Configure AD SSO web authentication
Sophos Firewall supports NTLM and Kerberos web authentication for Active Directory single sign-on (AD SSO). When one of these options is configured, the firewall can automatically authenticate users on the network as they access web resources. See Authentication methods. To authenticate SSL VPN users, see SSL VPN.
You must configure the following steps:
- Specify a hostname for Sophos Firewall.
- Configure an Active Directory (AD) server.
- Confirm that the AD server is the primary service for authentication.
- Turn on AD SSO for the zones requiring NTLM and Kerberos authentication.
- Turn on NTLM and Kerberos authentication for Web authentication.
Configure a hostname
For NTLM, you can configure a hostname or a fully qualified domain name (FQDN). To work correctly, Kerberos requires an FQDN.
- Go to Administration > Admin and user settings.
-
For Hostname, enter a hostname or an FQDN. Use lowercase characters because Kerberos is case-sensitive.
Maximum number of characters for the hostname: 15
If you configure an FQDN, take note of the following:
- Make sure the host part has a maximum of 15 characters. For example,
sophosfirewall.mycompany.comis valid because the host part has 14 characters, butheadofficesophosfirewall.mycompany.comis invalid because the host part has more than 15 characters. - The firewall uses the host part to join the AD domain and then appends the AD domain to it within AD. So, you can configure
sophosfirewall.mycompany.com, but it's stored in AD assophosfirewall.mycompany.local. This matters in DNS and Kerberos authentication.
Note
By default, the serial number is used as the hostname if you don't configure a specific FQDN hostname during the initial setup of the firewall.
- Make sure the host part has a maximum of 15 characters. For example,
-
Click Apply.
Configure redirection location
- Go to Administration > Admin and user settings.
-
Under Admin console and end-user interaction, select and configure the appropriate redirection setting:
If you use Kerberos in transparent mode, the hostname used in redirection must be the hostname AD knows. This can be different from the configured one.
On the client, you can run
setspn -Q HTTP/*to confirm the Service Principal Name (SPN) of the firewall. You must use the same value in redirection. Make sure that it can be resolved in DNS.If you use NTLM in transparent mode with a hostname for redirection, the client automatically trust the server to send credentials to it.
If you use an FQDN for redirection, the client needs to be configured to trust it.
-
Click Apply.
Add an AD server
Add an AD server that includes a search query. You’ll need the following information to complete this task:
- Domain name
- NetBIOS domain
-
Username and password of a domain-joined user
Tip
Any domain-joined user account can query, search, and read AD group membership and is sufficient if you don't use AD SSO. However, you must have an account with greater privileges to join a firewall to AD SSO. For HA deployments, or if the firewall encounters any issues, the firewall may need to automatically rejoin AD. You can use an account in the Domain Admins group, or create one with the specific additional permissions. To create an account with the specific permissions, see Sophos Firewall: Troubleshoot issues when joining Active Directory for AD SSO.
Check the properties of the AD server. For example, on Microsoft Windows, go to Windows Administrative Tools.
Search queries are based on the domain name (DN). In this example, the DN is contoso.com, so the search query is: dc=contoso,dc=com.
- Go to Authentication > Servers and click Add.
-
Configure the following:
Note
For settings not listed here, use the default value.
Setting Value Server type Active Directory Server name My_AD_ServerServer IP/domain 192.168.1.100NetBIOS domain contosoADS user name <username> Password <password> Domain name contoso.comSearch queries dc=contoso,dc=com -
Click Test connection to validate the user credentials and check the connection to the server.
Note
If you're having issues connecting the firewall to the AD server for AD SSO, try changing the Connection security to Plaintext. While Test connection may work, the AD SSO connection can sometimes have issues with increased connection security. Lowering security temporarily during debugging can determine if that's the issue, and needs further investigation.
-
Click Save.
Set primary authentication method
To query the AD server first, set it as the primary authentication method. When users sign in to the firewall for the first time, they're automatically added as a member of the default group specified.
- Go to Authentication > Services.
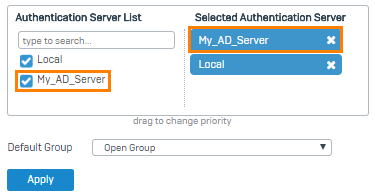
- In the Authentication server list under Firewall authentication methods, select
My_AD_Server. -
Move the server to the first position in the list of selected servers.
-
Click Apply.
- Go to Authentication > Groups and verify the imported groups.
Note
AD SSO connects to the servers in the order of their listing under Selected authentication server. It only connects to the other servers if it can't reach the preceding servers.
Turn on AD SSO for LAN zones
Turn on AD authentication for the required zones.
AD authentication is required for Kerberos and NTLM to work.
- Go to Administration > Device access.
- Select the checkbox to turn on AD SSO for the LAN zone. You can also turn on AD SSO for other zones if required.
- Click Apply.
Note
This creates an AD computer object on your domain.
Turn on Kerberos and NTLM authentication for web authentication
Allow browsers to authenticate using Kerberos and NTLM.
- Go to Authentication > Web authentication.
- Under If Active Directory (AD) SSO is configured, select Kerberos & NTLM.
- Click Apply.
Check Kerberos and NTLM connection
Use the log viewer to check if Kerberos and NTLM is working and that web requests are being authenticated correctly.
- Open Log viewer.
- In the drop-down list, select Authentication.
When the firewall initially connects with the AD server, it will log the messages Kerberos authentication initialized successfully and NTLM authentication channel established successfully.
AD SSO won't work if the message Cannot initialize Kerberos authentication or Cannot establish NTLM authentication channel appears. The firewall requires both NTLM and Kerberos to be configured and working correctly with the AD server before it offers either one to web clients. In this case, check the configured AD server. Try changing the Connection security to Plaintext, and make sure that the AD server account is a member of Domain Admins. More detailed error messages may be available on the AD server for why the server refuses the connection.
Successful authentications are shown in this log if you configure web requests to require web authentication. The Log Comp column indicates if the client uses NTLM or Kerberos.
Note
If you want the client to use Kerberos, but it's using NTLM, the client may not be matching the Service Principal Name (SPN). On the client, run the command setspn -Q HTTP/*. For transparent mode, the configured redirection URL must match the SPN. For standard mode, the proxy configured in the browser must match the SPN.