Set up MTA mode with multiple WAN or alias IP addresses
In MTA mode for email delivery, if you have multiple WAN interfaces or public IP addresses, you must create an outbound rule to forward mails through one interface or IP address. You can have multiple interfaces or IP addresses to receive emails.
Depending on your WAN and IP address configuration, you must do as follows:
- If you have a single WAN interface with multiple alias IP addresses, configure an SNAT rule for SMTP with the specific public IP address you want to forward the traffic from.
- If you have multiple WAN interfaces and no alias IP addresses, configure an SD-WAN route for SMTP.
- If you have multiple WAN interfaces and alias IP addresses, configure both the SNAT rule and the SD-WAN route.
- For all scenarios, change the route precedence to: Static, VPN, SD-WAN.
Create a NAT rule for the SMTP and SMTPS services
Create an SNAT rule to translate outbound SMTP and SMTPS traffic flowing through the WAN interface you specify.
Do as follows:
- Go to Rules and policies > NAT rules.
- Select IPv4 or IPv6, click Add NAT rule, and click New NAT rule.
- Enter a name.
-
Specify the translation settings as follows:
Name Value Original source ANY Translated source (SNAT) Select MASQ or an alias IP address. Original destination ANY Translated destination (DNAT) Original Original service SMTP, SMTP(S), and SMTPS_465 Translated service (PAT) Original Inbound interface ANY Outbound interface Select the WAN interface through which you want the traffic to exit the firewall. -
Click Save.
Here's an example of a NAT rule for SMTP:
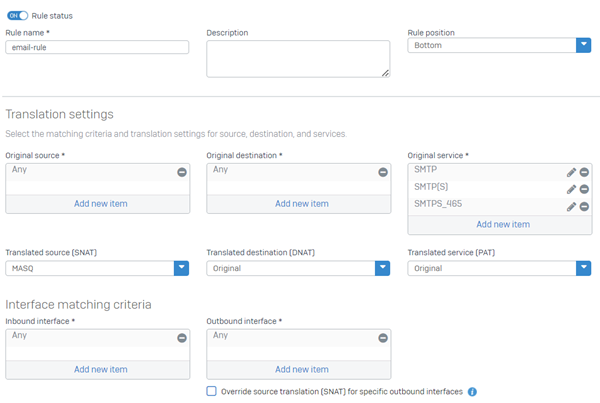
Create an SD-WAN route for the SMTP service
Create an SD-WAN route for the SMTP service.
Do as follows:
- Go to Routing > SD-WAN routes.
- Click IPv4 or IPv6 and click Add.
- Enter a name.
-
Select the traffic selector settings as follows:
Option Setting Incoming interface ANY DSCP marking Select a level to match incoming packets for priority. Source networks ANY Destination networks Internet IPv4 group Services SMTP, SMTP(S), and SMTPS_465 Application object ANY Users or groups ANY -
Under Link selection settings, select Primary and Backup gateways and select the primary gateway. The backup gateway is optional.
Note
If you select a backup gateway, make sure that the backup gateway can send outbound traffic through port 25 and you've added it to your Sender Policy Framework (SPF) record.
-
(Optional) Select Route only through specified gateways if you want to route traffic only using the gateways specified in this route. If these gateways are unreachable, the firewall drops the traffic.
Here's an example of an SD-WAN route for SMTP:
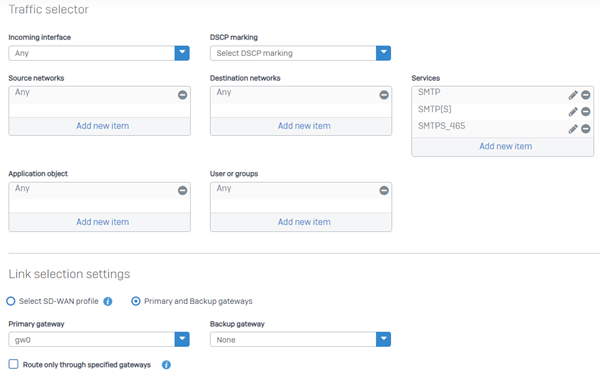
-
Click Save.
- Sign in to the command-line console of the firewall as the admin.
- Type
4for Device Console. -
Enter the following command:
set routing sd-wan-policy-route system-generate-traffic enable
Change the route precedence
Change the route precedence to: Static, VPN, SD-WAN.
Do as follows:
- Sign in to the command-line console of the firewall as the admin.
- Type
4for Device Console. -
To change the route precedence, enter the following command:
system route_precedence set static vpn sdwan_policyroute -
To verify if the route precedence has changed, enter the following command:
system route_precedence show
More resources