Detections
The Detections page shows threats detected on the computer.
You may not have all the features described here. This depends on your license.
The upper part of the page shows whether there are any detections to deal with.
No malware or PUAs outstanding indicates that there are no detections or that any detections have been cleaned up.
Click Scan to scan the computer for threats now.
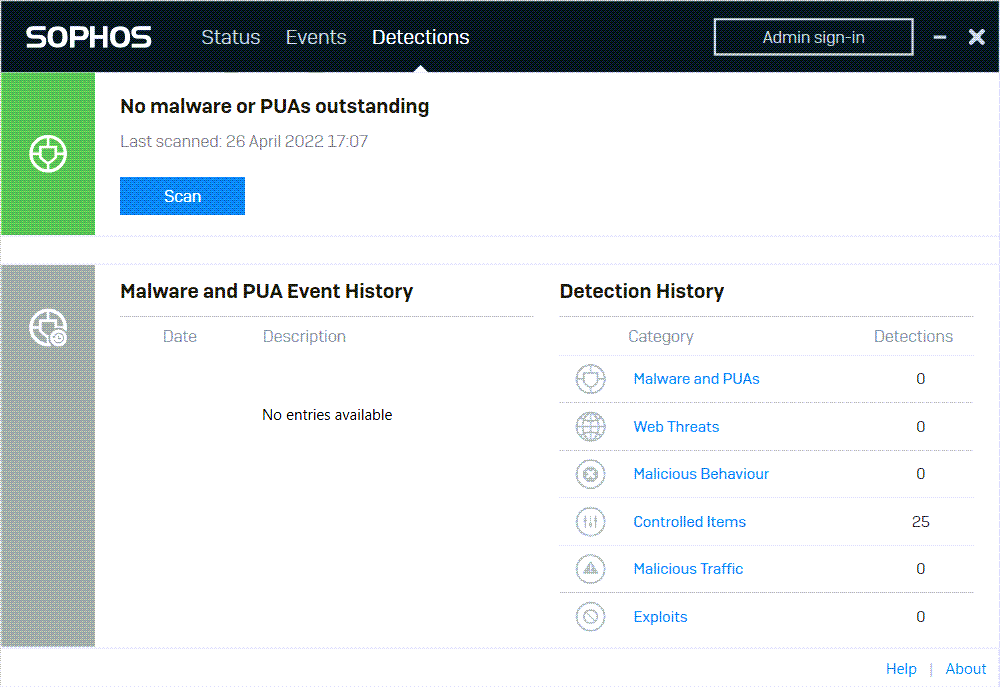
Detection history
Malware and PUA Event history shows details of malware and PUAs.
The Detection history shows statistics for each type of threat detected. Click any threat type to see a list of detection events of that type on the Events page.
Detection types
Here are details of the types of threats and unwanted items.
| Detection type | Description |
|---|---|
| Malware and PUAs | Malware is a general term for malicious software. It includes viruses, worms, Trojans and spyware. Potentially unwanted applications (PUAs) are programs that aren't malicious, such as dialers, remote administration tools and hacking tools, but are generally considered unsuitable for most business networks. |
| Web threats | Web threats include malicious websites, uncategorized websites, and risky downloads. Some websites are also generally considered unsuitable for business networks, for example adult websites or social media. These can be blocked. |
| Malicious behavior | Malicious behavior is suspicious behavior detected in software that is already running on the computer or server. This detection type is only for Windows. |
| Ransomware | Ransomware is malicious software that denies you access to your files until you pay a ransom. |
| Controlled Items | This category includes:
|
| Malicious Traffic | Malicious traffic is traffic between computers that indicates a possible attempt to take control of the computer or server (a “command and control” attack). |
| Exploits | Exploits that Sophos can prevent include application hijacking and exploits that take advantage of vulnerabilities in browsers, browser plug-ins, Java applications, media applications and Microsoft Office applications. This detection type is only for Windows. |