Logs and alerts for Active threat response
You can configure log settings, alerts, and notifications for threat feeds to save logs locally in the firewall and to send logs to syslog servers and Sophos Central.
Configure Log settings
To configure log settings, do as follows:
- Go to System services > Log settings.
-
Under Log settings, select Active threat response for the following options:
- Local reporting.
- Syslog servers that you configure.
-
Central reporting.
The column appears after you select Send reports and logs to Sophos Central on the Sophos Central page in the firewall.
-
Click Apply.
Note
To generate alerts and notifications, go to System services > Notification list.
See the logs
The firewall first implements MDR threat feeds if it's configured. To know how it logs events related to IoCs that exist in all threat feeds, see How the firewall implements active threat response.
Summary
- Go to Log viewer, and select Active threat response to see the blocked Indicators of Compromise (IoCs).
- If you have Synchronized Security, see the additional information, such as user, host, and process, to take action.
- To ask MDR analysts about an IoC identified by MDR, find their audit ID in the logs. They need the ID to identify the feed.
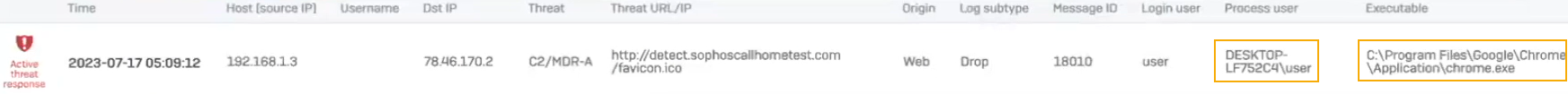
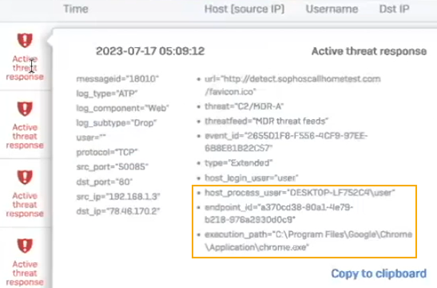
Endpoint threat details
When a threat is detected, the firewall queries endpoints managed by Sophos Central for information, such as the host, user, and process.
How to see the details
Use the following options:
-
Log viewer:
- Select Active threat response from the drop-down list.
- Check the Process user and Executable columns.
- Additionally, check the logs in the detailed format.
-
Reports:
- Click Network & threats.
- Select Active threat response from the drop-down list.
- Check the Synchronized IoC list.
Threat details
The endpoint threat details are as follows:
host_process_userendpoint_idexecution_path
Note
You can see the host, user, and process details in endpoints that use Windows 7 and later versions.
You don't see these details on macOS endpoints. Instead, a generic alert appears, for example, "Active threat C2/Generic-C deleted". To identify the endpoint, look for the source IP address in Log viewer in the firewall.
MDR security analyst audit ID
When an MDR security analyst adds or removes an IoC, such as an IP address, domain, or URL, the event is logged, showing the action and the security analyst's identity (audit_ID).
To ask MDR analysts about a threat feed, find their audit ID in the logs. They need the ID to identify the feed.
You can see the action and audit_ID using one of the following options:
- In Log viewer, select the detailed view button, then select Admin from the drop-down list.
- In Sophos Central, go to My Products > Firewall management > Tasks Queue.