RED operation and LAN modes
You can define how the remote network behind the RED integrates into your local network with RED operation modes.
You can use the VLAN switch port configuration to configure LAN ports separately with LAN modes.
RED operation modes
The RED operation mode defines how the remote network behind the RED integrates into your local network.
On Wireless networks, if you set up REDs with Client traffic set to Separate zone, all the wireless traffic goes to Sophos Firewall using the VXLAN protocol regardless of the operation mode.
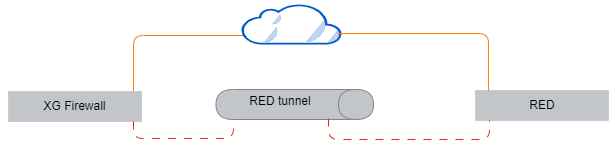
RED can operate in several modes. Sophos Firewall is deployed in your local network and the RED appliance in your remote network. The RED appliance establishes a tunnel with Sophos Firewall. Both have a connection to the internet. Here's an example:
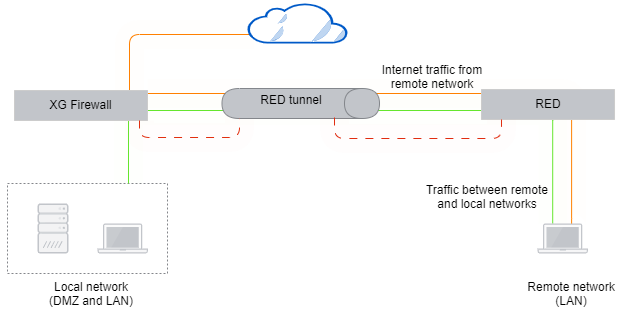
Standard/Unified
The firewall fully manages the remote network, which is managed as a remote LAN, through the RED. It acts as a DHCP server and default gateway.
In this mode, you can block or allow traffic between local and remote LANs using firewall rules. You can filter web traffic using the web security module, and you can control applications, such as Skype or BitTorrent, for local and remote LAN users. This provides the highest level of security and manageability for remote networks.
This mode may place increased bandwidth requirements on the firewall's internet link.
If the RED loses contact with Sophos Firewall and the tunnel fails, the RED stops routing traffic. Remote LAN users lose access to the internet and the firewall's internal networks until the tunnel can reconnect.
Note
Handle VLAN traffic through the Standard/Unified mode if VLAN is deployed behind the RED.
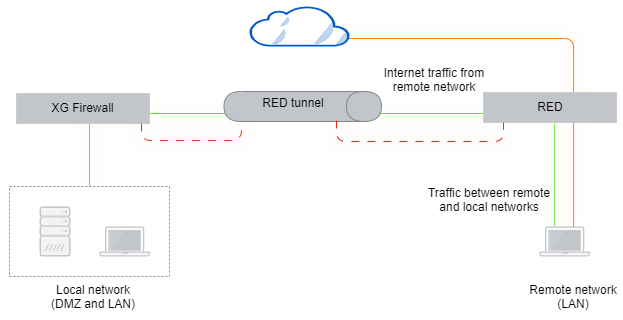
Standard/Split
The firewall manages the remote network and acts as a DHCP server. Only traffic targeted to split networks is redirected to your local firewall. All traffic not targeted to the split networks is directly routed to the internet.
Note
Only traffic from the RED's DHCP network can go to the internet.
In this mode, the RED masquerades outbound traffic to come from its public IP address. This feature minimizes bandwidth usage over the tunnel and lightens the bandwidth requirements on the firewall, but it also reduces the manageability of the remote network substantially. Traffic to or from the internet can't be filtered or protected from threats. Security can only be applied between the remote and local LANs.
If the RED loses contact with Sophos Firewall and the tunnel fails, the RED stops routing traffic. Remote LAN users lose access to the internet and the firewall's internal networks until the tunnel can reconnect.
Note
This mode isn't compatible with VLAN tagged frames.
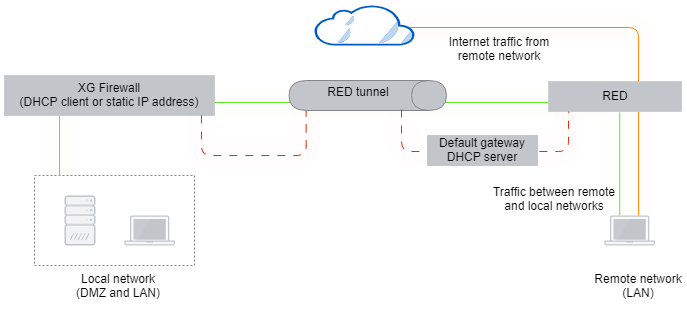
Transparent/Split
The firewall does not manage the remote network. It's connected to the remote LAN and the remote LAN's gateway and receives an address on the remote LAN through DHCP. Only traffic destined for certain networks transmits down the tunnel. In this case, the RED does not act as the gateway, but it's in-line with the gateway and can transparently redirect packets down the tunnel.
Since the firewall has no control of the remote network, local domains can only be resolved by the remote router if you define a split DNS server. This is a local DNS server on your network that can be queried by remote clients.
In this mode, the local interface of the RED and its uplink interface to your local firewall as well as its link to the remote router are bridged. Since the firewall is a client of the remote network, routing traffic to the split networks the same way as with other modes isn't possible. Therefore, the RED intercepts all traffic. Traffic targeting a split network or split domain is redirected to the firewall interface.
Note
This mode isn't compatible with VLAN tagged frames.
Manual/Split
You can set up this mode only through physical configuration. This mode allows the tunnel to go down without turning off local internet access. In this scenario, you configure the RED device in Standard/Unified mode but not place it in front of the remote LAN. You connect it to an alternate gateway on the remote LAN, and then add routes on the existing default gateway to access remote networks behind the RED.
You plug the WAN port into the same LAN switch that LAN clients are connected to, and once the RED receives its mode configuration, you connect a LAN port to the same LAN switch.
This setup is physically more complex than other modes, but is logically simpler, and allows for a tunnel or RED hardware failure, without disrupting normal internet traffic.
Bridged RED setup
If you have many RED devices, treat all remote RED networks as a single LAN. Create a single bridge interface on the firewall, bridging any number of NICs. You can bridge more than one RED connection together to treat all remote RED connections as a single LAN. You can use firewall rules to control access from RED to RED, so security isn't compromised in this setup.
To set up a bridge, do as follows:
- Add at least two RED devices to Sophos Firewall. See Set up a RED device manually.
- Go to Network > Interfaces, click Add interface, and click Add bridge.
- Enter a name and hardware name.
- Under Member interfaces, select the RED appliances and their zones.
- Click Save.
RED LAN modes
For REDs with more than one uplink, you can use the VLAN switch port configuration to configure LAN ports separately.
Untagged (hybrid port)
Ethernet frames with the VLAN IDs specified in the LAN VID(s) fields are sent to this port. The frames are sent without tags. So, endpoints don't have to support VLAN. This port allows one VLAN ID.
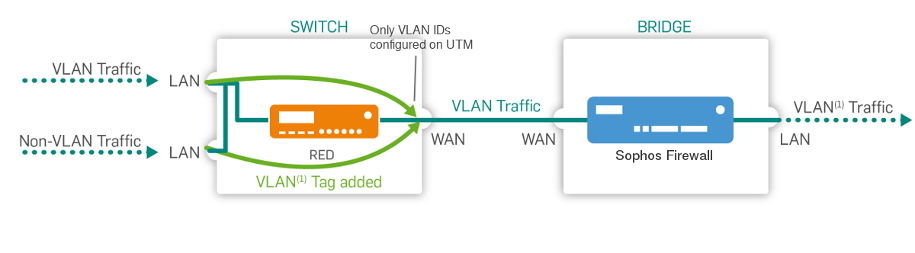
Untagged, drop tagged (access port)
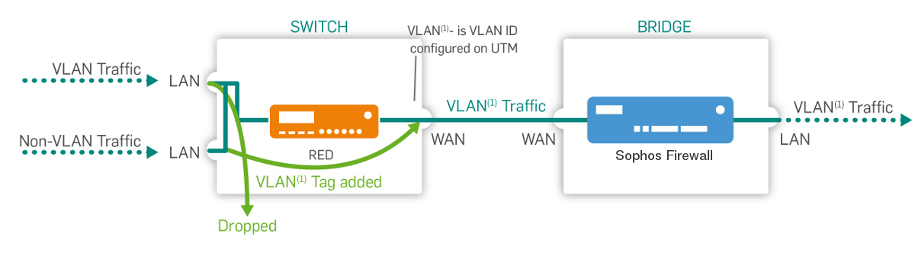
Ethernet frames with the VLAN IDs specified in the LAN VID(s) fields below aren't sent to this port. The frames are sent without tags. Therefore, endpoints don't have to support VLAN.
Tagged (trunk port)
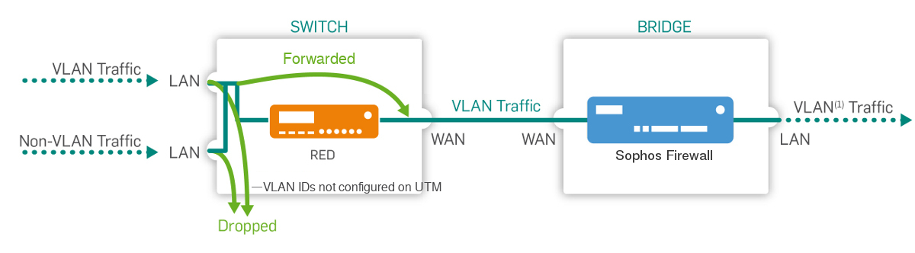
Ethernet frames with the VLAN IDs specified in the LAN VID(s) fields below are sent to this port. The frames are sent with tags, and the endpoints must support VLAN. Frames without VLAN IDs aren't sent to this port. This port allows up to 64 VLAN IDs. Separate the IDs using a comma.
Disabled
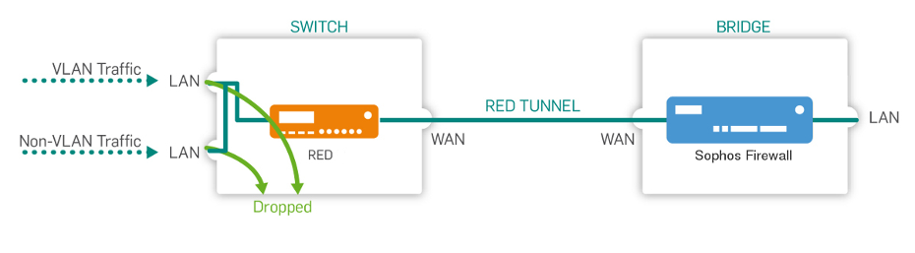
This port is closed. Ethernet frames with or without VLAN IDs specified in the LAN VID(s) fields aren't sent to this port.
More resources