Configure per-connection AD SSO authentication for multi-user hosts
You can use per-connection AD SSO authentication for multi-user hosts configured to use the Firewall as a direct proxy.
Overview
This overview explains how to configure per-connection authentication for multi-user hosts. A multi-user host is an endpoint or server on which multiple users can sign in at the same time, for example, a multi-user Linux server or a Windows server running Remote Desktop services or Direct Access.
When you turn on per-connection authentication, the web proxy authenticates each HTTP or HTTPS connection from the multi-user host using an NTLM or Kerberos authentication challenge. The firewall treats all other network traffic from a multi-user host as unauthenticated – with no known user ID.
Restrictions
-
Per-connection authentication only applies for connections using direct proxy mode. You must configure browsers and other clients on the multi-user host to connect using the firewall's web proxy listening port. The default port is 3128.
-
A multi-user host with per-connection authentication configured can only use per-connection authentication. Sophos Firewall disables all other authentication methods for any traffic coming from the IP address of that host.
-
For Kerberos SSO to work, the endpoint computers must use the FQDN of Sophos Firewall in their proxy settings. You can't use an IP address. NTLMv2 mode isn't affected by this restriction and is automatically used if the endpoint computers aren't configured correctly, or if the browser doesn't support Kerberos authentication.
Note
Sophos Authentication for Thin Client (SATC) also enables Sophos Firewall to authenticate users accessing a server or remote desktop. SATC is included with Sophos Server Protection in Sophos Central and can authenticate all types of connections from end-users’ desktop sessions without requiring direct proxy configuration. See Sophos Authentication for Thin Client.
Introduction
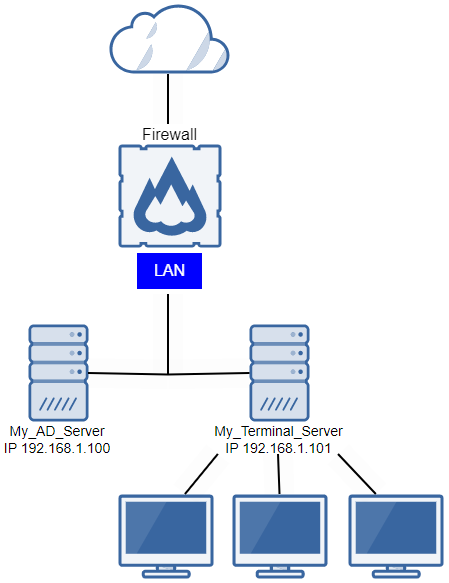
In this example, you want to turn on per-connection AD SSO authentication for users signed in to My_Terminal_Server in the sophos.com domain. Here's the network schema.
Configuration
To use per-connection authentication for multi-user hosts, do as follows:
- Add an Active Directory (AD) server for authentication.
- Import AD groups.
- Set the firewall authentication method.
- Create an IP host for your multi-user host.
- Create firewall rules for inbound and outbound multi-user host traffic.
Add an AD server for authentication
When a user signs in to Sophos Firewall, it authenticates the user by verifying them against the list of users created during the integration with AD. After authenticating the user, Sophos Firewall communicates with AD to get additional authorization data for access control.
To add an AD server, do as follows:
- Go to Authentication > Servers and click Add.
- Select Active Directory as the server type.
-
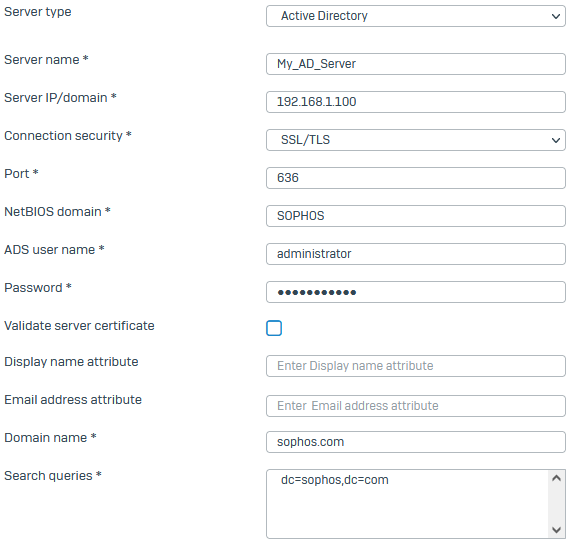
Specify the server settings.
Note
For settings not listed in this example, use the default settings.
Setting Value Name My_AD_Server Server IP/domain 192.168.1.100 Connection security SSL/TLS
Uses the default port.NetBIOS domain SOPHOS ADS username administrator Password Password for the admin user of the server. Domain name sophos.com Search queries Click Add and enter dc=sophos,dc=com.Here's an example:
Tip
Search queries are based on the domain name (DN). In this example, the domain name is
sophos.com, so the search query is:dc=sophos,dc=com.See Searching AD
-
Click Test connection to validate the user credentials and check the connection to the server.
- Click Save.
Import AD groups
When a user signs in for the first time, the firewall automatically adds them as members of the default group specified. If the user's group exists in Sophos firewall, the firewall adds the user to that group.
To import AD groups into the firewall and specify policies for them, do as follows:
-
Go to Authentication > Servers > Manage and click Import
 for
for My_AD_Server. -
In the Import group wizard, click Start.
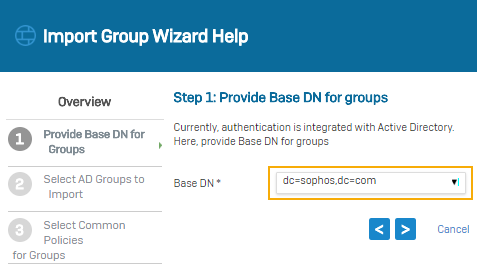
-
For Base DN, select
dc=sophos,dc=com. -
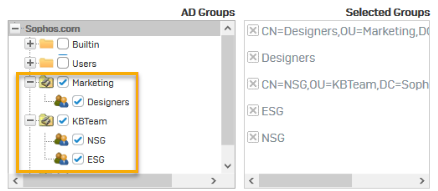
Choose the AD groups you want to import. In this example, select the Marketing and KBTeam OUs.
Tip
Selecting an OU will select all groups within that OU.
-
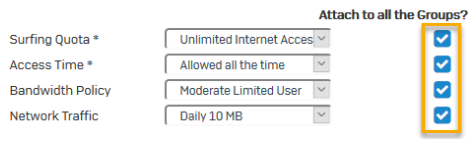
Select common policies for groups. Select Attach to all the Groups to assign the policies to all groups that the wizard imports.
-
Review the selection.
- View the results and click Close.
- Go to Authentication > Groups and verify the recently imported groups.
Set the primary authentication method
If you've configured multiple AD servers, Sophos Firewall performs validation against your AD servers in the order configured in the web admin console.
To set the AD server as the primary authentication method, do as follows:
- Go to Authentication > Services.
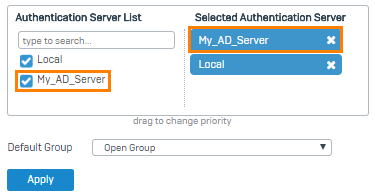
- In the authentication server list under Firewall authentication methods, select
My_AD_Server. -
Move the server to the first position in the list of selected servers.
Here's an example:
-
Choose the default group. Sophos Firewall adds users to the default group if they don't belong to a local group.
-
Click Apply.
Create an IP host
You must create an IP host for your multi-user host so that you can select it for per-connection authentication.
To create an IP host for your multi-user host, do as follows:
- Go to Hosts and services > IP host and click Add.
-
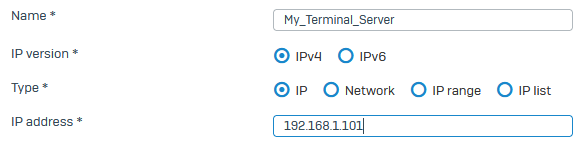
Specify the settings.
Setting Value Name My_Terminal_Server IP version IPv4 Type IP IP Address 192.168.1.101 Here's an example:
-
Click Save.
Tip
If you have more than one multi-user host, you can create an IP host group. See Add an IP host group.
Turn on per-connection AD SSO authentication for multi-user hosts
To authenticate multiple users from a single IP address using AD SSO, you must turn on per-connection authentication for multi-user hosts. The firewall continues to use per-IP authentication for all other hosts.
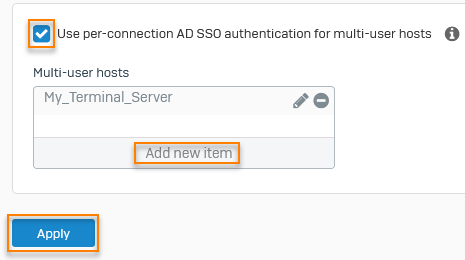
To turn on per-connection authentication for multi-user hosts, do as follows:
- Go to Authentication > Web authentication > Authentication settings for direct web proxy.
- Select Use per-connection AD SSO authentication for multi-user hosts.
- Click Add new item and select
My_Terminal_Server. -
Click Apply.
Here's an example:
Create firewall rules for multi-user host traffic
Multi-user hosts with per-connection authentication turned on must have a separate firewall rule that has Match known users turned off.
To create firewall rules for outbound multi-user host traffic, do as follows:
- Go to Rules and policies > Firewall rules.
- Select IPv4 or IPv6, select Add firewall rule, and select New firewall rule.
-
Enter the rule details:
Setting Value Rule name TS_Outbound Rule position Top Action Accept Log firewall traffic Select to log all traffic that matches this rule. Warning
Sophos Firewall evaluates rules in the order shown until it finds a match. Per-connection authentication rules must come before other rules that affect your multi-user hosts with Match known users turned on, for example, rules that affect any groups your multi-user hosts belong to. If Match known users is turned on for a multi-user host, then the firewall processes all traffic from that host based on the logged-in user (usually an admin) and won't process any more rules for that host.
-
Specify the settings.
Setting Value Source zones LAN Source networks and devices My_Terminal_Server Destination zones WAN Destination networks Any Services Select the services you want to allow. Match known users Turn this setting off. -
Enter any other settings needed for your environment. See Add a firewall rule.
- Click Save.
To create firewall rules for inbound multi-user host traffic, do as follows:
- Select IPv4 or IPv6, select Add firewall rule, and select New firewall rule.
-
Enter the rule details:
Setting Value Rule name TS_Inbound Rule position Top Action Accept Log firewall traffic Select to log all traffic that matches this rule. Warning
Sophos Firewall evaluates rules in the order shown until it finds a match. Per-connection authentication rules must come before other rules that affect your multi-user hosts with Match known users turned on, for example, rules that affect any groups your multi-user hosts belong to. If Match known users is turned on for a multi-user host, then the firewall processes all traffic from that host based on the logged-in user (usually an admin) and won't process any more rules for that host.
-
Specify the settings.
Setting Value Source zones WAN Source networks and devices Any Destination zones LAN Destination networks My_Terminal_Server Services Select the services you want to allow. Match known users Turn this setting off. -
Enter any other settings needed for your environment. See Add a firewall rule.
- Click Save.
More information