Route system-generated authentication queries through an IPsec tunnel
You can route traffic generated by Sophos Firewall through a policy-based or route-based VPN tunnel.
For example, you can route the branch office firewall's authentication queries to the AD server deployed in the head office through an IPsec tunnel.
Overview
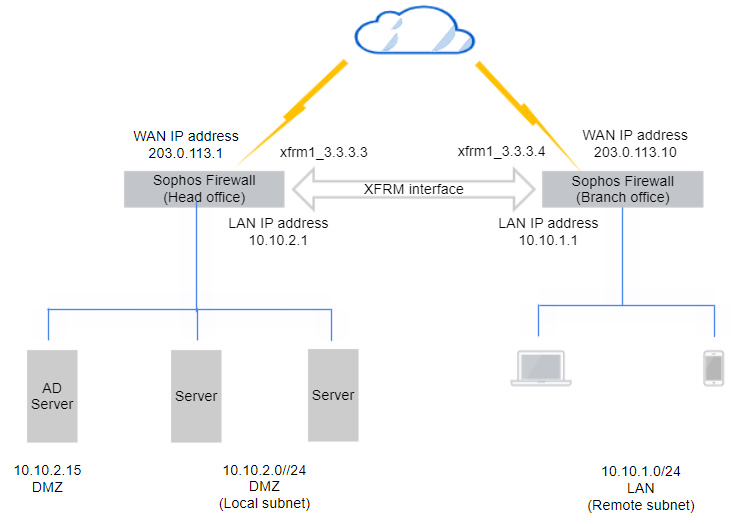
An IPsec VPN tunnel connects the head office and the branch office firewalls.
System-generated traffic uses a gateway listed on Network > WAN link manager by default. You can ensure that this traffic uses an IPsec tunnel. This example shows how to use policy-based and route-based tunnels for the traffic.
For policy-based IPsec tunnels, do as follows on the branch office firewall:
- Add an IPsec route for system-generated traffic to the AD server.
- Translate (source NAT) the branch office gateway addresses to a LAN or WAN interface for authentication queries to the AD server's address. In this example, we use a LAN interface.
- Check the local and remote subnets in your policy-based IPsec configuration for the LAN or WAN interface you've used in the translation.
For route-based IPsec tunnels, do as follows:
- Translate (source NAT) the branch office gateway addresses to the XFRM interface for authentication queries to the AD server's address. Do this on the branch office firewall.
- Configure an SD-WAN route to send authentication queries to the XFRM interface. Do this on the branch and head office firewalls.
- Configure inbound and outbound firewall rules on the head office firewall.
The configuration details are examples based on the following network diagram:
Prerequisite: Configure an IPsec VPN tunnel
You must have one of the following VPN configurations on both firewalls:
- A policy-based VPN for traffic between the branch office LAN and the head office DMZ subnets. See the following configuration examples:
- A route-based VPN with any-to-any subnets between the branch and head office firewalls. See the following configuration example:
You must configure the following IP hosts on both firewalls:
- AD server (example:
10.10.1.15) - Branch office LAN interface (example:
10.10.1.1) - XFRM interface addresses (example:
3.3.3.3and3.3.3.4)
You must add an IPsec route and translate the gateway addresses on the branch office firewall.
Branch office: Add an IPsec route
Do as follows:
- Sign in to the CLI of the branch office firewall.
- Enter 4 for Device console and press Enter.
-
To add an IPsec route that sends system-generated traffic to the AD server through an IPsec connection, enter the following command:
system ipsec_route add host <IP address of host> tunnelname <tunnel>Example
system ipsec_route add host
10.10.2.15tunnelname Branch_to_HeadOffice
Translate the addresses of gateways system-generated traffic uses
Do as follows:
-
Translate the branch office firewall's gateway addresses to a LAN interface address for authentication queries to the AD server at the head office.
Enter the following command:
set advanced-firewall sys-traffic-nat add destination <Destination or network IP address> snatip <NATed IP>Example
set advanced-firewall sys-traffic-nat add destination
10.10.2.15snatip10.10.1.1 -
Make sure you've selected the translated LAN interface as a local and remote subnet in the corresponding branch and head office IPsec configurations.
You can use a route-based tunnel with any-to-any subnets.
Branch office: Add an SD-WAN route
- Go to Routing > SD-WAN routes and click Add.
- Enter a Name.
- Set Source networks to Any.
- Set Destination networks to the IP host for the AD server. To configure the IP host, do as follows:
- Click Add new item and clear Any.
- Click Add and enter a Name.
- For IP address, enter
10.10.2.15 - Click Save.
-
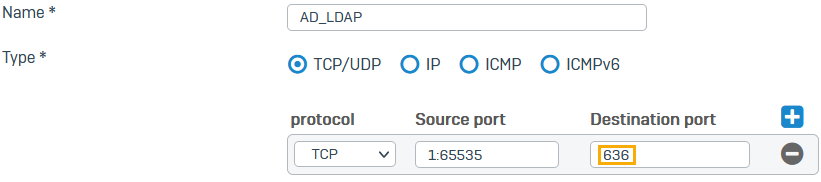
For Services, create an object for TCP port 636 (the default port for secure AD and LDAP authentication).
Do as follows:
- Click Add new item and clear Any.
- Click Add and click Services.
- Enter a Name.
- For Destination port, enter
636. -
Click Save.
-
Under Link selection settings, select Primary and backup gateways.
- Click the drop-down list for Primary gateway and click Add.
-
Do as follows:
- Enter a name.
- For Gateway IP, enter the head office XFRM IP address (
3.3.3.3). -
For Interface, select the XFRM interface you've configured on this firewall (example:
xfrm1_3.3.3.4).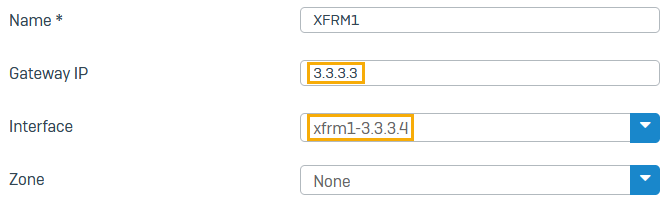
-
If you want Health check on, for Monitoring condition, enter the AD server's IP address (
10.10.2.15).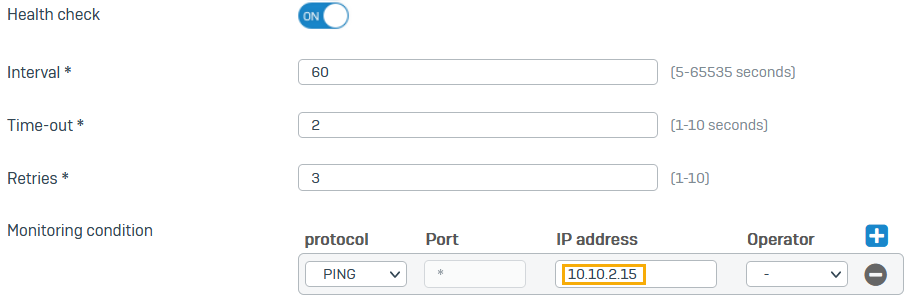
-
Select Route only through specified gateways.
The firewall then drops traffic if the tunnel isn't available.
-
Click Save.
Branch office: Turn on ping through VPN
- Go to Administration > Device access.
- Under Ping/Ping6, select the checkbox for VPN.
- Click Apply.
Branch office: Translate the gateway used by default
Translate (source NAT) the branch office firewall's gateway addresses to the XFRM interface address for system-generated traffic to the head office AD server.
Enter the following command:
set advanced-firewall sys-traffic-nat add destination <Destination or network IP address> snatip <NATed IP>
Example
set advanced-firewall sys-traffic-nat add destination 10.10.2.15 snatip 10.10.1.1
Head office: Add an SD-WAN route
- Go to Routing > SD-WAN routes and click Add.
- Enter a Name.
- Set Source networks to the IP host for the AD server (
10.10.2.15). - Set Destination networks to the IP host for the LAN interface to which you've translated on the branch office firewall (
10.10.1.1). -
For Services, create an object for TCP port 636 (the default port for secure AD and LDAP authentication.)
Do as follows:
- Click Add new item and clear Any.
- Click Add and click Services.
- Enter a Name.
- For Destination port, enter
636. - Click Save.
-
Under Link selection settings, select Primary and backup gateways.
- Click the drop-down list for Primary gateway and click Add.
-
Do as follows:
- Enter a name.
- For Gateway IP, enter the branch office XFRM IP address (
3.3.3.4). -
For Interface, select the XFRM interface you've configured on this firewall (example:
xfrm1_3.3.3.3).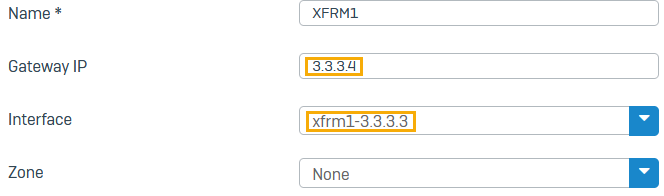
-
If you want Health check on, for Monitoring condition, enter an IP address in the branch office LAN (
10.10.1.10).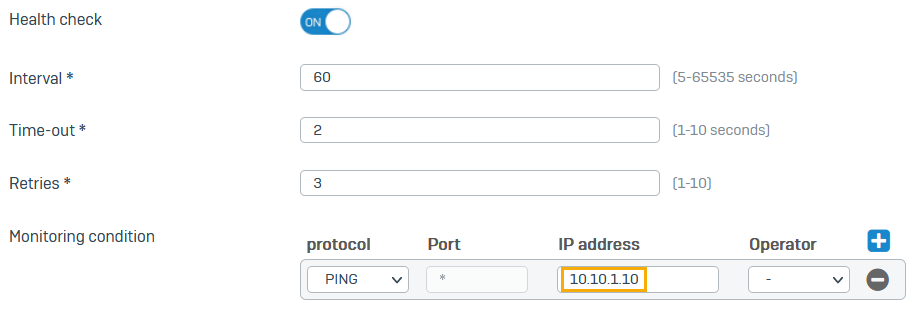
-
Select Route only through specified gateways.
The firewall then drops traffic if the tunnel isn't available.
-
Click Save.
Head office: Turn on ping through VPN
- Go to Administration > Device access.
- Under Ping/Ping6, select the checkbox for VPN.
- Click Apply.
Head office: Outbound firewall rule
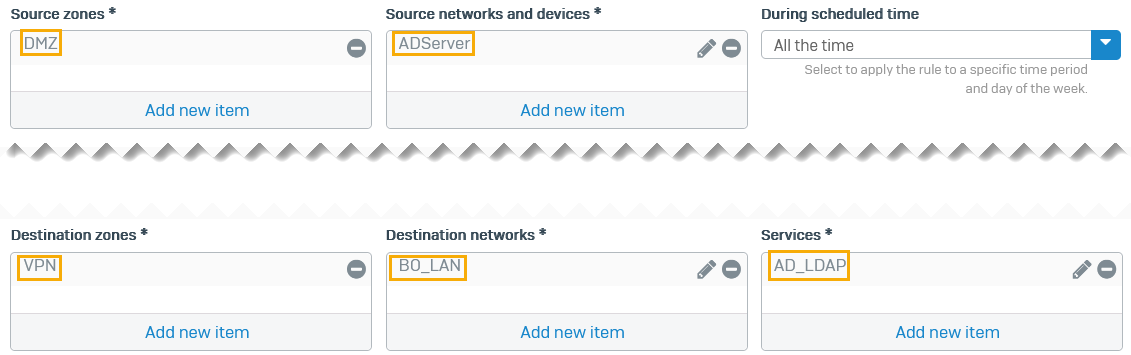
Configure a firewall rule to allow outbound traffic on the head office firewall. This allows the AD server to send its replies through the route-based VPN tunnel.
Select the following:
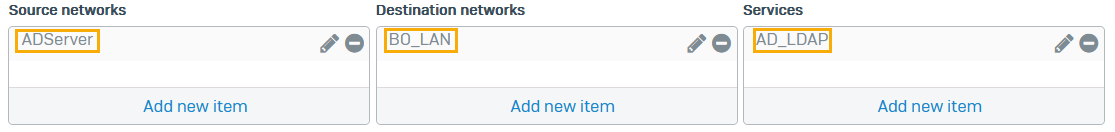
- Source zones:
DMZ - Source networks and devices:
ADServer - Destination zones:
VPN - Destination networks:
BO_LAN - Services:
AD_LDAP -
Click Save.
Here's an example:
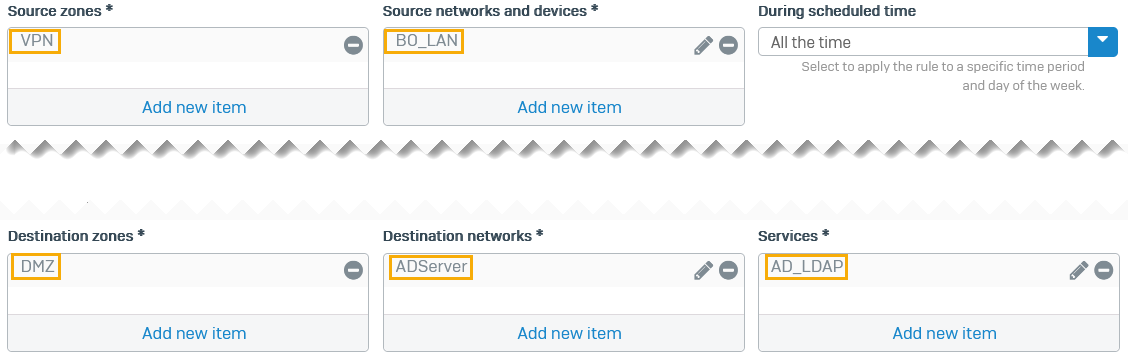
Head office: Inbound firewall rule
Configure a firewall rule to allow inbound traffic on the head office firewall. Authentication queries received through the route-based VPN tunnel are then sent to the AD server.
Select the following:
- Source zones:
VPN - Source networks and devices:
BO_LAN - Destination zones:
DMZ - Destination networks:
ADServer - Services:
AD_LDAP -
Click Save.
Here's an example: