Add a Microsoft Entra ID (Azure AD) server
Add a Microsoft Entra ID (Azure AD) server to authenticate administrators signing in to the web admin console of the firewall and users signing in to the captive portal.
Before you add a Microsoft Entra ID server in the firewall, you must configure the authentication infrastructure on Azure Portal. See Configure Microsoft Entra ID (Azure AD) on Azure Portal.
To add a Microsoft Entra ID server in the firewall, do as follows:
- Go to Authentication > Servers and click Add.
- From the Server type list, select Azure AD SSO.
- In Server name, enter a name for the server.
-
For the IDs, do as follows:
- On Azure, go to Azure Active Directory > App registrations and click the application you created for the firewall.
- Copy Application (client) ID and paste it in Application (client) ID on the firewall.
- Copy Directory (tenant) ID and paste it in Directory (tenant) ID on the firewall.
-
On Azure, create a client secret and paste it in Client secret.
-
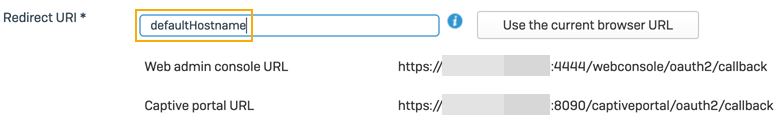
In Redirect URI, enter the FQDN or IP address from where the firewall is accessible. You can also click Use the current browser URL to fill it automatically. The redirect URI is unique for each firewall.
If you're configuring Microsoft Entra ID from Sophos Central firewall management, don't use the Sophos Central reverse SSO URL.
If you're configuring Microsoft Entra ID through Sophos Central group firewall management, you won't see the Redirect URI setting. It's configured as follows:
- In 20.0 MR1 and later, the Redirect URI is automatically set to the firewall's hostname if it's configured.
-
In 20.0 GA and earlier, or if no hostname is configured, the Redirect URI automatically uses the text
defaultHostname. After the initial configuration, you must manually update each firewall's Redirect URI with the IP address or hostname from where the firewall is accessible.
-
Copy the Web admin console URL or the Captive portal URL.
- Paste the URL in the application you created for the firewall on Azure. See Paste the redirect URI on Azure.
- User attributes under User attribute mapping are fetched from the Azure token to create users in the firewall.
-
From the Fallback user group list, select a user group.
If a user's Microsoft Entra ID group exists in the firewall, it assigns the user to that group. If it doesn't exist, the firewall assigns the user to the group you select here.
Note
If you use the Microsoft Entra ID server in Authentication > Services under Firewall authentication methods, the Fallback user group still applies instead of the Default group.
-
Select the role mapping criteria as follows:
Currently, you can only authenticate administrators signing in to the web admin console and users signing in to the captive portal.
-
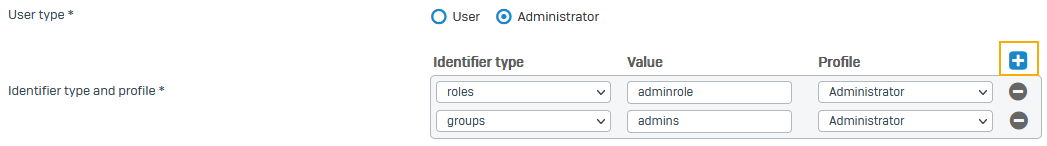
User type:
- User: Select this option if you only want to authenticate captive portal users.
- Administrator: Select this option if you want to authenticate both web admin console administrators and captive portal users.
-
Identifier type and profile:
-
Identifier type: Select the type you configured on Azure:
- roles
- groups
-
Value: Enter the value you configured on Azure for the identifier type.
-
Profile: Select an administrator profile.
You can see these on Profiles > Device access on the firewall.
To add multiple identifier types, click Expand
 .
. -
-
-
Click Test connection to validate the user credentials and check the connection to the server.
- Click Save.
-
Go to Authentication > Services and select the Microsoft Entra ID server under the following authentication methods:
- Firewall authentication methods: For the captive portal.
- Administrator authentication methods: For the web admin console.
Note
The firewall only allows one Microsoft Entra ID server for each authentication method.
-
Go to Authentication > Web authentication.
-
Select In new browser window.
Users must explicitly sign out to end their sessions or wait for the Microsoft Entra ID (Azure AD) token expiration time. We recommend keeping the captive portal window open for users to sign out.
-
Clear Use insecure HTTP instead of HTTPS.
Microsoft Entra ID SSO isn't supported if you select this option.
-
Click Apply.
Note
You must select Match known users and Use web authentication for unknown users in the corresponding firewall rules to use Microsoft Entra ID for authentication.
Note
Microsoft Entra ID (formerly Azure AD) uses token-based authentication through OAuth 2.0 and OpenID Connect (OIDC). So, local and remote users can't use Credential login and sign in with username and password.
To implement Credential login, you can use directory services, such as Active Directory (AD) or LDAP.