Network behind firewall is unreachable
If the tunnel is established but request traffic from the endpoint doesn't reach the permitted network resource, check the following settings.
-
Scenario: Traffic flow
- Firewall to permitted resource
- Endpoint to permitted resource
To check if the client traffic reaches the firewall, see the following pages:
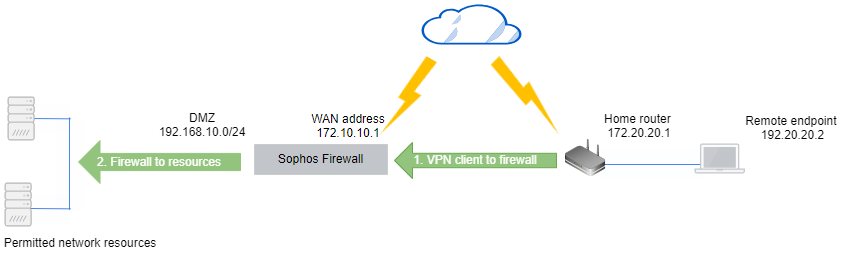
Traffic from endpoint to permitted resource
In the endpoint
The route is pushed to the endpoint after the tunnel is established. To check if the route is added, see the endpoint's routing table as follows:
- Enter the route command for your endpoint OS.
-
The route entry must have the following details:
- Destination IP address: Permitted network resource's address (example:
192.168.10.0). - Interface: The
tuninterface address. It's an IP address from the SSL VPN lease range (example:10.81.0.1). - Address assigned to the endpoint: An IP address from the SSL VPN lease range (example:
10.81.0.2).
- Destination IP address: Permitted network resource's address (example:
An example:
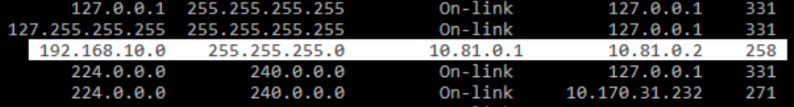
Route doesn't exist in the endpoint.
If you don't find the route in the endpoint, do as follows:
- Download and import the
.ovpnfile again to see if it resolves the issue. - Check the VPN client's log to know the issue.
- Check the endpoint permissions.
In the firewall
If the route exists in the endpoint, check the following parameters:
-
To check if SSL VPN traffic is arriving at the firewall, do as follows:
- Send a ping request from the endpoint to the permitted resource.
- Go to Diagnostics > Packet capture, and enter the following under BPF string:
host <Destination IP address> and port <SSL VPN port> or host <Leased IP address>Example
host 192.168.10.2 and port 8443 or host 10.81.0.2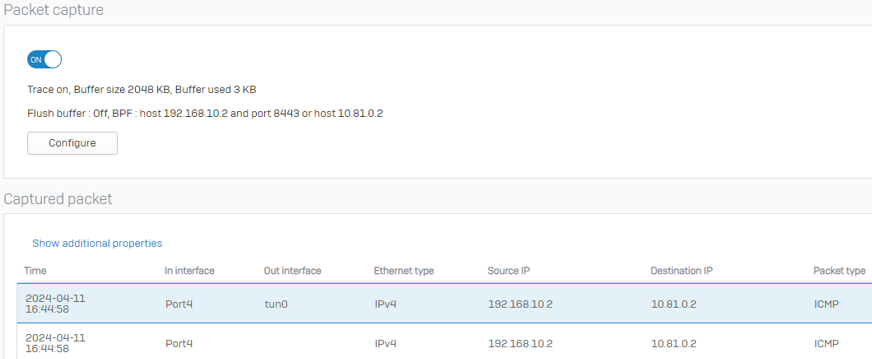
-
If you don't get the above result, check if the firewall can reach the resource:
- Temporarily turn on ping in the permitted network resource.
- Go to Diagnostics > Tools and send a ping from the firewall to the resource.
If there's no response, you must check your network topology.
Check the configurations
Check the following configurations.
Firewall rules
Firewall rule for SSL VPN
Make sure the firewall rule has the following settings:
- Source zones:
VPN - Source networks: The system hosts
##ALL_SSLVPN_RWor##ALL_SSLVPN_RW6. -
Destination zones: Select one of the following options:
- Any if you've turned on Default gateway in the SSL VPN policy.
- Zones to which the permitted network resources belong, for example, WAN, DMZ.
-
Destination networks: Select one of the following options:
- Any if you've turned on Default gateway in the SSL VPN policy.
- The permitted network resources you specified in the remote access SSL VPN policies.
-
Users and groups: If you specified resource access to specific users, make sure you added the users or groups as follows:
- Select Match known users.
- Add users or groups under User or groups.
Matches incorrect firewall rule
To check if traffic matches the correct firewall rule, do as follows:
- Go to Log viewer and select Firewall in the drop-down list.
-
Click Add filter and specify the following filters:
Setting Value Field In interface Condition Is Value tun
The firewall uses tun interfaces, such as tun0 and tun1, for SSL VPN traffic.
- Click Add filter.
- See the firewall rule ID under the Firewall rule column.
An example:
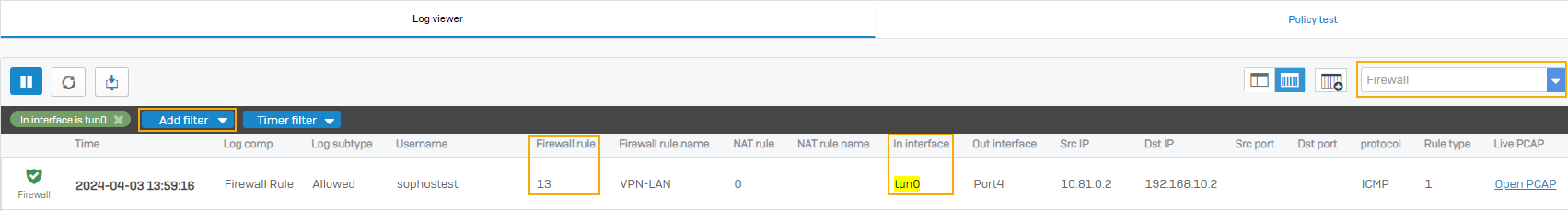
If an incorrect firewall rule is matched, take one of the following actions:
- Move it lower than the correct firewall rule in the firewall rule list.
- Change its Services setting to exclude SSL VPN's port-protocol combination.
SSL VPN configurations
SSL VPN global settings
Under Assign IP addresses, make sure the subnets don't overlap with the following addresses:
- An internal network.
- Any static route's destination IP address or network.
- Static peer IP addresses in site-to-site SSL VPN tunnels.
-
Commonly used home router subnets, such as
192.168.0.0/24,192.168.1.0/24,192.168.2.0/24,10.0.0.0,10.0.1.0, and10.1.1.0. -
Static IP addresses, if any, must be within the static IPv4 or IPv6 address range in SSL VPN global settings.
SSL VPN policy
- Go to Remote access VPN > SSL VPN.
- Make sure you added the correct users or groups to Policy members in the policy.
-
Under Permitted network resources, make sure you follow these guidelines:
- Even if you turned on Default gateway, select the network resources remote users can access.
- Don't select the interfaces. These don't ensure that users access the corresponding subnets.
- Check if you selected the correct resources.
Note
To apply the changes to SSL VPN policies, users must disconnect and reconnect the tunnel.
DNAT rule
If the permitted network resource IP address is the same as the home router's address, add a DNAT rule as follows:
- Original source: IP host with the SSL VPN lease range.
- Translated source:
Original - Original destination: A non-conflicting IP host address.
- Translated destination: Permitted network resource address.
DNS resolution
If users can't access permitted resources using their FQDN, check the following configurations:
- If the permitted resource is an FQDN, using dynamic IP addresses, remote users must manually disconnect and reconnect when the address changes.
- Make sure you configured the correct DNS server in SSL VPN global settings.
- Go to Administration > Device access and check if you allowed DNS over VPN.