Add subordinate and root CAs for TLS traffic
This example shows how to generate the Certificate Signing Request (CSR) in Sophos Firewall and the subordinate Certificate Authority (CA) in Active Directory Certificate Services (AD CS) in Enterprise CA mode.
Note
You can't use this example if you have AD CS in Standalone CA mode.
Alternatively, you can use a third-party tool, such as OpenSSL, to generate the CSR and CAs. You must upload subordinate and root CAs generated through third-party tools on Certificates > Certificate authorities. See Add a CA.
You can use the subordinate CA as the signing CA for SSL/TLS inspection, HTTPS decryption, and TLS configurations for emails.
Do as follows:
- Generate a CSR.
- Generate a subordinate CA and download the subordinate and root CAs.
- Import the subordinate CA to Sophos Firewall.
- Upload the root CA to Sophos Firewall.
- Apply the subordinate CA.
Generate a CSR
- Go to Certificates > Certificates and click Add.
-
For Action, select Generate certificate signing request (CSR).

-
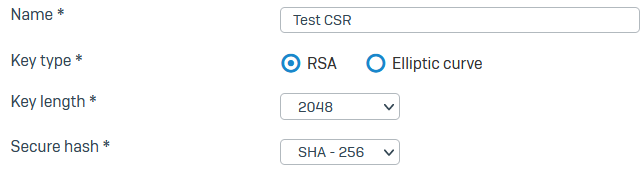
Specify the following Certificate details:
- Enter a name.
- Key type (example: RSA)
- Key length (example: 2048)
-
Secure hash (example: SHA - 256)
Here's an example:
-
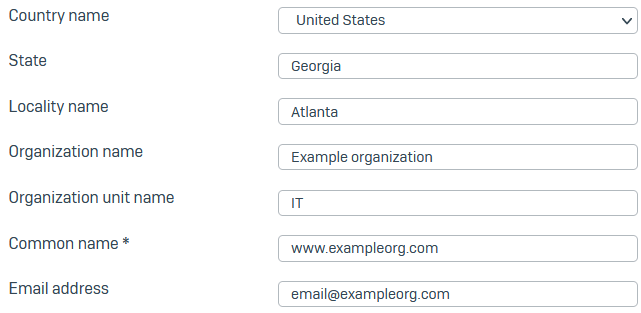
Specify the following Subject name attributes:
- Country name (example: United States)
- State (example: Georgia)
- Locality name (example: Atlanta)
- Organization name (example: Example organization)
- Organization unit name (example: IT)
- Common name (example: www.exampleorg.com)
-
Email address (example: email@exampleorg.com)
Here's an example:
-
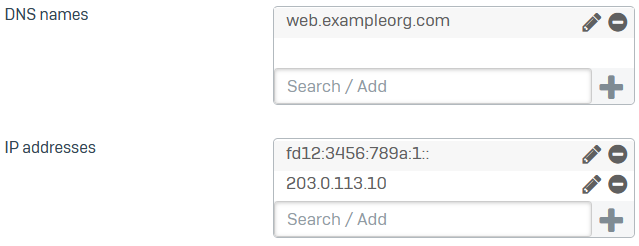
For Subject Alternative Names, enter DNS names or IP addresses.
Examples: web.exampleorg.com, fd12:3456:789a:1::, 203.0.113.10
-
Click Save.
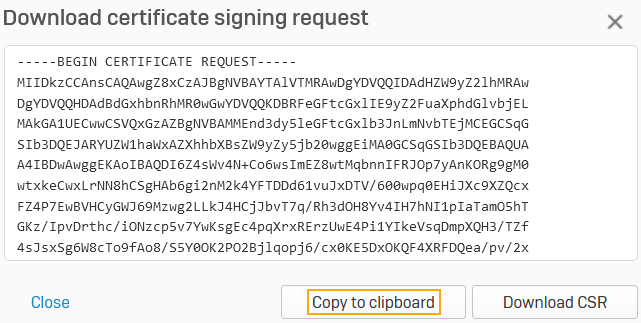
- Download the CSR as follows:
- Click the download button
 for the CSR you created.
for the CSR you created. -
In the pop-up window, click Copy to clipboard.
Here's an example:
- Click the download button
Generate a subordinate CA in Active Directory Certificate Services
You must generate a subordinate CA based on the CSR. This example uses AD CS in Enterprise CA mode.
-
In AD CS, do as follows to generate a subordinate CA.
-
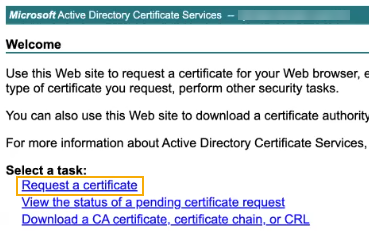
Click Request a certificate.
-
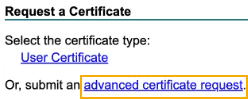
Click Advanced certificate request.
-
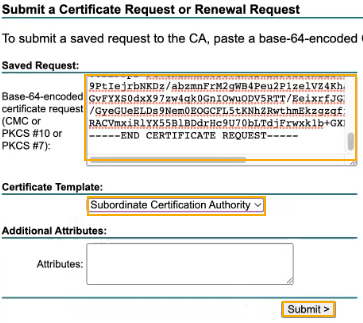
Paste the CSR certificate you copied.
- For Certificate template, select Subordinate Certification Authority.
-
Click Submit.
Here's an example:
-
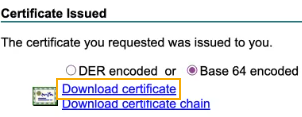
Under Certificate Issued, select an encoding format.
This example selects the Base 64 encoded format.
-
Click Download certificate to download the subordinate CA certificate.
-
-
Do as follows to download the root CA certificate:
-
On the welcome page, click Download a CA certificate.
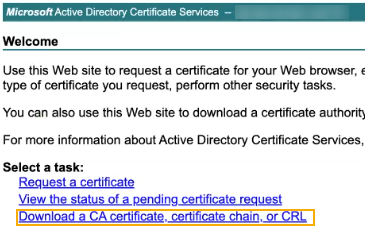
-
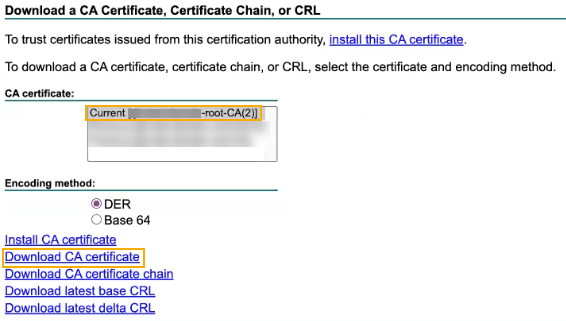
Select the root CA that's used to sign the subordinate CA.
-
Click Download CA certificate.
Here's an example:
-
Click Save.
-
Import the subordinate CA to Sophos Firewall
For CAs generated based on a CSR you created on Sophos Firewall, you must import the CA as follows:
- Go to Certificates > Certificates and click Add.
- Click the import button
 for the CSR you generated.
for the CSR you generated. - Click Choose file and select the subordinate CA you downloaded from AD CS.
-
Click Certificate authority only.
The firewall recognizes that it's a CA and makes the CA options available.
-
Change the certificate authority name if you want.
-
Click Import certificate.
Here's an example:
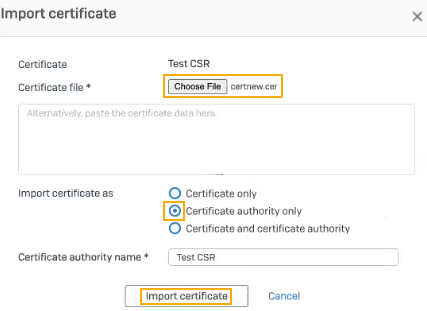
-
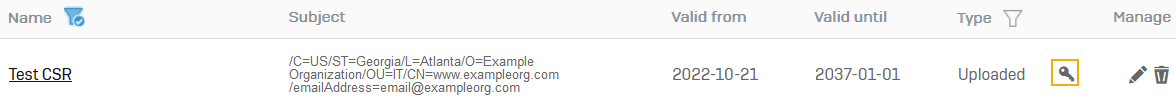
To see the subordinate CA on the list, go to Certificates > Certificate authorities.
-
Use the filter next to Name, enter the search term for the CA's name, and click Apply.
Here's an example:
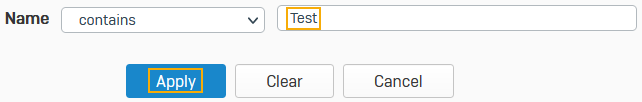
You can see the subordinate CA you imported. The firewall automatically associates the CSR's private key with the subordinate CA.
Upload the root CA to Sophos Firewall
To trust the subordinate signing CA, you must upload its root CA to Sophos Firewall.
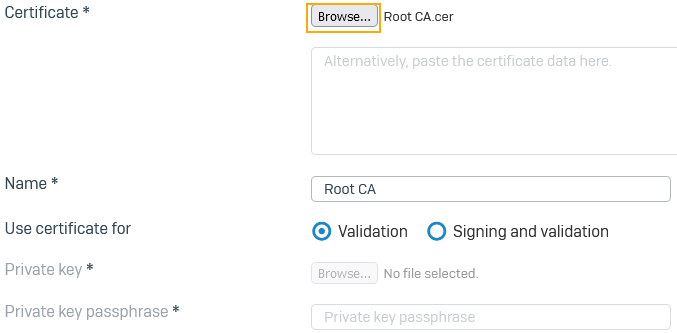
- Go to Certificates > Certificate authorities and click Add.
- For Certificate, click Browse and upload the root CA you downloaded from AD CS.
- Change the name if you want.
-
Under Use certificate for, retain the following default selection: Validation.
The root CA only validates the subordinate CA you imported.
Here's an example:
-
Click Save.
Apply the CA
You can select the subordinate CA to re-sign SSL/TLS traffic.
-
See Configure SSL/TLS inspection and decryption.
To make sure the subordinate and root CAs are in use for web traffic, open an HTTPS website, click the padlock icon, and check the secure connection details.
- See Email general settings.