Create an Amazon VPC site-to-site connection
You can create a site-to-site VPN connection between your local network and Amazon Virtual Private Cloud (VPC).
Introduction
In this example, you'll import the AWS site-to-site VPN connection settings and establish a connection to Amazon VPC. This example uses the Amazon VPC configuration file to import the settings and BGP for dynamic routing. Here's the network schema:
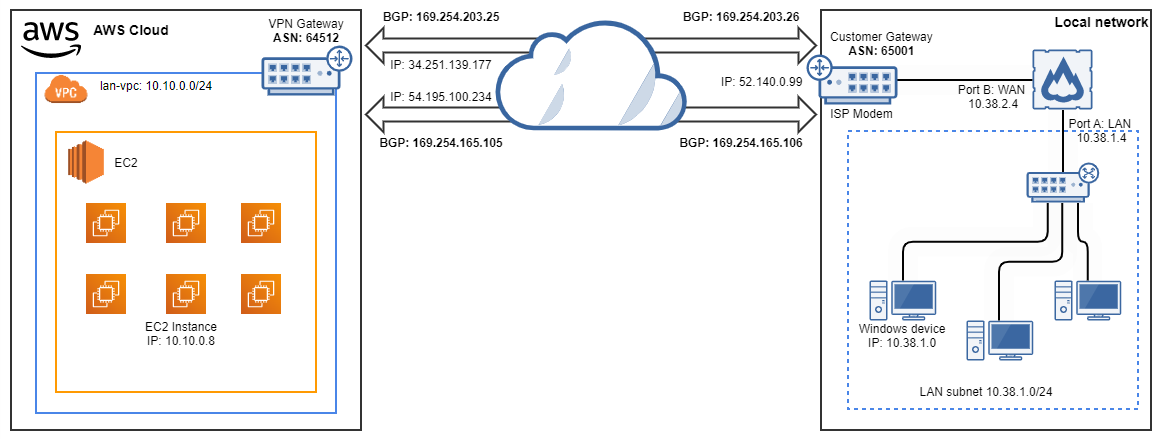
Prerequisites
Warning
This information was correct at the time of writing. To ensure you're following the most current steps, review the Amazon documentation. See the following:
Before you connect Amazon VPC to Sophos Firewall, you must set up an AWS site-to-site VPN connection on the Amazon VPC console.
If you want to use dynamic routing, your AWS site-to-site VPN connection settings must include the following:
- You must configure Local IPv4 Network Cidr and Remote IPv4 Network Cidr as
0.0.0.0/0to establish BGP peering. -
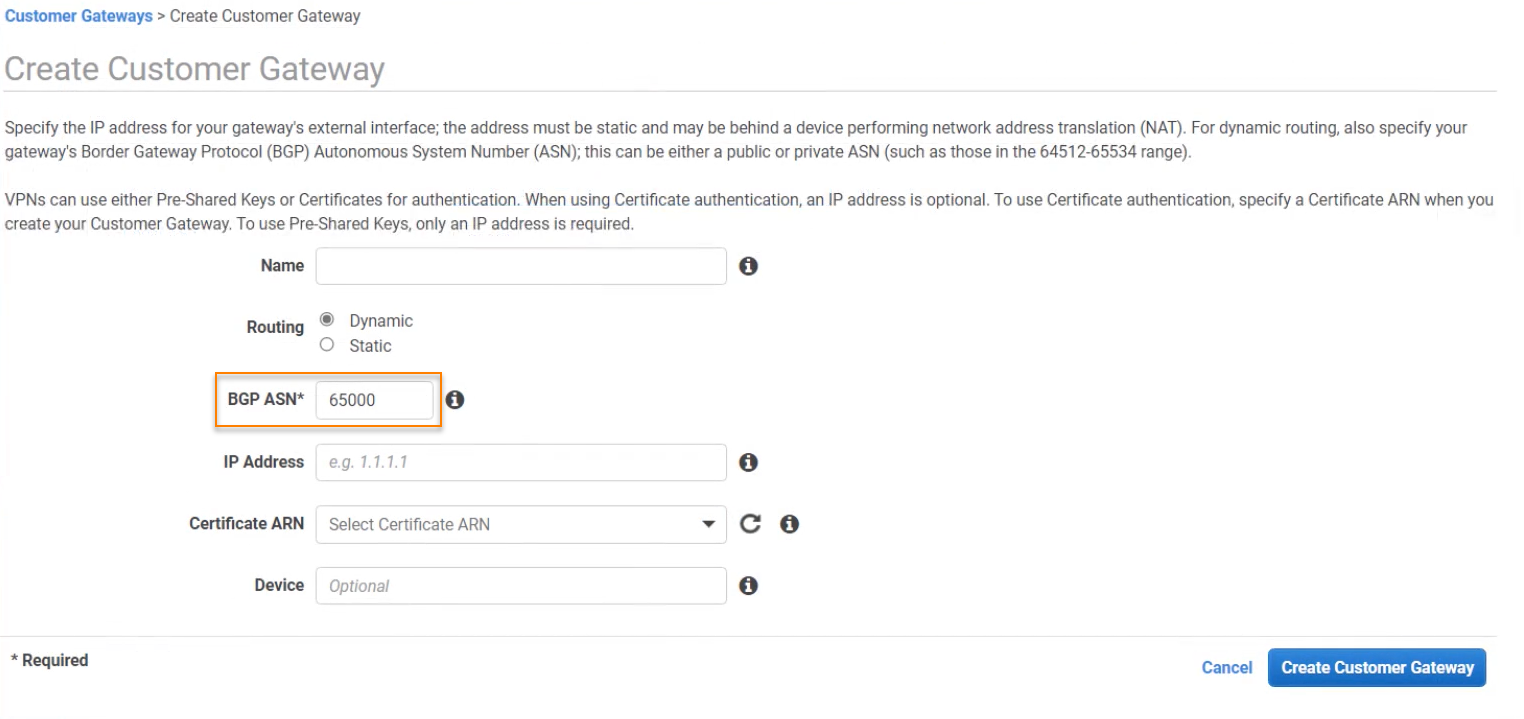
If you've already configured BGP on Sophos Firewall on Routing > BGP > Global configuration, you must enter your firewall's preconfigured Local AS value in the BGP ASN field on the Create Customer Gateway page in AWS.
Here's an example:
Note
If the BGP configuration includes “no bgp default ipv4-unicast” in the BGP CLI. Then the BGP peering won't automatically form.
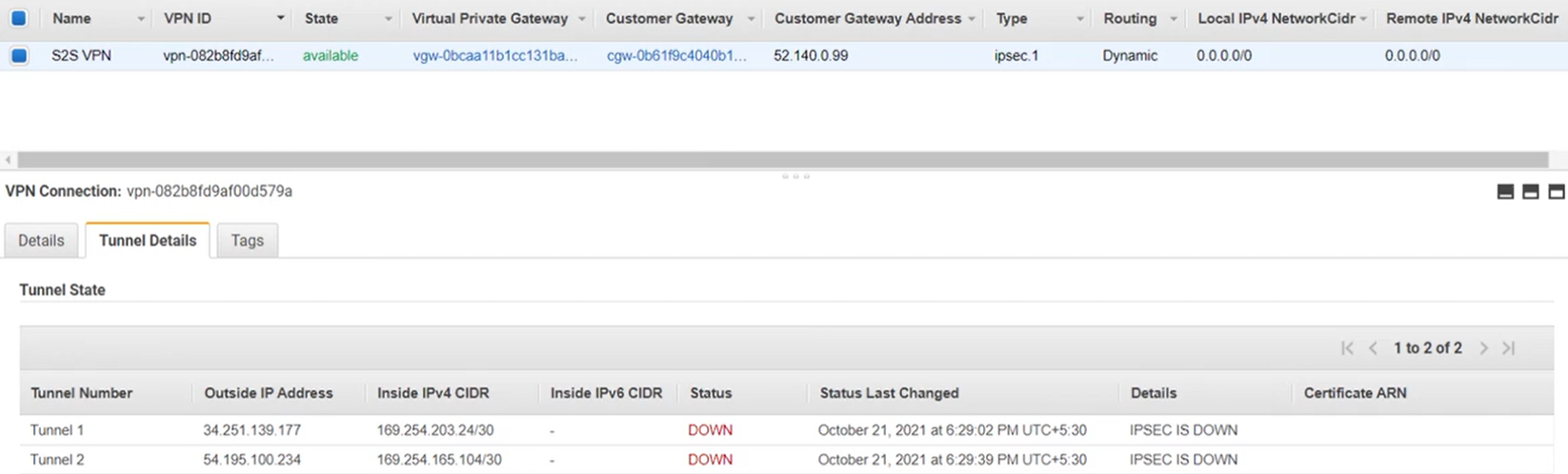
In this example, we've configured an Amazon site-to-site VPN connection with the following settings:
| Setting | Value |
|---|---|
| Name | S2S VPN |
| Customer Gateway Address | 52.140.0.99 |
| Type | ipsec1 |
| Routing | Dynamic |
| Local IPv4 Network Cidr | 0.0.0.0/0 |
| Remote IPv4 Network Cidr | 0.0.0.0/0 |
Here's an example of the site-to-site VPN settings and the tunnel configuration settings:
Download the Amazon VPC configuration file
You must download the Amazon site-to-site VPN settings as a configuration file so that you can import them into your firewall. Do as follows:
- Open the Amazon VPC console.
- Go to VIRTUAL PRIVATE NETWORK (VPN) > Site-to-Site VPN Connections.
- Select S2S VPN.
- Click Download Configuration.
-
Choose the following settings and click Download:
Setting Value Vendor Sophos Platform Sophos Firewall Software v19+ Ike Version ikev2 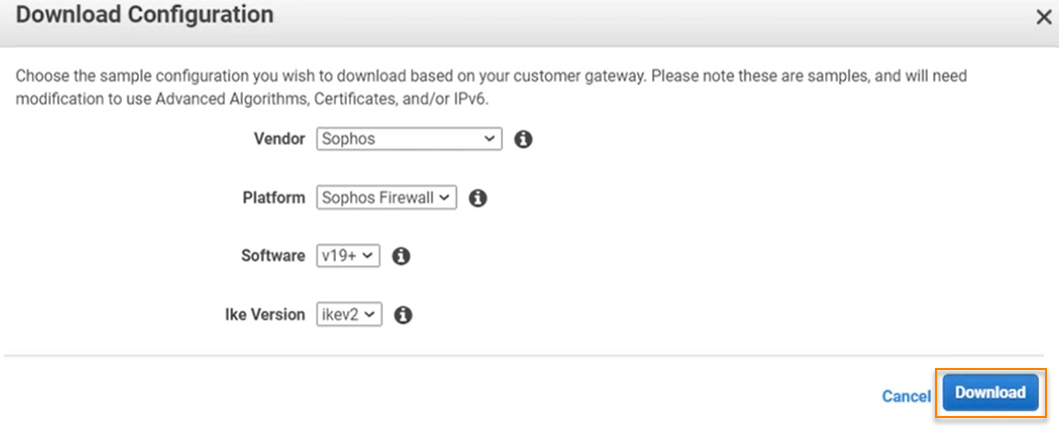
Customize the configuration file
The configuration file is only an example and may not match your intended site-to-site VPN connection settings. You must change the example configuration file to take advantage of additional security algorithms, Diffie-Hellman groups, private certificates, and IPv6 traffic.
In this example, the firewall is behind the ISP modem so you must change the tunnel_outside_address value to match the IP address of the WAN interface of your firewall. Do as follows:
-
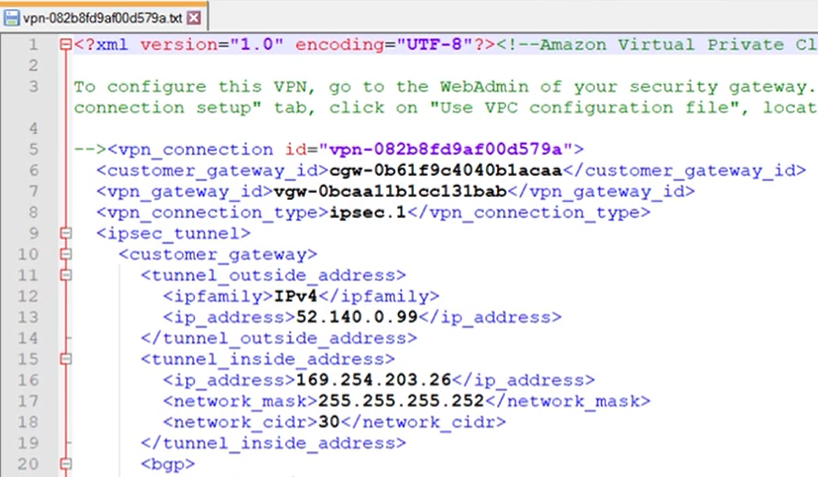
Open the VPC configuration file in a text editor.
Here's an example:
-
Locate the following lines:
<tunnel_outside_address> <ipfamily>IPv4</ipfamily> <ip_address>52.140.0.99</ip_address> </tunnel_outside_address>Note
In this example, these lines appear twice since two tunnels are configured on the VPC console. Each tunnel has its own configuration within a single AWS site-to-site VPN example configuration file. You must change the settings for each tunnel.
-
Change both occurrences of
ip_addressto10.38.2.4. They must match the IP address of the WAN interface of your firewall:<ip_address>10.38.2.4</ip_address> -
Save the changes and exit.
Import the Amazon VPC settings into Sophos Firewall
To import the configuration file into Sophos Firewall, do as follows:
- Sign in to Sophos Firewall.
- Go to Site-to-site VPN > Amazon VPC.
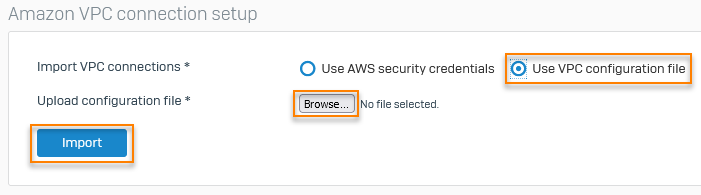
- Choose Use VPC configuration file.
- Click Browse.
- Choose the configuration file and click Open.
-
Click Import.
Sophos Firewall automatically creates the IPsec profiles, BGP settings, and XFRM interfaces using the settings imported from the configuration file. The connections appear in Amazon VPC connections and are automatically activated. For information about locating and confirming the automatically created settings, see the following documents:
Add the local subnet to BGP networks
To establish BGP routes between your network and Amazon VPC, you must add the local subnet to your BGP networks. Do as follows:
- Go to Routing > BGP > Networks.
- Click Add.
- For IPv4/netmask, enter
10.38.1.0. - Select /24(255.255.255.0) from the drop-down menu.
- Click Save.
Turn on dynamic routing for the VPN zone
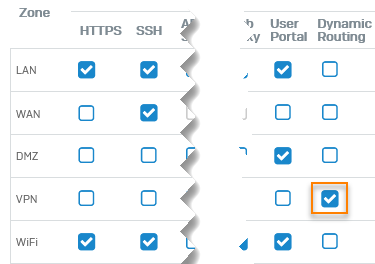
You must turn on dynamic routing for the VPN zone for Sophos Firewall to use BGP routing with Amazon VPC. Do as follows:
- Go to Administration > Device Access.
-
Select Dynamic Routing for the VPN zone.
-
Click Apply.
Create IP hosts
You must create IP hosts for the local and remote subnets that will use this connection so you can select them for firewall rules.
To create IP hosts for your subnets, do as follows:
- Go to Hosts and services > IP host and click Add.
-
Specify the settings.
Setting Value Name lan-local IP version IPv4 Type Network IP Address 10.38.1.0 Subnet /24(255.255.255.0) -
Click Save.
- Click Add.
-
Specify the settings.
Setting Value Name lan-vpc IP version IPv4 Type Network IP Address 10.10.0.0 Subnet /24(255.255.255.0) -
Click Save.
Create firewall rules for VPN traffic
You must create outbound and inbound firewall rules to allow traffic between your local network and Amazon VPC.
To create a firewall rule for outbound VPN traffic, do as follows:
- Go to Rules and policies > Firewall rules.
- Click IPv4, click Add firewall rule, and click New firewall rule.
- Enter
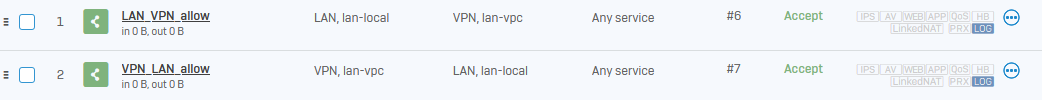
LAN_VPN_allowin the Rule name field and select Log firewall traffic. -
Specify the settings.
Setting Value Source zones LAN Source networks and devices lan-local Destination zones VPN Destination networks lan-vpc Services Any -
Click Save.
To create a firewall rule for inbound VPN traffic, do as follows:
- Click IPv4, click Add firewall rule, and click New firewall rule.
- Enter
VPN_LAN_allowin the Rule name field and select Log firewall traffic. -
Specify the settings.
Setting Value Source zones VPN Source networks and devices lan-vpc Destination zones LAN Destination networks lan-local Services Any -
Click Save.
Here's an example:
Confirm the tunnel status
You can check the tunnel status on Sophos Firewall and the AWS VPC console.
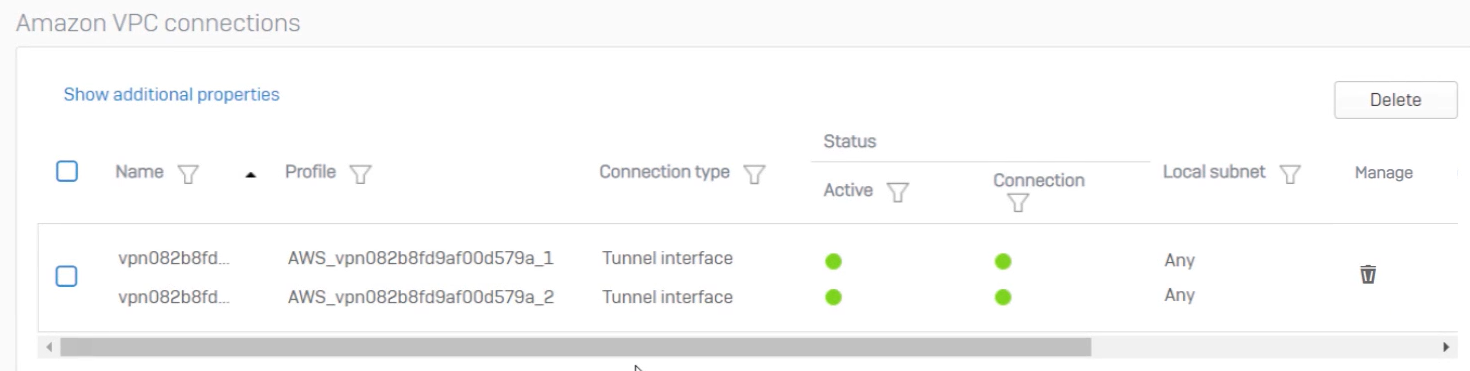
- Go to Site-to-site VPN > Amazon VPC > Amazon VPC connections.
-
Confirm that the tunnels are active and connected. This happens automatically when you import the AWS site-to-site VPN settings.
Here's an example:
-
Go to Routing > Information > BGP.
-
Select from the following:
Option Description Neighbors Shows the BGP neighbor details. Routes Shows the dynamically-learned routes. Summary Shows the BGP peer IP address information, uptime, and messages sent and received.
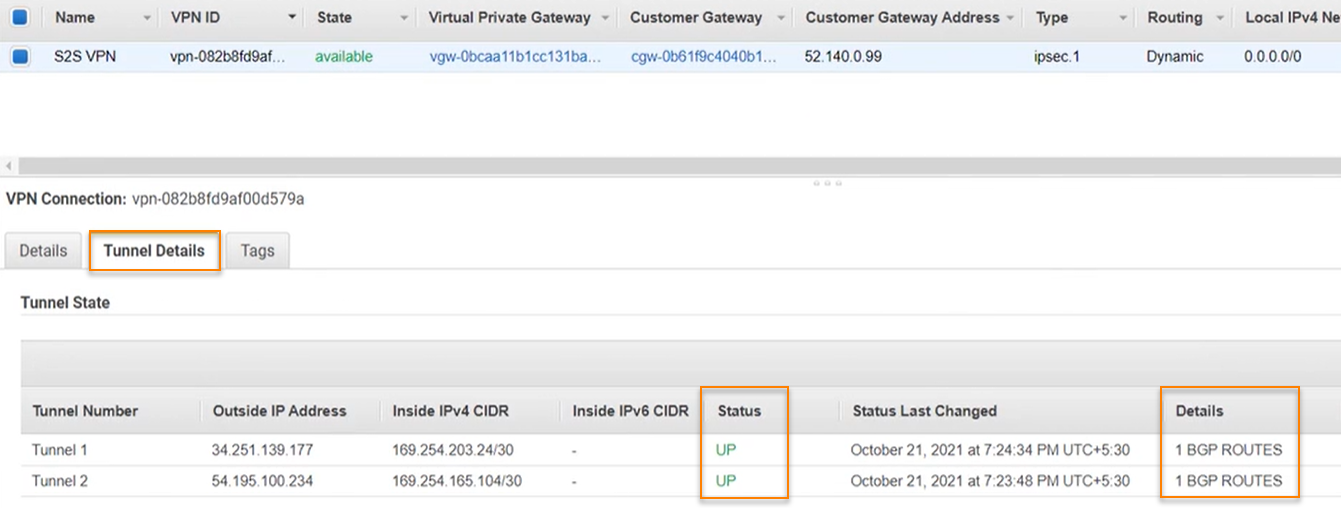
- Go to VIRTUAL PRIVATE NETWORK (VPN) > Site-to-Site VPN Connections.
- Select S2S VPN.
- Click Tunnel Details.
-
Confirm that Status is 'UP' and that BGP routes are established.
Here's an example:
Generate traffic
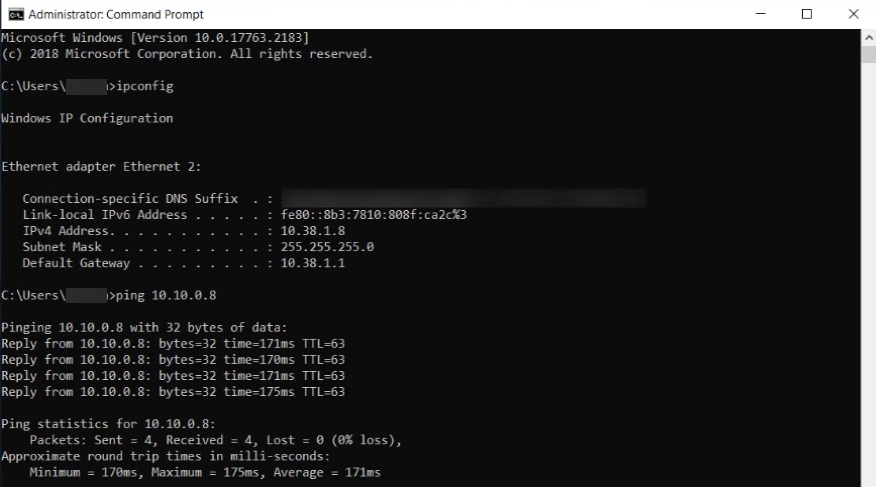
You can confirm that traffic is flowing through the VPC connection by sending a ping to an Amazon VPC resource from a device on your local network. The following example shows a successful ping from 10.38.1.8 on the local network to 10.10.0.8 in Amazon VPC.
More information