Create Port Address Translation (PAT) rule for traffic to internal servers
This example shows how to create a many-to-many destination NAT rule with port translation for incoming traffic to internal servers. It also shows how to create firewall rules to allow the traffic.
Objectives
When you complete this unit, you'll know how to do the following:
- Create a destination NAT rule to translate traffic from external sources to the internal servers.
- Specify a loopback NAT rule to translate traffic from internal sources to the internal servers.
- Specify a reflexive NAT rule to translate traffic from the servers. This is a source NAT rule for the internal servers.
- Load balance traffic among the internal servers.
DNAT network diagram
Destination NAT is typically used to translate incoming traffic that reaches the WAN IP addresses. The following network information is illustrative:
- Pre-NAT IP address of web servers:
11.8.9.28 - Post-NAT IP addresses of web servers:
10.145.15.42, 10.145.15.114
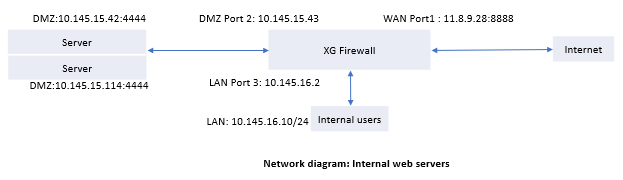
Here's an example:
- Destination NAT from external source to internal web servers with port translation:
AnytoWeb server public IP address (11.8.9.28)translated toWeb server internal IP list(10.145.15.42, 10.145.15.114) with port translation fromTCP 8888toTCP 4444. - Loopback rule to translate traffic from internal source to internal web servers:
Network LAN(10.145.16.10/24) toWeb server public IP address (11.8.9.28)translated toWeb server internal IP list(10.145.15.42, 10.145.15.114) with port translation fromTCP 8888toTCP 4444. - Reflexive rule to translate traffic from the web server to external and internal destinations:
Web server internal IP list(10.145.15.42, 10.145.15.114) toAny. - Load balancing method for the web servers.
- Firewall rule to allow traffic from external networks to the internal web servers in DMZ.
- Firewall rule to allow traffic from an internal network to the internal web servers.
- Firewall rule to allow traffic from the internal web servers to any network.
Specify the NAT rule settings
- Go to Rules and policies > NAT rules, select IPv4 or IPv6 and click Add NAT rule.
- Specify the rule name and rule position.
-
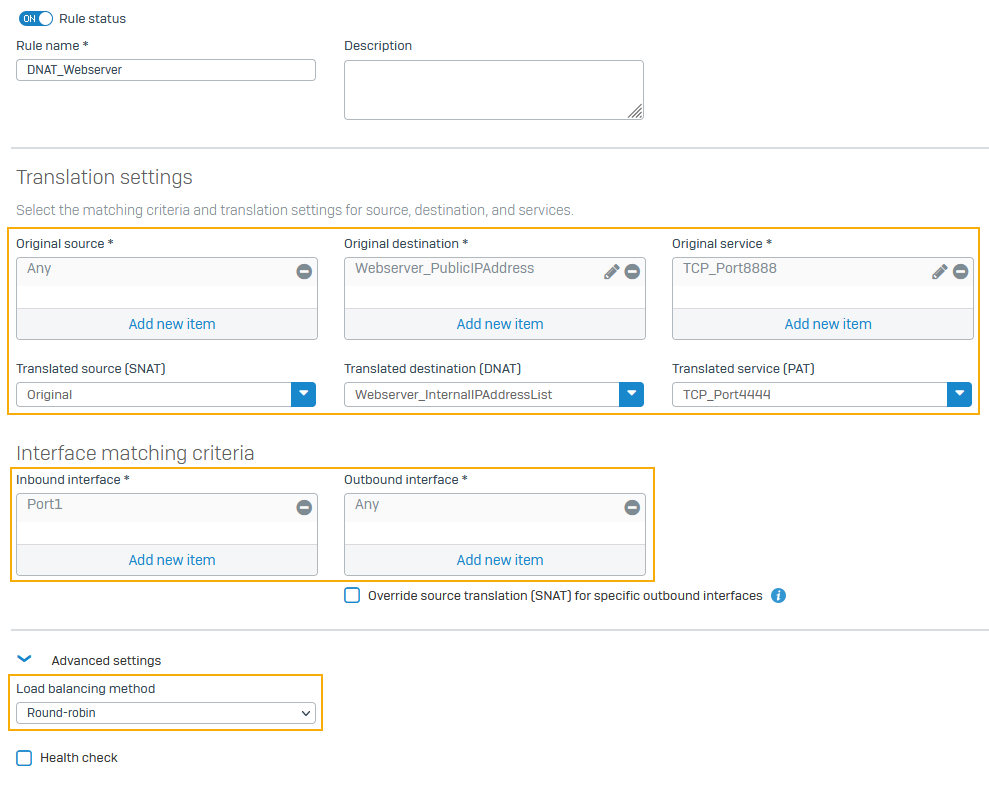
In this example, specify the translation settings for incoming traffic to the web servers:
Setting Value Original source AnyTranslated source (SNAT) MASQOriginal destination Webserver_PublicIPAddressTranslated destination (DNAT) Webserver_InternalIPAddressListOriginal service TCP port 8888Select Create new and set Destination port to
8888.Translated service (PAT) TCP port 4444Select Create new and set Destination port to
4444.Inbound interface Select the WAN interface.
In this example, it's
Port1.Outbound interface Any -
Select Create loopback rule to translate traffic from internal users to the internal web servers.
- Select Create reflexive rule to create a source NAT rule that translates traffic from the web servers.
- Select a load balancing method to load balance traffic between the web servers. In this example, you select
Round-robin. -
Click Save.
The following image shows an example of how to configure the settings:
Create firewall rules to allow traffic that matches the destination NAT rule, loopback rule, and reflexive NAT rule.
Specify firewall rule settings for the DNAT rule
- Go to Rules and policies > Firewall rules. Select protocol IPv4 or IPv6 and select Add firewall rule. Select New firewall rule.
- Specify the rule name and rule position.
-
Specify the source, destination, and services as follows:
Setting Value Source zones WANSource networks and devices AnyDestination zones DMZ
Select the zone containing your web servers.
Sophos Firewall looks up the matching DNAT rule for the traffic. It identifies the zone containing the translated destination, which is DMZ in this example. It uses DMZ as the destination zone when it matches a firewall rule.Destination networks Webserver PublicIPAddressServices TCP port 8888,TCP port 4444 -
Specify the security settings and click Save.
The following image shows an example of how to configure the settings:
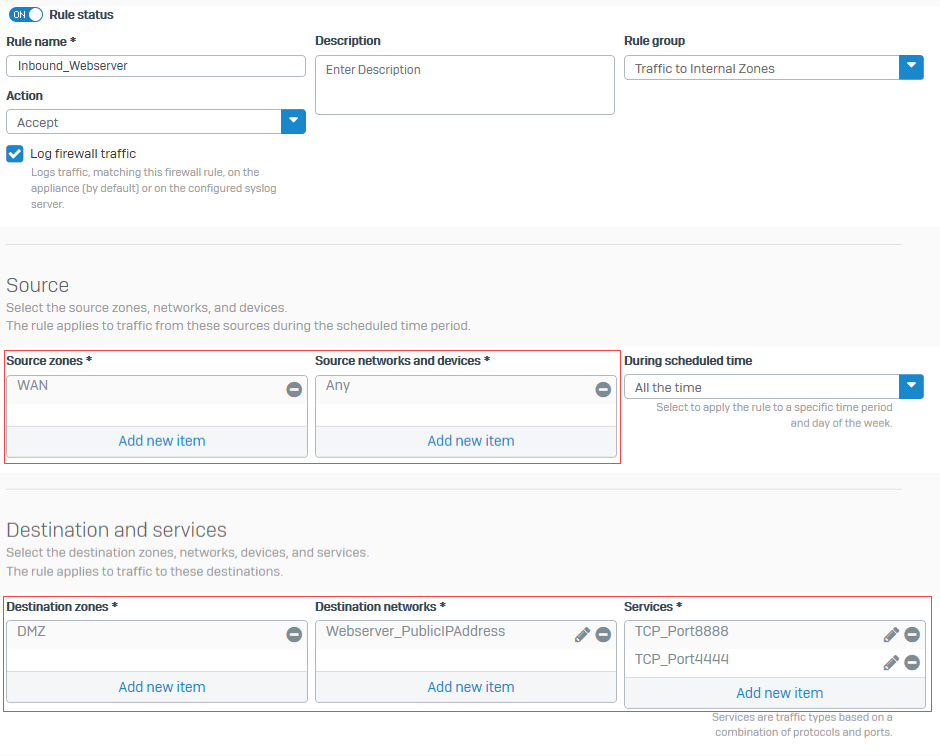
You created a firewall rule to allow traffic from external sources to the internal web servers.
Specify firewall rule settings for the loopback rule
- Go to Rules and policies > Firewall rules. Select protocol IPv4 or IPv6 and select Add firewall rule. Select New firewall rule.
- Specify the rule name and rule position.
-
Specify the source, destination, and services as follows:
Setting Value Source zones LANSource networks and devices Network_LANDestination zones DMZDestination networks Webserver PublicIPAddressServices TCP port 8888,TCP port 4444 -
Specify the security settings and click Save.
The following image shows an example of how to configure the settings:
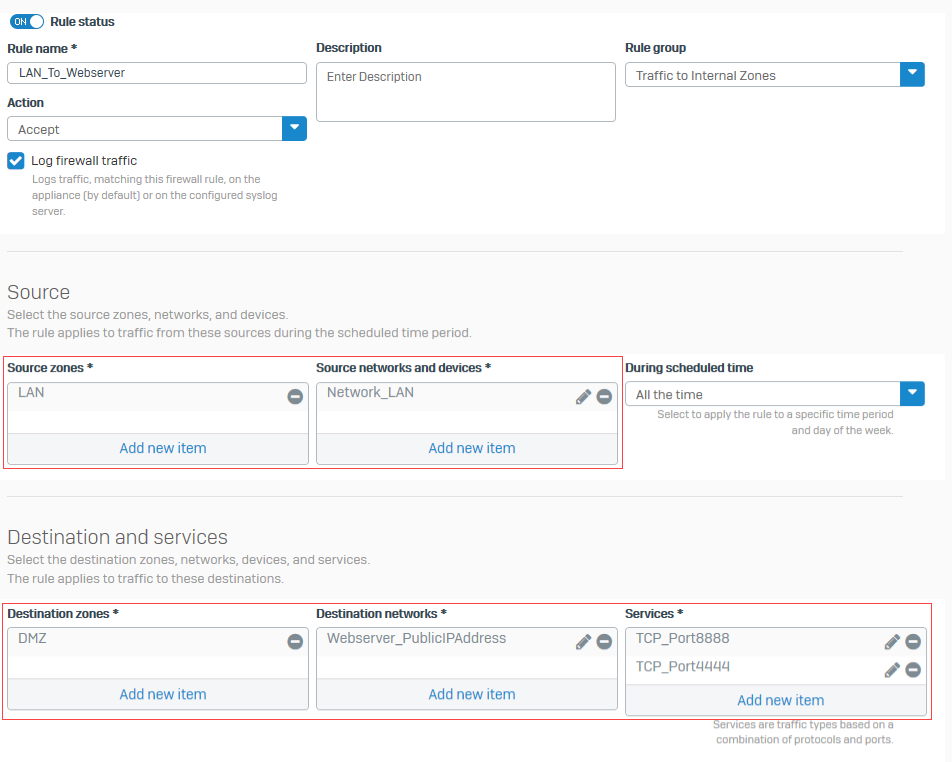
You created a firewall rule to allow traffic from the internal network to the internal web servers.
Specify firewall rule settings for reflexive NAT rule
- Go to Rules and policies > Firewall rules. Select protocol IPv4 or IPv6 and select Add firewall rule. Select New firewall rule.
- Specify the rule name and rule position.
-
Specify the source, destination, and services as follows:
Setting Value Source zones DMZSource networks and devices Webserver InternalIPAddressListDestination zones AnyDestination networks AnyServices TCP port 8888,TCP port 4444 -
Specify the security settings and click Save.
The following image shows an example of how to configure the settings:
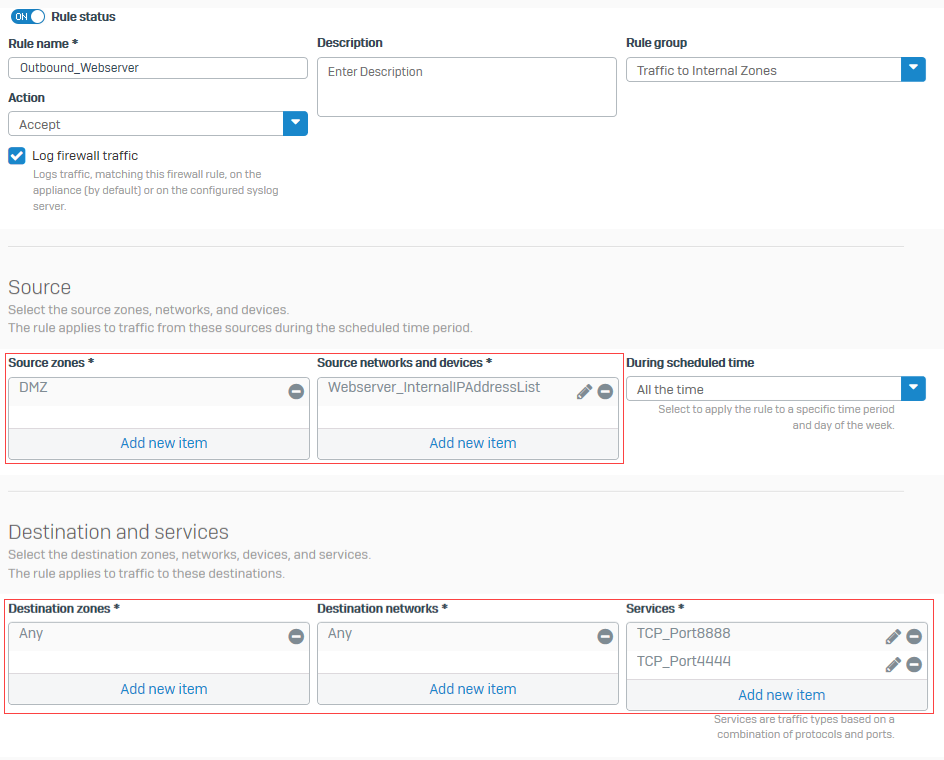
You created a firewall rule to allow traffic from the internal web servers to internal and external networks.
More resources