VoIP troubleshooting
How to troubleshoot common issues with VoIP.
Connections and call quality
Audio and video calls are dropping or only work one way when H.323 helper module is loaded.
Cause
If the H.323 helper module is loaded along with proper firewall rules or DNAT rules, and audio or video continues to drop or only works one way, application-level NAT might not be occurring.
Remedy
- Connect to the firewall through the CLI console.
- Select Option 4 (Device Console).
-
Run the following command:
system system_modules h323 unload -
Configure a transparent subnet gateway. See Sophos Firewall: Implement transparent subnet gateways using proxy ARP.
- Start a video call from a Polycom device which is behind the firewall and check if it is functioning correctly.
VoIP calls drop or have poor quality.
Condition
UDP time-out value causes VoIP calls to drop or have poor quality.
Cause
Sophos Firewall has a default UDP time-out of 60 seconds, which can be low for reliable VoIP communication. We recommended a time-out value of 150 seconds. Check with your VoIP provider to see what they recommend for a UDP time-out value.
Remedy
Change the current UDP time-out value from the command line interface (CLI). Do as follows:
- Connect to the firewall through the CLI console.
- Select Option 4 (Device Console).
-
Enter the following command:
show advanced-firewallThe output shows the current UDP time-out value next to
UDP timeout stream.Here's an example:
console> show advanced-firewall Strict Policy : on FtpBounce Prevention : control Tcp Conn. Establishment Idle Timeout : 10800 UDP Timeout : 30 UDP Timeout Stream : 60 ... -
Enter the following command to increase the UDP time-out to 150 seconds:
set advanced-firewall udp-timeout-stream 150
If your provider recommends a different value, use that.
Unstable VoIP connection if DoS settings for UDP rate are applied.
Cause
UDP flood settings cause VoIP traffic to drop.
Remedy
- Sign in to the web admin console.
- Go to Intrusion prevention > DoS & spoof protection.
- Under DoS settings, clear the Apply flag checkboxes for UDP flood.
- Test the VoIP connection.
-
If this setting resolves the VoIP issue, lower the UDP flood protection values before applying the flag again.
A single value only works for some environments. Adjust the values until you find the best for your VoIP setup.
External users are unable to make voice calls from outside the network.
Cause
The firewall supports SIP media ports in the range 1024-65535 with its SIP helper module. The default port is UDP 5060.
If you load the firewall's SIP helper and set a media port outside this range, the firewall drops the packets, and VoIP calls may not connect. Event logs show the cause as Invalid Traffic.
Remedy
- Sign in to the CLI and enter 4 for Device Console.
-
Change the SIP port using the following command:
system system_modules sip load ports <custom_port>
VPN and IPS-related issues
The phone rings, but there's no audio.
Condition
You can place a call, and the receiving phone rings, but you don't hear any audio.
Cause
This condition occurs if the caller can't send data at the RTP stage of a SIP connection. This often happens when using a VPN or the Sophos Connect client.
Here's an example of this condition where Alice is the caller and Boris is the recipient.
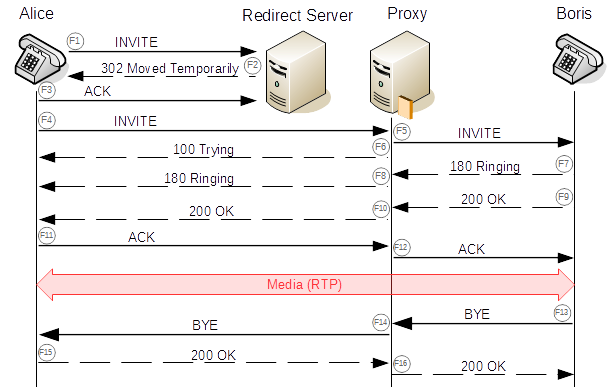
Remedy
- Go to Rules and policies > Firewall rules.
- Make sure you've configured a firewall rule for SIP.
- Make sure you select the recipient's network in Destination networks. Set the recipient's network to Any if you want to call any phone.
VoIP call issues over site-to-site VPN or with IPS configured.
Cause
Site-to-site VPN, IPS, or both on your firewall cause dropped or poor-quality VoIP calls.
Remedy
- Connect to the firewall through the CLI console.
- Select Option 4 (Device Console).
-
Enter the following command to turn off the preloaded IPS patterns for SIP:
set ips sip_preproc disable -
When IPS patterns are turned off, the firewall does not flush the connections when IPsec tunnels come up. Enter the following command:
set vpn conn-remove-tunnel-up disable
Other issues
VoIP phones register with PBX using the IP address of the firewall.
Condition
Some phones register with your PBX server with the IP address of the firewall instead of the phone's IP address.
For example, a phone with an IP address 192.168.20.12 registers with the IP address 192.168.1.5.
Cause
Conntrack needs to be cleared.
Remedy
- Click Log viewer.
- Click Add filter.
-
Specify the following values:
- Field: Dst IP.
- Condition: Is.
- Value: Enter the IP address of your PBX server.
-
Click Add filter.
-
Confirm that traffic to your PBX server for both working and non-working phones uses the correct firewall rule.
-
Go to Rules and policies > Firewall Rules and find the firewall rule that manages your VoIP traffic.
- Confirm that the firewall rule allows your phone's VoIP protocol, either SIP or H323.
-
Go to Rules and policies > Firewall Rules > NAT rules and confirm the correct NAT rules are in place and no conflicts exist.
-
Connect to the firewall through the CLI console.
- Select Option 4 (Device Console).
-
Run the following command to check the SIP helper status:
system system_modules showIf the SIP module shows as loaded, turn it off using the following command:
system system_modules sip unload -
Type exit to exit the device console and return to the main CLI menu.
- Select 5. Device management, then select 3. Advanced Shell.
-
Delete the conntrack entry corresponding to the wrong IP address used by the phone using the following command:
conntrack -D --src <IP ADDRESS OF PHONE> --dst <IP ADDRESS OF PBX> -p tcp