2.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.ap-south-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-proxy.cloudstation.sa-east-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.eu-central-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.eu-west-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.us-east-2.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.us-west-2.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.ca-central-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.ap-northeast-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.ap-southeast-2.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.ap-south-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| nta-push-ws.cloudstation.sa-east-1.prod.hydra.sophos.com | TCP/443 | HTTPS |
| ntp.ubuntu.com | UDP/123 | NTP |
| objects.githubusercontent.com | TCP/443 | HTTPS |
| packages.buildkite.com | TCP/443 | HTTPS |
| production.cloudflare.docker.com | TCP/443 | HTTPS |
| raw.githubusercontent.com | TCP/443 | HTTPS |
| registry-1.docker.io | TCP/443 | HTTPS |
| s3-r-w.eu-west-1.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.eu-central-1.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.us-east-2.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.us-west-2.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.ca-central-1.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.ap-southeast-2.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.ap-northeast-1.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.ap-south-1.amazonaws.com | TCP/443 | HTTPS |
| s3-r-w.sa-east-1.amazonaws.com | TCP/443 | HTTPS |
| sdu-feedback.sophos.com | TCP/443 | HTTPS |
| security.ubuntu.com | TCP/80 | HTTP |
| sophossecops.jfrog.io | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-eu-west-1-prod-bucket.s3.eu-west-1.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-eu-central-1-prod-bucket.s3.eu-central-1.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-us-east-2-prod-bucket.s3.us-east-2.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-us-west-2-prod-bucket.s3.us-west-2.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-ca-central-1-prod-bucket.s3.ca-central-1.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-ap-southeast-2-prod-bucket.s3.ap-southeast-2.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-ap-northeast-1-prod-bucket.s3.ap-northeast-1.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-ap-south-1-prod-bucket.s3.ap-south-1.amazonaws.com | TCP/443 | HTTPS |
| tf-nta-sva-images-cloudstation-sa-east-1-prod-bucket.s3.sa-east-1.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-eu-west-1-prod-ndr-bucket.s3.eu-west-1.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-eu-central-1-prod-ndr-bucket.s3.eu-central-1.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-us-east-2-prod-ndr-bucket.s3.us-east-2.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-us-west-2-prod-ndr-bucket.s3.us-west-2.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-ca-central-1-prod-ndr-bucket.s3.ca-central-1.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-ap-southeast-2-prod-ndr-bucket.s3.ap-southeast-2.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-ap-northeast-1-prod-ndr-bucket.s3.ap-northeast-1.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-ap-south-1-prod-ndr-bucket.s3.ap-south-1.amazonaws.com | TCP/443 | HTTPS |
| tf-presigned-url-sa-east-1-prod-ndr-bucket.s3.sa-east-1.amazonaws.com | TCP/443 | HTTPS |