Forward the branch office internet traffic through the head office
You can configure a policy-based IPsec VPN connection to forward all internet traffic from the branch office to the head office's WAN port through an IPsec tunnel.
If you want the branch office's system-generated traffic to go to the internet directly from the branch office, you can turn off policy-based IPsec VPN routes for system-generated traffic.
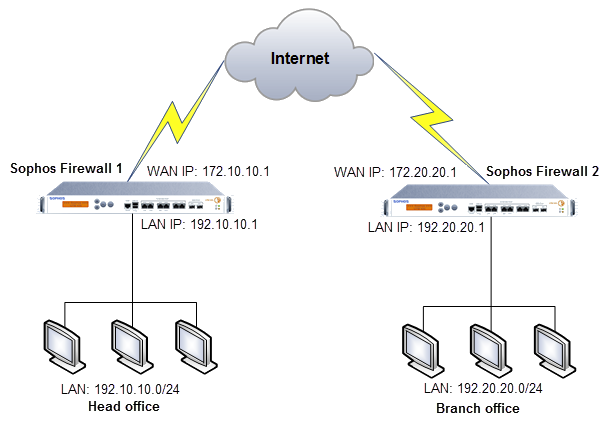
Network diagram
To forward all internet traffic from the branch office to the head office, do as follows:
- Configure a policy-based IPsec VPN connection between the branch office (Sophos Firewall 2) and the head office (Sophos Firewall 1).
- Configure firewall rules to allow traffic.
- (Optional) Turn off policy-based IPsec VPN routes for system-generated traffic if required.
Requirements
For this scenario, the route precedence must be VPN, static, and then SD-WAN routes. See Route precedence.
Configure a policy-based IPsec VPN
Create a policy-based IPsec VPN connection between the branch office and the head office. See Create a policy-based IPsec VPN using preshared key.
Configure the subnets as follows:
| Subnet | Head office firewall | Branch office firewall |
|---|---|---|
| Local | Any | Branch office LAN |
| Remote | Branch office LAN | Any |
Configure firewall rules
Configure firewall rules in the head and branch offices to allow traffic.
For all the rules, use the default values for the settings not mentioned in the tables.
Add a VPN-to-WAN firewall rule in the head office firewall
Add a VPN-to-WAN firewall rule in the head office firewall to allow all traffic from the VPN tunnel to route through the WAN port of the head office firewall.
In the head office firewall, do as follows:
- Go to Rules and policies > Firewall rules.
-
Select IPv4 or IPv6 protocol, select Add firewall rule, then click New firewall rule.
-
Specify the settings as follows:
Setting Value Rule name VPN to WAN Action Accept Log firewall traffic Select Rule position Top Rule group None Source zones VPN Destination zones WAN Create linked NAT rule > Translated source (SNAT) MASQ -
Click Save.
Add a LAN-to-VPN firewall rule in the branch office firewall
Add a LAN-to-VPN firewall rule in the branch office firewall to forward all LAN traffic to the VPN tunnel.
In the branch office firewall, do as follows:
- Go to Rules and policies > Firewall rules.
-
Select IPv4 or IPv6 protocol, select Add firewall rule, then click New firewall rule.
-
Specify the settings as follows:
Setting Value Rule name LAN to VPN Action Accept Log firewall traffic Select Rule position Top Rule group None Source zones LAN Source networks and devices Related IP address subnet Destination zones VPN -
Click Save.
Add a firewall rule in the branch office firewall to drop traffic
Add a firewall rule in the branch office firewall to drop LAN traffic going to the branch office firewall's WAN port.
In the branch office firewall, do as follows:
- Go to Rules and policies > Firewall rules.
-
Select IPv4 or IPv6 protocol, select Add firewall rule, then click New firewall rule.
-
Specify the settings as follows:
Setting Value Rule name LAN to WAN drop Action Drop Rule position Top Rule group None Source zones LAN Destination zones WAN -
Click Save.
Turn off policy-based IPsec VPN routes for system-generated traffic
If you want to allow the branch office's system-generated traffic to go to the internet directly from the branch office firewall's WAN port, you can turn off policy-based IPsec VPN routes for system-generated traffic.
To turn off policy-based IPsec VPN routes for system-generated traffic, do as follows:
- Sign in to the command-line console of the branch office firewall.
- For Device Console, type
4. -
Enter the following command:
set routing policy-based-ipsec-vpn system-generate-traffic disable