Invalid traffic events
Invalid traffic logging is on by default for Sophos Firewall.
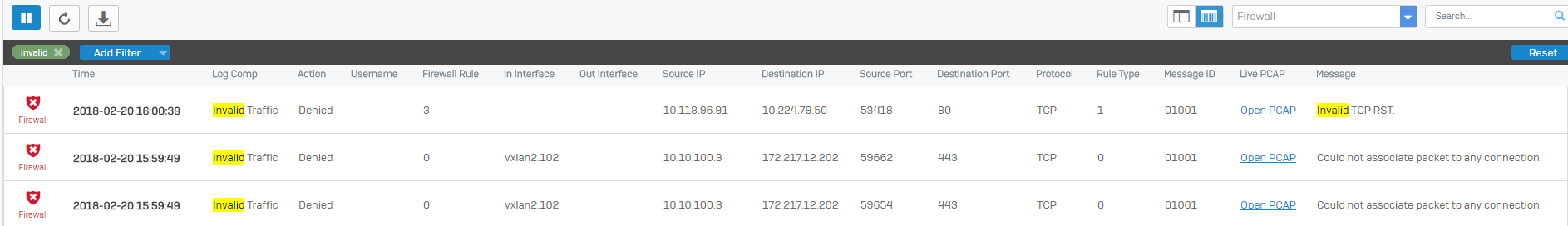
Invalid traffic events are shown in the log viewer. The following screenshot shows some examples:
Sophos Firewall uses a connection tracking system (conntrack). This system follows all TCP sessions through Sophos Firewall (as well as some UDP and ICMP sessions).
TCP uses flags to control the state of an open connection. It commonly uses the following flags:
SYN(Synchronization): A request for synchronization.SYN-ACK(Synchronization-Acknowledgment): Acknowledges the request and establishes connection parameters between devices.ACK(Acknowledgment): Confirms the connection agreement has been accepted and that the connection is now established. At this point data transfer can begin.PSH(Push): Sends data immediately.FIN(Finish): Request to end the session. The connection is closed when both devices accept this.RST(Reset): Closes the session without waiting for a response. This may be because an unexpected packet was received.
Sophos Firewall checks the data packets for conntrack entries. Conntrack entries are generated when connection initializing packets are sent, for example, TCP, SYN, or ICMP echo requests.
If a user sends a packet that doesn't match a current connection, Sophos Firewall logs this as an invalid traffic event.
All firewalls drop multiple TCP RST and TCP FIN packets to prevent attacks. Sophos Firewall drops these packets and records them as invalid traffic events.
Managing invalid traffic events
You should check your invalid traffic events if you have accessibility or connection problems.
You can reduce the number of invalid traffic events that you get. To do this change the Tcp Connection Establishment Idle Timeout value.
Note
This does not resolve issues. This will only decrease the number of invalid traffic events logged by Sophos Firewall.
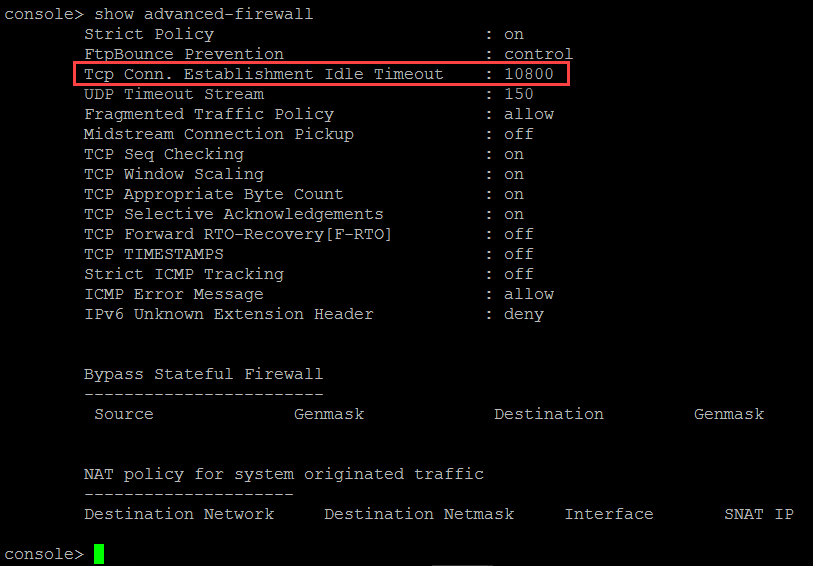
Tcp Connection Establishment Idle Timeout defaults to 10800 seconds (3 hours). After 3 hours of idle time, the conntrack entries expire. If a user then sends a packet, it doesn't match any connection in the conntrack table. Sophos Firewall drops the packet and logs it as an invalid traffic event.
To check the Tcp Connection Establishment Idle Timeout value, do as follows:
- Sign in to the command-line interface (CLI) and choose option 4. Device Console.
- Run the following command: show advanced-firewall.
This screenshot shows the Tcp Connection Establishment Idle Timeout value.
You can reduce the number of invalid traffic events logged by increasing the Tcp Connection Establishment Idle Timeout value. For example, you can increase the timeout to 6 hours (21600 seconds):
set advanced-firewall tcp-est-idle-timeout 21600