Multi-factor authentication (MFA)
You can implement multi-factor authentication using hardware or software tokens.
For software tokens, users must scan the QR code on the user portal using an authenticator application on their mobile devices, such as the authenticator feature in Intercept X for Mobile.
Warning
Sophos Authenticator reached End of Life (EOL) on July 31, 2022.
We recommend that users migrate to another authenticator app, such as the authenticator feature in Intercept X for Mobile, Google Authenticator, or other apps. See Migrate to another authenticator application.
Multi-factor authentication (MFA) settings
You can configure MFA and apply it to users signing in to certain firewall services, such as the user portal and remote access VPN. The settings determine whether users can use software or hardware tokens.
You can also set the timestep (time period) for which passcodes remain valid.
See Multi-factor authentication (MFA) settings.
Issued tokens
You can manually configure tokens and see the list of users who've used the token.
Manually configure the secret
To manually configure the secret, click Add token (for hardware tokens) and configure the settings.
You can use the secret for software tokens if you turn on Generate OTP token with next sign-in under MFA settings.
Types of users and tokens
The list shows the issued tokens and their users as follows:
- Tokens you've manually configured without adding a user. You can add the user later.
- Users for whom you've manually configured a token. Example:
newuser -
Users and administrators who've scanned the QR code. Example:
adminandtestadministratorNote
Other administrators can't change the status, edit, or delete the default admin's (
admin) tokens. The default admin can turn on MFA for the account on Administration > Device access.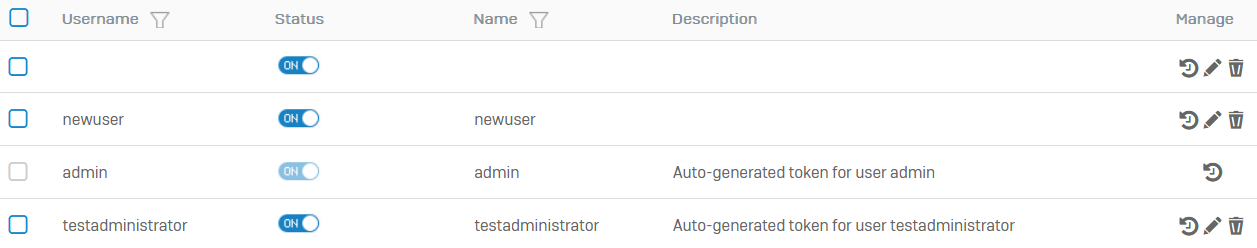
Actions
- Turn the status on or off to temporarily prevent the user from signing in.
- To manually generate passcodes for a user on the list, click the edit button
 . For Additional codes, click the add button
. For Additional codes, click the add button  .
. -
To check the authenticator app or hardware token's time offset and synchronize it with the firewall, do as follows:
- Click the Synchronize token time offset button
 .
. - Enter the generated passcode and click Check.
The time offset synchronizes. Synchronizing the token time between the app and the firewall corrects time drifts.
- Click the Synchronize token time offset button
Note
If you use the API to import MFA settings or tokens, you must include a blank <tokenid/> attribute.
Migrating to another app or losing account access
If a user loses a hardware token, delete the issued token and add a new token for the user.
If you want users to move to another authenticator app, or if they lose their mobile device, losing access to their account in the app, do as follows:
- Under Issued tokens, delete these users. The firewall will generate the QR code again.
- Users must scan the QR code again on the user portal.
See Migrate to another authenticator application.
More resources