Web authentication
You can use Active Directory SSO or the captive portal to authenticate users. Users will then appear in logging and reporting and will be used as matching criteria in firewall rules and web policies.
Active Directory single sign-on (SSO) attempts to silently authenticate users signed in to endpoint devices with Sophos Firewall without user interaction.
The captive portal is a web page that requires users behind the firewall to authenticate when attempting to access a website. You can also define the behavior and layout of the captive portal.
The maximum username and password length for the captive portal is 50.
Captive portal URL: https://<IP address of Sophos Firewall>:8090
After authenticating with the captive portal, Sophos Firewall allows users to proceed to their requested destination or redirects them to a URL that you specify.
To view authenticated users, go to Current activities > Live users.
Note
If multi-factor authentication (MFA) is configured, users must first sign in to the user portal and set up their one-time password (OTP). They can then sign in to the captive portal using their password and OTP token. See Multi-factor authentication (MFA) settings.
Authorize unauthenticated users for web access
The settings that you specify here are implemented based on the firewall rules and the web policies for unknown users and authenticated users and user groups.
| Firewall rule setting: Use web authentication for unknown users | Behavior |
|---|---|
| On | For unauthenticated web requests that match the firewall rule, the users will be authenticated. |
| Off | Unauthenticated requests are allowed. If the requests are blocked due to the web policy, users will be authenticated. |
| Reason for authentication | AD SSO configured | Behavior |
|---|---|---|
| Firewall rule applies. | Yes | When unauthenticated web requests are made, AD SSO attempts to silently authenticate users signed in to endpoint devices. If authentication fails, requests are redirected to the captive portal. Once the users are authenticated, the page is reloaded and the users’ web policy is re-evaluated. |
| A web policy specified for unknown users or groups applies and is set to Block. | Yes | |
| Firewall rule applies. | No | When unauthenticated web requests are made, the requests are redirected to the captive portal. |
| Web policy for unknown users or groups is set to Block. | No | When unauthenticated web requests are blocked, a block page is displayed. You can show the captive portal link on the block page. |
Sophos Firewall supports two AD SSO mechanisms, NTLM and Kerberos. Kerberos is faster and more secure than NTLM, but has more prerequisites.
| Option | Description |
|---|---|
| NTLM only | Includes only NTLM in authentication headers. Use this option if you have legacy clients that can’t handle Kerberos headers. |
| Kerberos & NTLM | Default Includes both NTLM and Kerberos in authentication headers. Browsers choose which mechanism to use. |
Note
If Active Directory is configured, you can turn on access to AD SSO from specific network zones, for example, LAN. Go to Administration > Device access and select the zones under Local service ACL.
Captive portal behavior
Specify the captive portal settings.
Note
If you have an IPv4 and IPv6 (dual-stack) network, users must sign in for IPv4 and IPv6 websites separately.
Show user portal link
Shows the user portal link on the captive portal page.
Show web page after sign-in
Redirects users after authentication to the page they’ve requested or a custom page.
Open web page
| Option | Description |
|---|---|
| In new browser window | Opens the web page in a new browser window. The captive portal page remains open. |
| In captive portal window | Opens the web page in the current tab, replacing the captive portal page. |
Web page
| Option | Description |
|---|---|
| Originally requested by user | Opens the web page originally requested by the users before they were redirected to the captive portal. |
| Custom | Specify a page to which the users are redirected. For example, open an internal home page after the sign-in. |
Sign out user
| Option | Description |
|---|---|
| When captive portal page is closed or redirected | The captive portal sends a logout message to Sophos Firewall if the user clicks the Logout button, closes the captive portal page, or opens a new web page in the captive portal browser tab. The captive portal page sends periodic keepalive messages to Sophos Firewall to indicate that the computer is still on the network. The firewall signs the user out when it stops receiving keepalive messages, which can happen when a laptop goes to sleep or disconnects from the network. |
| When user is inactive | Specify the amount of data transfer within a time frame for a user to be considered active. Sophos Firewall signs the user out when the user is inactive or if the user clicks the Logout button. |
| Never | Users are never signed out automatically. To sign out, users must click the Logout button. |
Use insecure HTTP instead of HTTPS
Allows users to access the captive portal through HTTP.
We recommend that you use HTTPS. Transmitting unencrypted passwords over a network poses a severe security risk.**: Sophos Firewall comes with a preinstalled locally-signed HTTPS certificate. To prevent browser certificate warnings, you can replace it with a certificate that you’ve generated (and distributed to ensure client trust) or purchased from a certificate authority.
To save changes, select Apply.
Note
Microsoft Entra ID (Azure AD) SSO isn't supported if you select this option.
Authentication settings for direct web proxy
Allows per-connection authentication for the specified multi-user hosts. A multi-user host is an endpoint or server on which multiple users can sign in at the same time.
Note
If you have Match known users selected in your firewall rule, you must create a separate firewall rule for your multi-user hosts with this feature turned off.
Use per-connection AD SSO authentication for multi-user hosts
Allows you to specify multi-user hosts that will use per-connection authentication.
Note
If you've selected this option, you must select an AD server under Authentication > Services > Firewall authentication methods.
Multi-user hosts
Allows you to choose, create, or edit the following network object types:
- IP host group
- IP
- IP list
- IP range
- Network
You must consider the following when configuring multi-user hosts:
- IP addresses assigned to multi-user hosts only use per-connection authentication for direct proxy connections.
- IP addresses assigned to multi-user hosts can't use any other per-IP authentication method, for example, STAS, Clientless user, Captive portal, transparent AD SSO, and so on.
- Sophos Firewall treats connections from IP addresses assigned to multi-user hosts that aren't direct proxy connections as unauthenticated.
- Connections from IP addresses not assigned to multi-user hosts continue to use per-IP authentication based on your configuration.
Captive portal appearance
You can customize the appearance and content of the captive portal. For example, you can specify your company logo and custom text. Select the Preview button at the bottom to see what the page will look like to users.
| Option | Description |
|---|---|
| Default layout | Uses the default Sophos layout. |
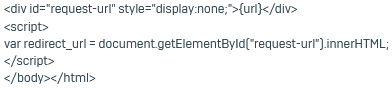
| Custom HTML | Select to edit the HTML and CSS code. You can also use JavaScript. The code must contain the following elements:
|
| Default logo | Uses the Sophos logo. |
| Custom logo | Select to use your own logo. Upload an image or enter a link to your logo. |
| Sign-in page header HTML | Enter the text to be shown above the sign-in box. You can use HTML. Use Header and footer text color to customize the font color. |
| User prompt | You can change the default text. |
| Username field label | You can change the label of the username field. |
| Password field label | You can change the label of the password field. |
| Sign-in button label | You can change the label of the sign-in button. |
| Sign-out button label | You can change the label of the sign-out button. |
| User portal link label | You can change the name of the user portal link. |
| Sign-in page footer HTML | Enter the text to be shown below the sign-in box. You can use HTML. Use Header and footer text color to customize the font color. |
| Background color | You can change the background color of the full page. |
| Header and footer text color | You can change the font color of the header and the footer. It will be visible only if you’ve specified a header or footer. |
| Custom logo background color | You can change the background color of the box that contains the logo. |
| User prompt text color | You can change the font color of the user prompt. |
| User portal link text color | You can change the font color of the user portal link. |
To save the settings, select Apply.
To erase custom settings, select Reset to default.