Configure Active Directory authentication
You can add existing Active Directory (AD) users to Sophos Firewall. Add an Active Directory server, import groups, and set the primary authentication method.
Introduction
You need to do as follows:
- Add and configure an Active Directory server on the firewall.
- Import AD groups using the Import group wizard.
- (Optional) Configure a firewall rule to allow internet access.
- Set the primary authentication method so that the firewall queries the Active Directory server first.
Overview
This overview explains how Sophos Firewall uses Active Directory to authenticate users and manage access control.
When an Active Directory user signs in to Sophos Firewall for the first time, they are automatically added to the default group. If the user's Active Directory group exists in Sophos Firewall they are added to that group.
When a user signs in to Sophos Firewall, it authenticates the user by verifying them against the list of users created during the integration with Active Directory. When the user is authenticated, Sophos Firewall communicates with Active Directory to get additional authorization data for access control.
If your Active Directory server is down, the authentication request returns a Wrong username/password message.
When you've configured multiple Active Directory servers, Sophos Firewall performs validation against your Active Directory servers in the order configured in the web admin console.
Video: Active Directory integration
The following video shows how to integrate an AD server.
Add an Active Directory server
First, you add an Active Directory server that includes a search query.
You’ll need the following information to complete this task:
- Domain name
- NetBIOS domain
- Active Directory server password
Check the properties of the Active Directory server. For example, on Microsoft Windows, go to Windows Administrative Tools.
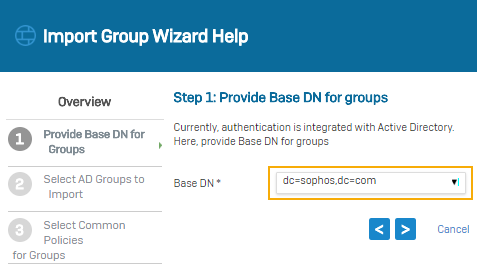
Search queries are based on the domain name (DN). In this example, the domain name is sophos.com, so the search query is: dc=sophos,dc=com.
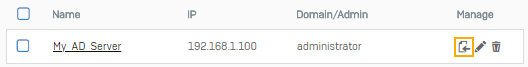
- Go to Authentication > Servers and click Add.
-
Specify the settings.
Note
For settings not listed here, use the default value.
Use the password configured on the Active Directory server.
Setting Value Server type Active directory Server name My_AD_Server Server IP/domain 192.168.1.100 NetBIOS domain sophos ADS username administrator Password <AD server password> Domain name sophos.com Search queries dc=sophos,dc=com Tip
Any domain-joined user account that can query, search, and read AD group membership is sufficient to import groups from the AD server.
-
Click Test connection to validate the user credentials and check the connection to the server.
Note
When both synchronized user ID and STAS are configured, the authentication server uses the mechanism from which it receives the sign-in request first.
-
Click Save.
Import Active Directory groups
Import Active Directory groups into the firewall and specify policies for them.
-
Go to Authentication > Servers and click Import
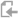 .
. -
In the Import group wizard, click Start.
-
Select the base DN for groups.
-
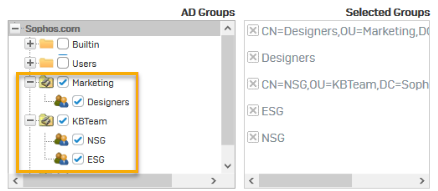
Select the AD groups to import.
-
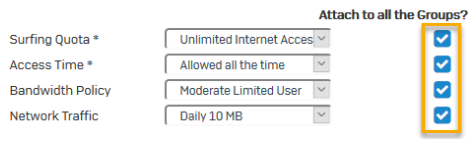
Select common policies for groups.
-
Review selection.
- View results.
- Go to Authentication > Groups and verify the recently imported groups.
Configure firewall rule to allow internet access
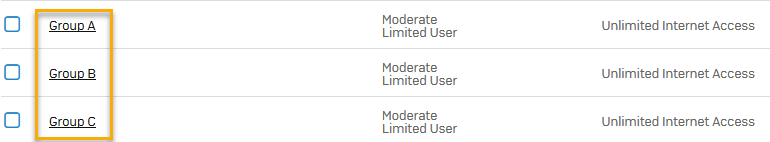
If you want to allow internet access for the groups that you created, you can configure a firewall rule. In this example, we imported three groups: Group A, Group B, and Group C.
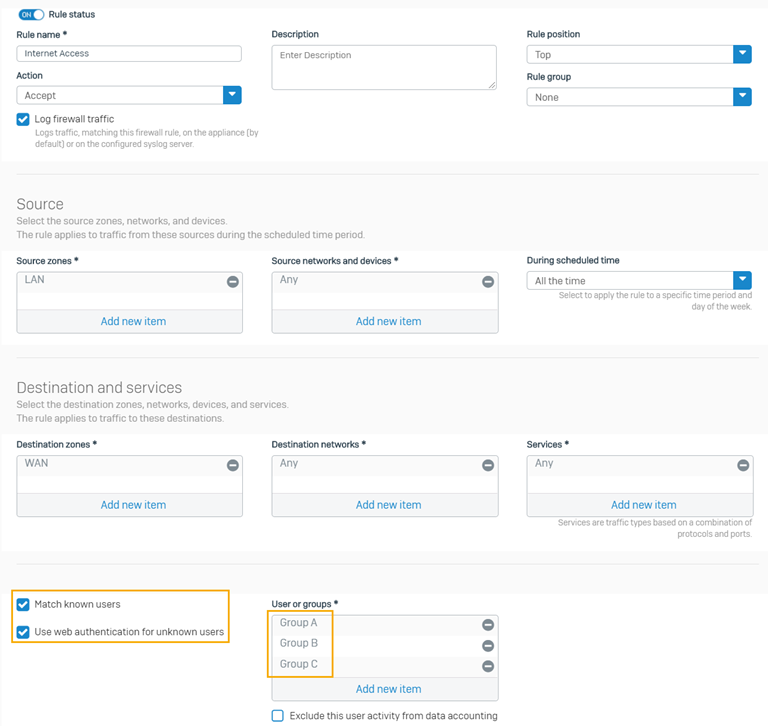
- Create a firewall rule to control internet access for your recently imported groups (Group A, Group B, and Group C). See Add a firewall rule.
- Select Match known users.
- Select Use web authentication for unknown users.
- Select the example groups (Group A, Group B, Group C) we imported.
-
Click Save.
See the example firewall rule below.
Set primary authentication method
To query the Active Directory server first, set it as the primary authentication method. When users sign in to the firewall for the first time, they're automatically added as a member of the default group specified.
Note
AD users must sign in to the firewall once to appear in groups.
- Go to Authentication > Services.
- In the authentication server list under Firewall authentication methods, select My_AD_Server.
-
Move the server to the first position in the list of selected servers.
-
Click Apply.
Go to Authentication > Groups and verify the imported groups.