Allow clientless SSO (STAS) authentication over a VPN
With Sophos Transparent Authentication Suite (STAS) 2.1.2.8, Sophos Firewall can be configured to allow VPN users to automatically authenticate with a remote Active Directory server via single sign-on (SSO).
Introduction
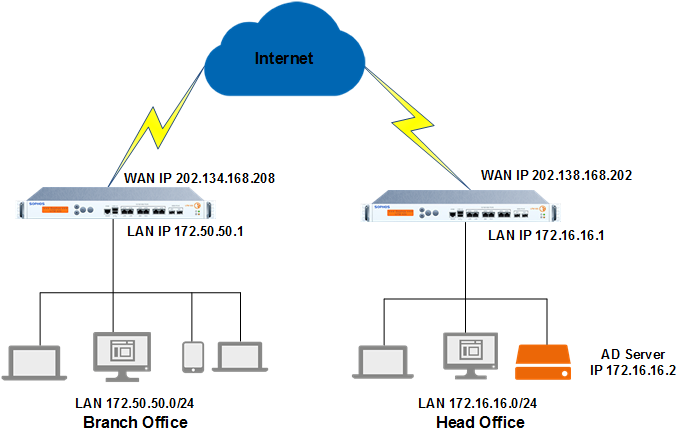
In this example, you want branch office users to automatically authenticate with the head office Active Directory server with clientless SSO. Here's the network schema.
Prerequisites
The following conditions must be met to use STAS over a VPN.
- IPsec connection must be active and connected.
- Traffic from the branch office must route through the IPsec tunnel. For more information, see Sophos XG Firewall: How to Route Initiated Traffic Through an IPsec VPN tunnel.
- Head office and branch office must have clientless SSO (STAS) implemented along with Active Directory. The domain controller is located in the head office only. For more information, see Configure transparent authentication using STAS.
Configuration
To allow branch office users to automatically authenticate with the head office Active Directory server with clientless SSO, you must do as follows:
- Add the branch office network as a monitored network in STAS.
- Add the branch office Sophos Firewall to STAS collector configuration.
- Configure the branch office Sophos Firewall to prompt VPN traffic for authentication.
Add the branch office network as a monitored network in STAS
To include the branch office network as a monitored network, do as follows:
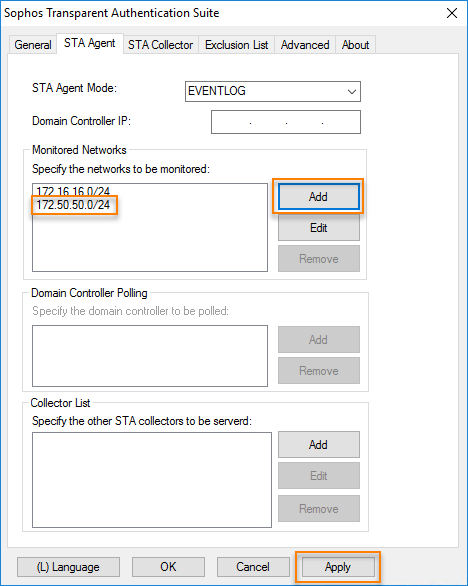
- Sign in to the server with the STAS application using the administrator credentials.
- Start STAS from the desktop or Start menu.
- Go to STA Agent.
- Under Monitored Networks, add the branch office network.
-
Click Apply.
Here's an example.
Add the branch office Sophos Firewall to STAS collector configuration
To include the branch office Sophos Firewall in STAS collector configuration, do as follows:
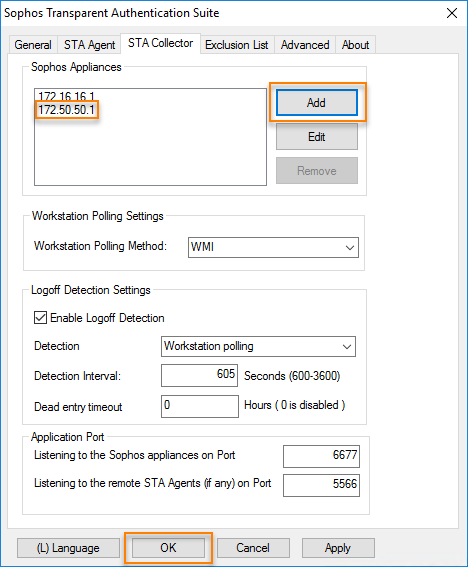
- Sign in to the server with the STAS application using the administrator credentials.
- Start STAS from the desktop or Start menu.
- Go to STA Collector.
- Under Sophos Appliances, add the IP address of the branch office Sophos Firewall.
-
Click OK.
Here's an example.
Configure the head office Sophos Firewall to prompt VPN traffic for authentication
By default, Sophos Firewall prompts unauthenticated traffic for clientless SSO from the LAN/DMZ zone. Since STAS at the head office serves login requests from the branch office over VPN, you must configure the head office Sophos Firewall to prompt the sign-in requests.
- Sign in to the command line using SSH. You can also access it from admin > Console in the upper-right corner of the web admin console.
- Choose option 4. Device Console.
-
Run the following command on the head office Sophos Firewall to add the branch office network to STAS.
system auth cta vpnzonenetwork add source-network 172.50.50.0 netmask 255.255.255.0
Note
Administration > Device Access > Local Service ACL > Clients must be turned on for the VPN zone.