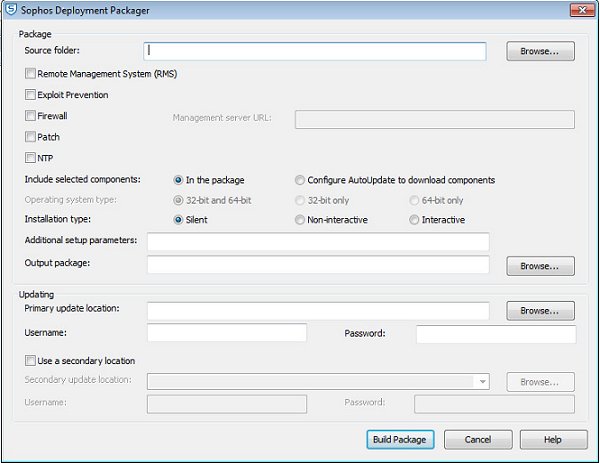
Create a protection package using the GUI
-
To create a protection package, run DeploymentPackager.exe.
The Sophos Deployment Packager dialog box is displayed.
- In Source folder, specify the location of the central installation directory containing the endpoint software installation files. This may be a UNC path or a local folder.
-
Select from the following:
- Remote Management System
(RMS): This installs and enables the Sophos Remote Management System, which
allows Sophos Enterprise Console to control Sophos Endpoint Security and Control. For Managed systems you must enable this
component.Note When you select this option, endpoints obtain their updating path and credentials from Sophos Enterprise Console through RMS.
- Exploit Prevention: This installs Sophos Exploit Prevention.
- Firewall: This installs
the Sophos Client Firewall. Note If you want to install this option, check endpoint system requirements at Sophos system requirements.
- Patch: This installs
Sophos Patch Agent. You must also enter the address where the Management server is installed
under Management Server URL. The address must be a fully qualified domain
name. Example: http://<server name>.
If you select this option, you can choose the Operating system type.
- NTP: This installs and enables Sophos Network Threat Protection (NTP).
- In Include selected
components do one of the following:
To include the selected components in the deployment package, click In the package.
To download selected components from the update source, click Configure AutoUpdate to download components.
Note The endpoint installer is unable to use a proxy server. If the update location is accessed through a proxy server, then the required endpoint components must be included in the package.
If you select Remote Management System (RMS) and then click In the package in Include selected components, the updating details are obtained from Sophos Enterprise Console.
Sophos System Protection and Sophos Endpoint Defense packages will be automatically added to the generated package (if they are part of the licensed packages) as they are not optional components.
- Remote Management System
(RMS): This installs and enables the Sophos Remote Management System, which
allows Sophos Enterprise Console to control Sophos Endpoint Security and Control. For Managed systems you must enable this
component.
- In Operating system type, choose which operating system type to package. This option is only applicable if Patch is being installed from the deployment package. If you choose either 32-bit or 64-bit, the package can be installed only on specific 32-bit or 64-bit operating systems. If you choose 32-bit and 64-bit, the package can be installed on both 32 and 64-bit operating systems, but the package size will be large.
-
In Installation type, select how the installation program will run on
endpoint computers.
- Select Silent: the program runs without any user interaction. The installation progress is not displayed on the endpoint computer.
- Select Non-interactive: the program runs without any user interaction. The installation progress is displayed on the endpoint computer.
- Select Interactive: the program runs with user interaction. The user can control the installation.
-
In Additional setup parameters, specify endpoint setup installation options.
Always specify group membership using the -g option so that each installer is specific to and sets
up endpoints to be members of existing groups.
The packager does not check these options for errors.
For further information, see knowledge base article 12570.
- In Output package, specify the destination path for the output installer package. You can also specify an optional filename; if this is not supplied, the Deployment Packager will use a default filename.
-
In the Updating panel, for indirectly-managed endpoint packages or where
remote management is enabled but not included in the package, enter the update path and credentials.
You may set ":<port number>" after an HTTPS URL; if unset, this defaults to
80.
- Ensure all the components that are selected can be updated from the update location you specify (for example, Patch). If a different location is used for components, you can configure it as a secondary update location.
- Credentials are obfuscated in the package; however, accounts set up for endpoints to read update server locations should always be as restrictive as possible, allowing only read-only access.
- Endpoints will attempt to use their system proxy settings only if set using the environmental variables http_proxy or all_proxy. Proxy settings in Windows Control Panel Internet Options or Internet Explorer are ignored. _proxy variable values take the format _proxy=[protocol://][user:password@]host[:port], for example https_proxy=http://user:password@proxy:8080.
- Click Build Package to build the self-extracting archive.