Active threat response
Active threat response provides instant and automated response to active adversaries equipped with sophisticated software and networking skills. These adversaries try to gain entry into your network and systems and continuously adapt their techniques using hands-on keyboard and AI-assisted methods.
Active threat response offers multiple modules of threat intelligence feeds, enabling the firewall to coordinate defenses immediately without manual intervention.
The modules are as follows:
- MDR threat feeds
- Sophos X-Ops threat feeds
You can choose to configure some or all of them. Configuration is simple because the threat feeds are integrated with the firewall.
The integration also enables the firewall to take immediate action without remediation delays, offering effective protection from threats.
What are threat feeds?
Threat feeds are a list of IP addresses, domains, and URLs involved in threat activity, such as phishing and malware. These objects are called Indicators of Compromise (IoCs) or indicators of attack.
Depending on the threat feed module, the firewall remains up-to-date with the threat feeds' latest indicators at frequent intervals or based on threat information.
When you configure a threat feed's settings, you allow the firewall to block or monitor traffic related to the IoCs in the feed.
Note
We recommend that you configure the firewall to block traffic related to IoCs instead of only logging the events.
Summary of threat feed modules
See what each threat feed module offers and its licensing requirements:
| Threat feed module | Description |
|---|---|
| MDR threat feeds | Sophos MDR analysts share intelligence about active threats in your network with the firewall. |
| Sophos X-Ops threat feeds | Threat database from SophosLabs. |
For licenses and the additional firewall configurations, see Requirements for threat feeds.
For threat feed configurations, see Configure threat feeds.
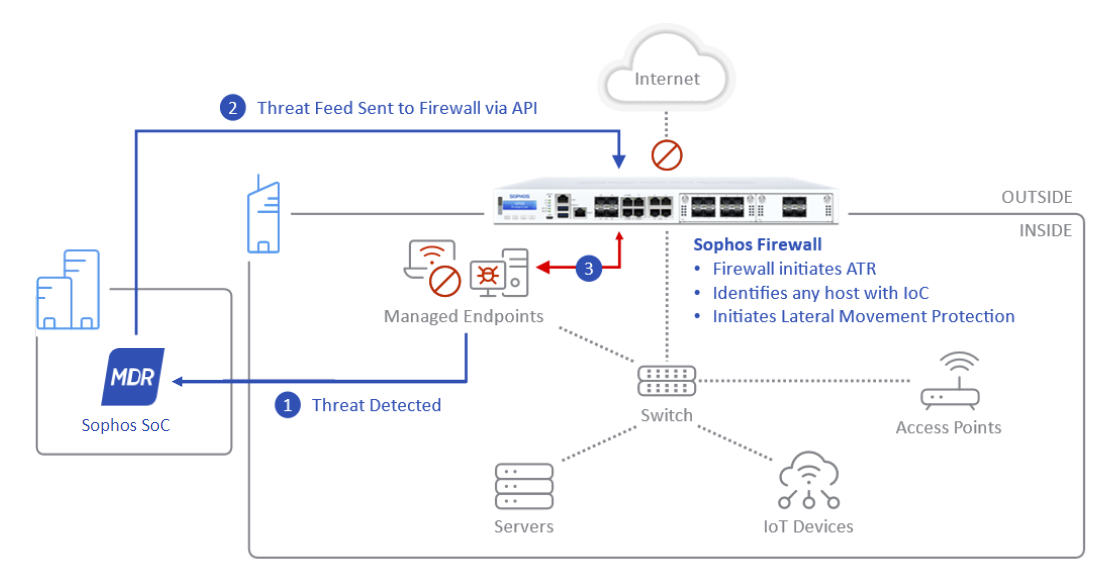
The following diagram shows how the different threat feed modules work with the firewall.
How the firewall implements threat feeds
The firewall first implements MDR threat feeds followed by Sophos X-Ops threat feeds.
If an IoC exists in both the threat feeds, the firewall takes action based on the following options you select:
- Log and drop: Drops the traffic, logs the event under MDR, and doesn't check the other threat feed.
- Log only or Monitor: Logs individual events for MDR and Sophos X-Ops threat feeds.
Note
Go to System services > Log settings and make sure logs for Active threat response are turned on.
Threat protection by traffic type
The following table shows the details of the traffic types that the Active threat response modules protect:
Forwarded traffic
Forwarded traffic is routed through the firewall to a destination within or outside the network.
| Traffic type | MDR | Sophos X-Ops |
|---|---|---|
| Source IP address match for outgoing traffic | ||
| Destination IP address, domain, and URL match for outgoing traffic |
Note
Active threat response doesn't match the source IP address for some types of traffic entering the network, such as DNAT and WAF traffic.
System-destined traffic
System-destined traffic is destined to the firewall, for example, traffic to the web admin console and traffic for which the firewall acts as the server.
| Traffic type | MDR | Sophos X-Ops |
|---|---|---|
| Source IP address match for traffic flowing to services listed in Administration > Device access, such as the web admin console, VPN portal, and VPN |
More resources