Protect internal mail server in legacy mode
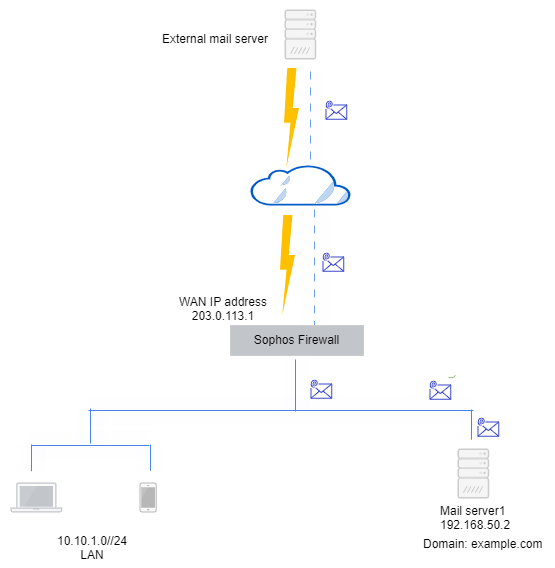
Configure Sophos Firewall to act as a transparent email proxy and route emails from the internet to an internal mail server.
Protect mail server in legacy mode
In legacy mode, Sophos Firewall acts as a transparent proxy. You can specify SMTP malware and spam scan policies and POP/IMAP scan policies. You must configure the following rules and policies:
- Firewall rules to allow incoming and outgoing traffic.
- NAT rules to translate IP addresses for incoming and outgoing traffic.
- SMTP settings
- SMTP malware and spam scan policies. This is optional.
- POP/IMAP scan policies. This is optional.
An example network diagram is as follows:
Create a firewall rule to allow email traffic
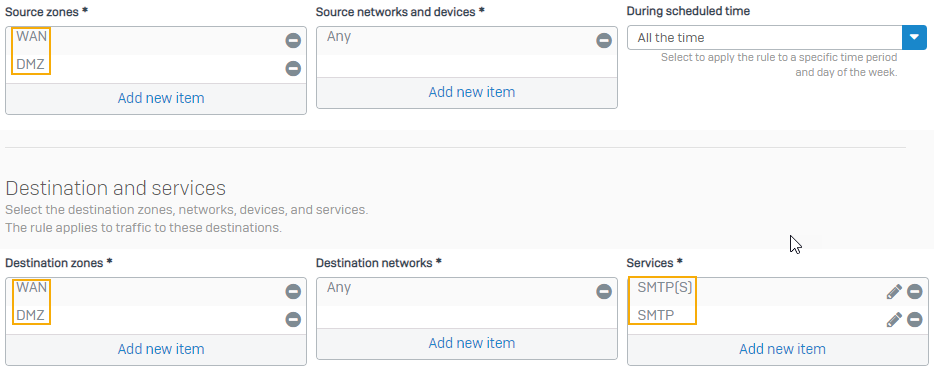
Create a firewall rule to allow SMTP and SMTPS traffic between the DMZ and WAN zones. You must add these zones to the source and destination zones to allow incoming and outgoing emails.
- Go to Rules and policies > Firewall rules and click Add firewall rule.
- Under Source zones, select DMZ and WAN.
- Under Destination zones, select WAN and DMZ.
-
Under Services, select SMTP and SMTPS.
Here's an example:
-
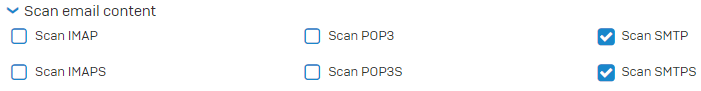
Under Scan email content, select Scan SMTP and Scan SMTPS.
Here's an example:
-
Click Save.
Create NAT rules to translate server IP address
Create a NAT rule to translate the WAN port's IP address to the internal mail server for incoming traffic. Select the reflexive rule to create a NAT rule automatically to masquerade the internal mail server's IP address for outgoing traffic.
- Go to Rules and policies > NAT rules. Select IPv4 or IPv6 and then select Add NAT rule.
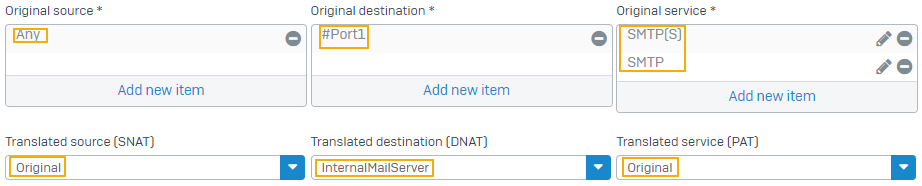
- Under Original source, select Any.
- Under Translated source (SNAT), select Original.
- Under Original destination, select the WAN interface.
-
Under Translated destination (DNAT), select the internal mail server.
You must create an IP host for the internal mail server to see it in the list.
-
Under Original service, select SMTP and SMTP[S].
-
Under Translated service (PAT), select Original.
Here's an example:
-
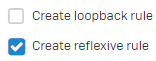
Select Create reflexive rule to create an SNAT rule masquerading traffic from the internal mail server to the external server.
-
Click Save.
Configure SMTP settings and scanning policies
Configure the SMTP settings. You can also specify the SMTP malware scan policies. You can specify the SMTP spam scan and POP/IMAP scan policies based on your need.
-
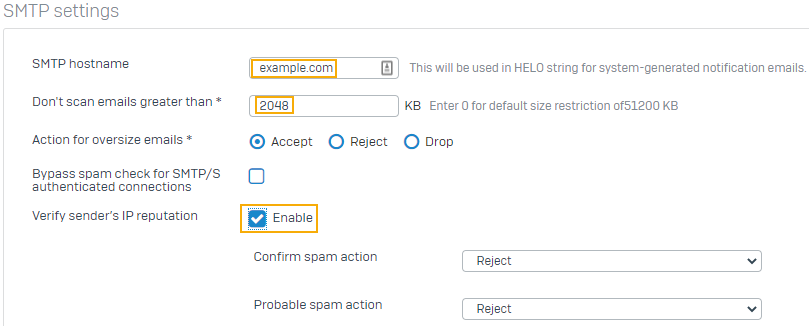
Go to Email > General settings > SMTP settings.
-
Go to Email > SMTP malware scan.
-
Select the recipient domain.
You can click Create new and configure an address book for the domain.
-
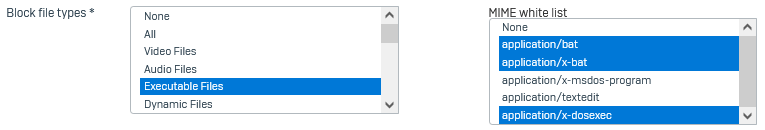
For Block file types, select Executable files.
-
Under MIME allow list, select the file types you don't want to block.
Here's an example:
-
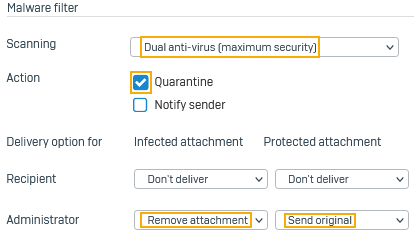
For Scanning, select Dual antivirus.
- For Action, select Quarantine.
- For the administrator setting under Infected attachment, select Remove attachment.
-
For the administrator setting under Protected attachment, select Send original.
Here's an example:
-
-
Configure SMTP and POP/IMAP spam scanning policies based on your need.
Sophos Firewall offers some default policies. You can see them on the policy list. Sophos Firewall processes them in the order shown. To change a policy's position in the list, drag and drop it.