Add a certificate signing request
You can generate certificate signing requests (CSR) on the firewall.
You can generate a certificate signing request (CSR). An external CA can issue a certificate or a subordinate CA based on the CSR.
- Go to Certificates > Certificates and click Add.
- For Action, select Generate certificate signing request (CSR).
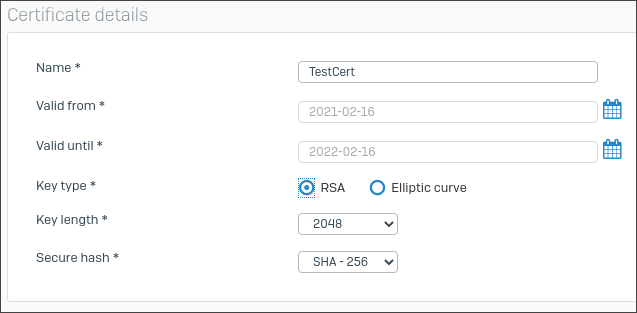
Certificate details
- Enter a name.
-
For Key type, select one of the following:
- RSA
- Elliptic curve
-
Select the Key length (for RSA) or Curve name (Elliptic curve).
Larger RSA keys offer greater security but take longer to encrypt and decrypt data.
-
Select a Secure hash algorithm.
Here's an example. You must enter your domain's details.
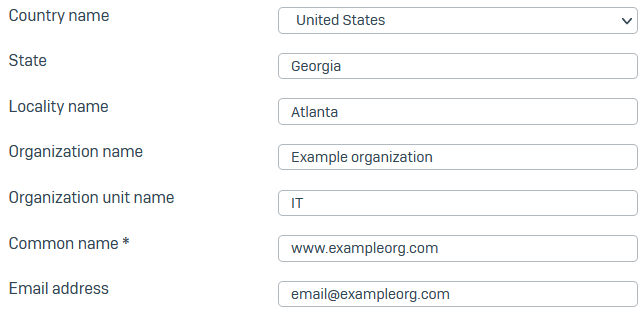
Subject name attributes
You must enter a common name. The firewall automatically fills all other fields with the details from your license. You can change these if you want.
- Country name: Enter the country in which the firewall is deployed.
- State: Enter the state or region.
- Locality name: Enter the city.
- Organization name: Enter the certificate owner's name (example:
Sophos Group) - Organization unit name: Enter the name of the department to which you'll assign the certificate (example:
Marketing). - Common name: Enter the hostname or FQDN (example:
marketing.sophos.com). -
Enter the contact person's email address.
Here's an example:
The distinguished name shows the certificate's configured details and is dynamically updated when you make changes.
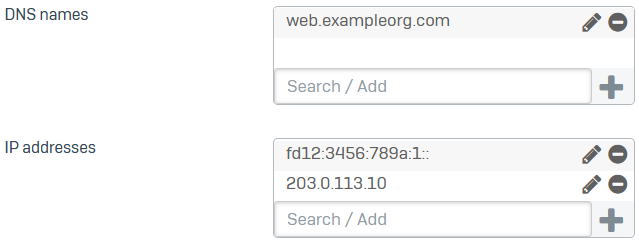
Subject Alternative Names (SAN)
You must enter at least one SAN or a certificate ID.
-
Enter a DNS name, IPv4, or IPv6 address, and click
 .
.Subject alternative names (SANs) define the DNS names and IP addresses the certificate secures.
Here's an example. You must enter your domain's details.
-
(Optional) If you're generating a certificate to use with earlier versions of SFOS, do as follows:
- Click Advanced settings.
-
For Certificate ID, select from the following options and enter the ID:
- DNS: Enter a domain name. The name must resolve to the IP address in the DNS records.
- IP address: A public IP address that you own.
- Email: Contact person's email address.
- DER ASN1 DN [X.509]: Use this if you specify a digital certificate to secure an object.
-
Click Save.
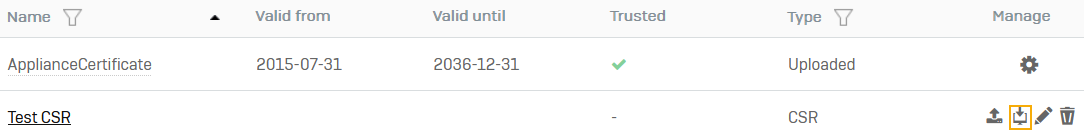
The CSR is added to the certificates list.
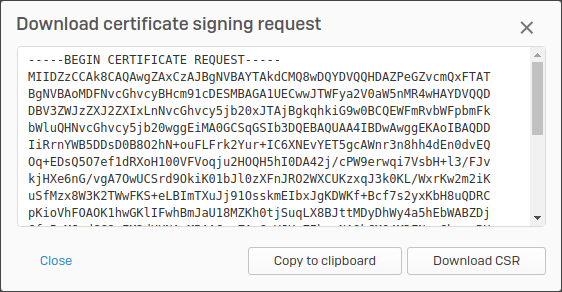
Copy or download CSR
-
On the certificates list, click
 for the CSR.
for the CSR.A dialog box shows the certificate signing request.
-
Copy or download the CSR (
.csrfile).
Next steps
- Use the copied or downloaded CSR to get a signed certificate or subordinate CA from a root CA. See Add subordinate and root CAs for TLS traffic.
- Import it to the firewall. See Import a certificate.
To generate a CSR for a Let's Encrypt™ certificate, do as follows:
- Go to Certificates > Certificates and click Add.
- For Action, select Request Let's Encrypt certificate.
- Enter a name.
-
In Domains, specify the domains for which you want to use the certificate. You can only enter FQDNs.
Domain validation is based on the HTTP-01 method, which doesn't support IP addresses and wildcard domains.
-
In Hosted address, select the public IP address of the WAN interface to which the domains resolve.
Because a domain validation request is sent to this IP address over port 80, make sure the following conditions are met:
- If the firewall is behind a router with the public IP address, create a DNAT rule on the router that translates the public IP address over port 80 to the firewall's WAN interface. This ensures the validation request reaches the firewall.
- To respond to the request, the firewall can't have a DNAT rule for this IP address on port 80.
-
Click Save.
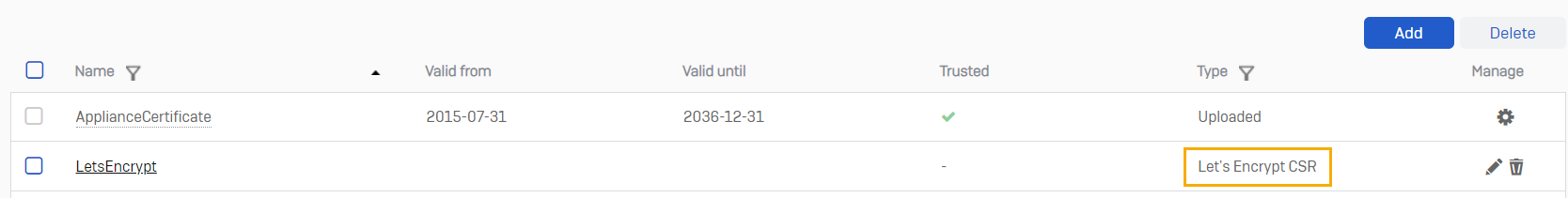
Certificate details
On the Certificates page, the Type column shows Let's Encrypt CSR for this CSR.
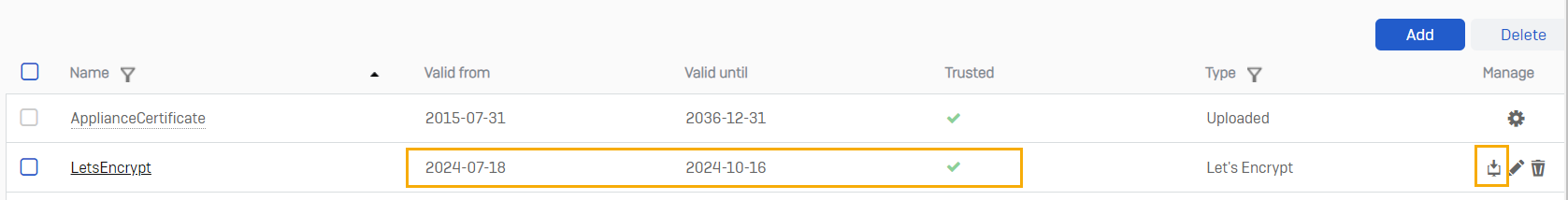
It takes a few minutes for the CA to validate the CSR. After it's validated, the Valid from and Valid until columns show the validity dates and the Trusted column shows a green tick mark. You can now click Download ![]() to download the certificate.
to download the certificate.
Warning
You can't edit the CSR if the domain is invalid or doesn't exist. In these cases, you must delete the CSR and create a new one.
Let's Encrypt is a trademark of the Internet Security Research Group. All rights reserved.