Firewall configurations for threat feeds
In addition to the threat feed configurations, you must configure firewall settings and rules based on the type of Indicators of Compromise (IoCs) and the type of traffic.
For more information about the modules that enable the firewall to identify IoCs, see How other modules implement threat feeds.
Configuration requirements
For Active threat response to identify and take action on all the IoCs, make sure the following configurations are in place:
- Firewall rule: Configure a rule allowing internal to WAN traffic.
-
Intrusion prevention: Specify at least one of the following settings.
- Application classification must be turned on. It's turned on by default. See application_classification.
- Select an intrusion prevention policy in the firewall rule.
Note
The firewall needs IPS-related settings for the following traffic:
- HTTPS traffic
- DNS requests to servers other than the firewall over HTTP and HTTPS
-
Decryption: Specify the decryption settings and rules for URLs over HTTPS to get the full URL path.
Note
To read the full URL, the firewall must decrypt traffic. The Server Name Indication (SNI) header only contains the domain name.
-
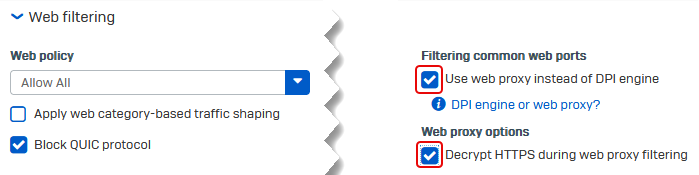
If you use Web proxy, do as follows:
-
If you use DPI mode, do as follows:
- Go to Web filtering in the firewall rule and clear Use web proxy instead of DPI engine.
- Go to Rules and policies > SSL/TLS inspection rules, click Add, and create a rule with Action set to Decrypt for internal to WAN traffic. See Add an SSL/TLS inspection rule.
-
Summary of requirements
To take action on IoCs, the firewall needs some basic configurations. If an IoC isn't blocked, see Troubleshoot Active threat response.
flowchart TD;
A(IoC types)
B(IP addresses)
C(Domains)
D(URLs)
E(Firewall rule)
F(1. Firewall rule</br>2. Application classification: On</br> or IPS policy in firewall rule)
G(1. Firewall rule</br>2. Application classification: On</br> or IPS policy in firewall rule</br>3. Web proxy, decryption settings in firewall rule</br> or DPI setting in firewall rule and</br> SSL/TLS inspection rule)
H(Check threat exclusions)
I(1. Check threat exclusions</br>2. Check web exclusions</br> or SSL/TLS exclusion lists)
A==>B;
A==>C;
A==>D;
B == Configuration ==> E == Troubleshooting ==> H
style E text-align:left
style H text-align:left
C == Configuration ==> F == Troubleshooting ==> I
style F text-align:left
D == Configuration ==> G == Troubleshooting ==> I
style G text-align:left
style I text-align:left
style A color:#000000, fill:white, stroke:#2962FF
style E color:#000000, fill:white, stroke:#2962FF
style F color:#000000, stroke:#2962FF, fill:white
style G color:#000000, stroke:#2962FF, fill:white
linkStyle default stroke:red
linkStyle 0 stroke-width:2px,stroke:#708090
linkStyle 1 stroke-width:2px,stroke:#708090
linkStyle 2 stroke-width:2px,stroke:#708090
linkStyle 3 stroke-width:2px,stroke:#4169E1
linkStyle 4 stroke-width:2px,stroke:#FFA500
linkStyle 5 stroke-width:2px,stroke:#4169E1
linkStyle 6 stroke-width:2px,stroke:#FFA500
linkStyle 7 stroke-width:2px,stroke:#4169E1
linkStyle 8 stroke-width:2px,stroke:#FFA500