SD-WAN routing behavior
You can configure SD-WAN routes with SD-WAN profiles to reroute connections dynamically when a gateway becomes unavailable or doesn't meet the SLAs any longer.
You can use SD-WAN routes to route system-generated traffic and reply packets.
Reroute connections
To implement zero-impact failover, rerouting traffic (reroute-connection) is turned on by default.
You can turn it on or off from the command-line console as follows:
| Options | CLI commands |
|---|---|
| Show rerouting status | show routing reroute-connection |
| Turn on rerouting | set routing reroute-connection enable |
| Turn off rerouting | set routing reroute-connection disable |
See Routing commands.
Reroute SNAT connections
By default, Sophos Firewall reroutes all connections that don't match a source NAT (SNAT) rule. You can turn on rerouting for SNAT connections using the reroute-snat-connection CLI command. Additionally, you can turn off rerouting for non-NATed connections using the reroute-connection CLI command.
However, rerouting SNAT connections only works if you apply the same source IP address to gateways or links used for rerouting connections. For example, if you use Port-A with source NAT IP address 192.0.2.1 to route the initial connection, the rerouted connection via Port-B must also use the same source NAT IP address 192.0.2.1.
Using configurations such as masqueraded (MASQ) connections or Override source translation in an SNAT rule changes the Translated Source. An SNAT rule with different translated IP addresses or IP ranges leads to communication failures between endpoint computers and servers. So, the firewall doesn't reroute SNAT connections for these configurations.
You can turn SNAT rerouting on or off from the command-line console as follows:
| Options | CLI commands |
|---|---|
| Show the rerouting status for SNAT connections | show routing reroute-snat-connection |
| Turn on rerouting for SNAT connections | set routing reroute-snat-connection enable |
| Turn off rerouting for SNAT connections | set routing reroute-snat-connection disable |
See Routing commands.
System-generated traffic and reply packets
You can create SD-WAN routes and specify the gateways for system-generated traffic and reply packets. On the CLI, make sure you turn on routing for both.
Reply packets
Sophos Firewall enforces symmetric routing on WAN interfaces for reply packets. These packets use the same WAN interface as the original packets.
You can configure asymmetric routing for reply packets on non-WAN interfaces. For example, you can specify an interface other than the original traffic's interface for LAN to DMZ traffic.
Restriction
SD-WAN routes don't apply to reply packets if the original traffic uses the default route (WAN link load balance). The default route applies, and reply packets exit on the same interface they enter.
You can change the setting on the CLI. To turn on SD-WAN routing for reply packets, run the following command:
set routing sd-wan-policy-route reply-packet enable
See Routing commands.
System-generated traffic
Select only the destination networks and services because the incoming interface and source networks remain unknown. For example, traffic related to services used by Sophos Firewall flows through different interfaces, depending on the type of service.
You can change the setting on the CLI. To turn on SD-WAN routing for system-generated traffic, run the following command:
set routing sd-wan-policy-route system-generate-traffic enable
See Routing commands.
Note
- The firewall doesn't forward system-generated traffic if you select all the configured gateways as Backup on Network > WAN link manager. You must select at least one of them as Active.
- System-generated RED traffic on UDP port 3410 is layer 2 traffic. So, SD-WAN routes don't apply to this traffic.
Check the status
You can check whether SD-WAN routing for system-generated traffic and reply packets is turned on in the web admin console.
The tooltip under Routing > SD-WAN routes shows this status.
Route-based VPNs with SD-WAN routes
You can use SD-WAN routes with route-based IPsec VPN connections. You can select the XFRM interface's gateway in SD-WAN profiles or SD-WAN routes. See Create a route-based VPN (any to any subnets).
To compress the IPsec tunnel's traffic to increase the throughput, go to Profiles > IPsec profiles and select Pass data in compressed format for the profile you've selected in the route-based VPN configuration.
Request and reply traffic
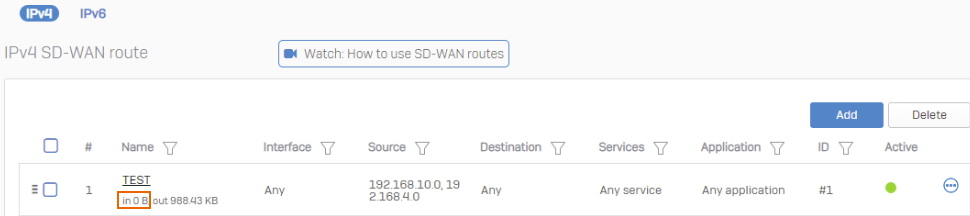
SD-WAN routes only show a route's traffic count for traffic that matches the source and destination settings in the route.
The following example only shows the request traffic count based on the route's source and destination settings. Although reply traffic follows a symmetric path, that is, uses the same route, the route configuration doesn't show the reply traffic count. The OUT count stands for the request traffic count. The IN count stands for the reply traffic count.
To see the request and reply traffic count, make sure the route's source and destination settings match request and reply traffic.