Configure Microsoft Entra ID (Azure AD) on Azure Portal
To configure Microsoft Entra ID with the firewall, you must do as follows on Azure:
- Create an application for the firewall.
-
Create application roles, groups, or both.
Application roles are specific to an application, and you can control access by assigning users and permissions to the roles required for that application. If you want to use application roles, see Create an application role.
To use Microsoft Entra ID groups, create groups specifically for the firewall and add only the users to whom you want to provide access to the firewall. If you want to use Microsoft Entra ID groups, see Create a Microsoft Entra ID group.
-
Assign users to the application.
In the firewall, you must then add Microsoft Entra ID SSO as an authentication server. See Add a Microsoft Entra ID (Azure AD) server.
Best practices
Here are the best practices for configuring Microsoft Entra ID with the firewall:
- Create a separate Azure application for the firewall for granular control and isolation.
- Make sure you turn on Assignment required in Microsoft Entra ID to grant access to only the users assigned to the Azure application.
- Grant only the required API permissions, User.Read, User.ReadAll and Group.ReadAll.
- Use application roles instead of Microsoft Entra ID groups.
Create an application for the firewall
We recommend you create a separate Azure application for the firewall for granular control and isolation. To create an application for the firewall, do as follows:
- On Azure, search for
app registrationsand click App registrations. - Click New registration.
- Enter a name for the application.
- Under Supported account types, for Who can use this application or access this API?, select Accounts in this organizational directory only (Default Directory only - Single tenant).
-
Under Redirect URI (optional), in the Select a platform list, select Web.
You don't need to specify a URL in the next field.
-
Click Register.
Azure Portal shows the details of the application you created.
-
Note the following details:
- Application (client) ID
- Directory (tenant) ID
You must enter these details when adding a Microsoft Entra ID server to the firewall.
Create an application role
If you want to assign permissions to users and applications, you can create an application role.
To create an application role, do as follows:
- In the application you created for the firewall on Azure, go to App roles and click Create app role.
- Enter a name for the role.
- In Allowed member types, select Both (Users/Groups + Applications).
-
In Value, enter a value for the application role.
For example, adminrole.
When a user signs in to the firewall, Microsoft Entra ID sends a token containing information about that user. The token includes this value to identify the device access rights (or profile) associated with the user. You must enter this value for the corresponding Identifier type on the firewall.
-
Enter a description for the role.
-
Click Apply.
The application role you created is shown in the application roles list.
-
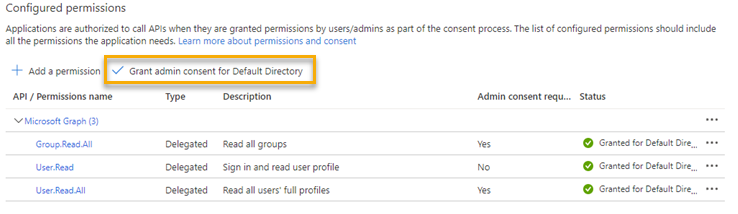
Go to API permissions and click Add a permission.
- In the Request API permissions pane, click Microsoft Graph.
- Select Delegated permissions.
- Under Select permissions, select the User.Read, User.ReadAll and Group.ReadAll permissions.
- Click Add permissions.
-
Grant admin consent for the selected permissions and click Yes when prompted.
Here's an example:
Note
The administrator consents on behalf of all users in the tenant's active directory. This allows the application to access the data of all users without prompting users for consent. See Permissions and consent in the Microsoft identity platform.
Require application assignment
You must require application assignment to only allow assigned users, groups, apps, or services to access your application.
To require application assignment, do as follows:
- On Azure, search for
enterprise applicationsand click Enterprise applications. - Click the application you created for the firewall on Azure.
- Go to Manage > Properties and turn on Assignment required.
- Click Save.
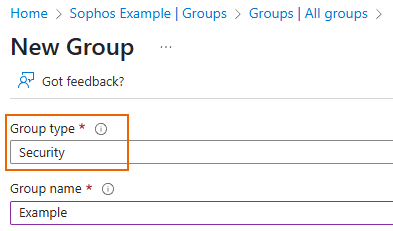
Create a Microsoft Entra ID group
If you want to create a Microsoft Entra ID group, do as follows on Azure:
- Create a Microsoft Entra ID group specifically for the firewall.
- To the Microsoft Entra ID group, add only the users to whom you want to provide access to the firewall.
- To import groups, add the required API permission. See Import groups.
For instructions about creating Microsoft Entra ID groups and assigning users, see Quickstart: Create a group with members and view all groups and members in Azure Active Directory.
Assign users or groups to the application
To assign users or groups to the application, do as follows:
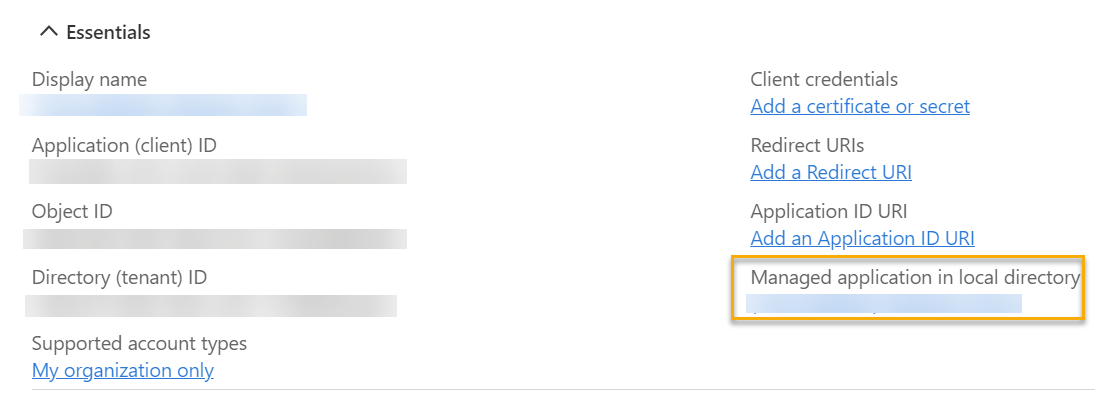
- Go to the application you created for the firewall on Azure.
-
Next to Manage application in local directory, click the application's name.
-
Go to Manage > Users and groups, then click Add user/group.
- Search for the users or groups you want to add and select them.
-
Select the application role you created.
If you've created more than one application role, select the application role you want to assign to the users or groups.
-
Click Assign.
Create a client secret
When you're adding Microsoft Entra ID server to the firewall, paste this secret in Client secret.
To create a client secret on Azure, do as follows:
- Go to App registrations and click the application you created for the firewall.
- In the application, go to Certificates & secrets > Client secrets and click New client secret.
- Enter a description, select the secret's expiry duration, and click Add.
-
Copy the secret from Value next to the name of the secret immediately.
Note
You must copy the secret immediately because Azure Portal hides the secret once the page reloads.
Paste the redirect URI on Azure
Do as follows: