DoS & spoof protection
To prevent spoofing attacks, you can restrict traffic to only recognized IP addresses, trusted MAC addresses, and IP-MAC pairs. You can also set traffic limits and flags to prevent DoS attacks and create rules to bypass DoS inspection. The firewall logs dropped traffic.
- To protect against spoofing attacks, select Enable spoof prevention, specify settings and zones, and click Apply. To drop traffic from an unknown IP address on a trusted MAC address, select Restrict unknown IP on trusted MAC.
- To add a trusted MAC address, scroll to Spoof protection trusted MAC and click Add. To import addresses, click Import.
- To protect against DoS attacks, scroll to DoS settings, specify settings, and click Apply. To view the current status of DoS attacks, click the link provided.
- To bypass DoS inspection for a specified IP address or port, scroll to DoS bypass rule and click Add.
Spoof protection general settings
Specify the type of spoof prevention and the zones that you want to protect.
IP spoofing: If the source IP address of a packet does not match any entry on the firewall’s routing table or if the packet isn't from a direct subnet, the firewall drops the packet.
MAC filter: If the packet doesn't specify a MAC address that's listed as a trusted MAC address, the firewall drops the packet. To select MAC filter, you must add at least one trusted MAC address.
Note
MAC filter doesn't apply to DHCP packets.
IP–MAC pair filter: An IP–MAC pair is a trusted MAC address bound to an IP address. For a match to occur, an incoming packet's IP and MAC address must match an IP–MAC pair. If there's no trusted MAC configured, all traffic is allowed since IP–MAC pair filter only blocks if there's an IP-MAC pair mismatch.
If you select IP-MAC pair filter for some zones, Restrict unknown IP on trusted MAC behaves as follows:
| Restrict unknown IP on trusted MAC | Behavior |
|---|---|
| Selected | Drops a packet from a trusted MAC without IP binding but uses an unknown IP address. Unknown IP addresses are those that aren't in the firewall's routing table or aren't from a direct subnet. |
| Cleared |
|
Spoof protection trusted MAC
Use trusted MAC addresses with the MAC filter setting to allow traffic for specified hosts.
When you bind a trusted MAC address to an IP address, the firewall matches traffic with the IP–MAC pairs and filters traffic based on the settings specified for the IP–MAC pair filter.
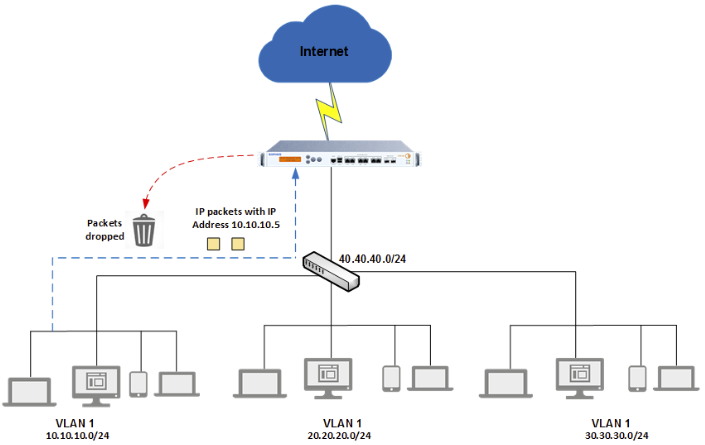
Spoof protection workflow
In the network diagram, a core switch with Sophos Firewall as the default gateway handles inter-VLAN routing. The firewall isn't connected to any inter-VLAN routes.
The workflow is as follows:
- A user in VLAN 1 with the IP address 10.10.10.5 tries to access
www.google.com. -
The firewall receives the request on its LAN interface and checks for the following conditions:
- A route entry for the packets received from 10.10.10.5.
- The source IP address of the packet is part of a directly connected subnet.
-
It drops the packets received from 10.10.10.5 if the IP spoofing conditions aren't fulfilled.
Denial-of-Service (DoS)
A DoS attack makes a device or network resource unavailable to its users. A common method of attack involves saturating a device with a vast number of requests so that it can't respond to legitimate traffic or the device responds so slowly that it's useless.
DoS attacks can be done in the following ways:
- ICMP flood: In this method, the attackers send large numbers of IP packets with the source addresses appearing as the legitimate users' addresses. The network's bandwidth is quickly used up, preventing legitimate packets from reaching their destination.
- SYN/TCP flood: This attack occurs when a device sends a flood of TCP/SYN packets, often with a forged sender address. Every packet is handled like a connection request. This causes the server to spawn a half-open connection by sending back a TCP/SYN-ACK packet (Acknowledge) and waiting for a response packet from the sender address. However, the response never comes since the sender's address is forged. These half-open connections occupy the number of available connections the server can make and keep it from responding to legitimate requests until after the attack ends.
- UDP flood: A UDP flood attack can be started by sending many UDP packets to random ports on a target device. The target device is then forced to send many ICMP packets because of the large number of UDP packets, eventually making it unreachable by other clients.
Distributed Denial-of-Service (DDoS)
A DDoS attack happens when multiple legitimate or compromised devices perform a DoS attack on a single device. This distributed attack can compromise the target device or force it to shut down along with its services to legitimate users.
DoS settings
You can specify limits on sent and received traffic and flag DoS attacks to prevent flooding of network hosts.
Tip
Specify limits based on your network specifications. Values that exceed your available bandwidth or server capacity may affect performance. Values that are too low may block valid requests.
| Name | Description |
|---|---|
| SYN flood | High rate of SYN requests, forcing the target server to create increasing number of half-open connections. |
| UDP flood | High rate of UDP packets, forcing the target host to check for the application listening at the port and reply with an increasing number of ICMP packets. |
| TCP flood | High TCP packet rate. |
| ICMP/ICMPv6 flood | High rate of ICMP/ICMPv6 echo requests. |
| Dropped source routed packets | Drops packets for which the sender specifies the packet route, preventing attackers from manipulating the routing tables. |
| Disable ICMP/ICMPv6 redirect packet | Won't accept ICMP and ICMPv6 redirect packets to prevent attackers from manipulating the routing tables. Downstream routers send these packets to inform Sophos Firewall of an optimal or active route to a destination. |
| ARP hardening | Allows ARP replies only when the source and destination IP addresses belong to the same subnet. It prevents ARP flood and ARP poisoning. |
Packet rate: Number of packets that each host can send or receive per minute.
Burst rate: Occasional traffic spike allowed above the packet rate to each host.
Note
With burst rate, you can allow traffic to exceed the packet rate occasionally. However, the firewall doesn’t allow frequent or sustained spikes above the packet rate.
Apply flag: Apply the traffic limit specified for the protocol.
Traffic dropped: Number of source or destination packets dropped. The statistics are accumulated since the last Sophos Firewall restart.
DoS bypass rule
You can bypass DoS settings for known hosts for the specified ports and protocols. For example, you can allow traffic of a VPN zone or specific hosts of the VPN zone to bypass DoS inspection.
Additional information
Packet rate: Sophos Firewall allows TCP traffic for a specific source or destination if packets come in below the rate given. Otherwise, Sophos Firewall drops the traffic.
Burst rate: Sophos Firewall allows this amount of packets initially, without checking the packet rate.
DoS protection works on a source or destination basis, so the packet rate and burst rate apply to either source or destination.
The firewall checks for a bypass rule first and then applies DoS protection to the remaining traffic.
The firewall retains DoS attack data for 30 seconds after the attack stops.
Sample flow
- Sophos Firewall allows the first 100 packets (up to burst rate), and after 100 packets, it checks the rate of the incoming packets. If the packets come below the configured packet rate, Sophos Firewall accepts them. If the packets come above the configured packet rate, Sophos Firewall declares the traffic as an ARP flood attack attempt and drops the packets.
- When a new packet arrives from the IP address that generated the traffic, Sophos Firewall checks whether the last packet from the same source arrived within thirty seconds.
- If the last packet arrived within thirty seconds, Sophos Firewall drops the packet and logs it as an ARP flood attack attempt.
- If the last packet didn't arrive within thirty seconds, Sophos Firewall excludes the source and allows traffic. If Sophos Firewall doesn't receive any traffic from the source IP address after thirty seconds, it isn't added to the allow list, and traffic from that IP address is still classed as an ARP flood attack attempt.
More resources