Send DHCP traffic over policy-based IPsec VPN to servers
Configure Sophos Firewall as the DHCP relay agent to forward DHCP packets between clients and the DHCP server behind the head office firewall.
Introduction
When you configure Sophos Firewall as a DHCP relay agent, it enables the DHCP server to lease IP addresses to clients in a different subnet from the server.
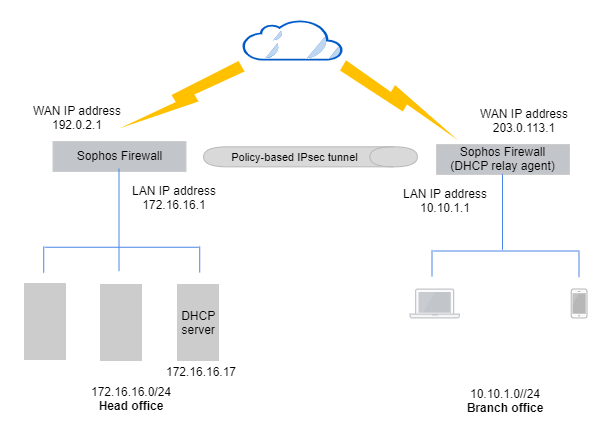
DHCP relay: Network diagram
In this example, we use a Windows Server that's configured as the DHCP server. The network details are as follows:
Head office:
- WAN IP address:
192.0.2.1 - DHCP server IP address:
172.16.16.17 - LAN subnet:
172.16.16.0/24
Branch office:
- WAN IP address:
203.0.113.1 - DHCP relay agent's interface:
10.10.1.1 - LAN subnet:
10.10.1.0/24
Branch office: Configure a DHCP relay agent
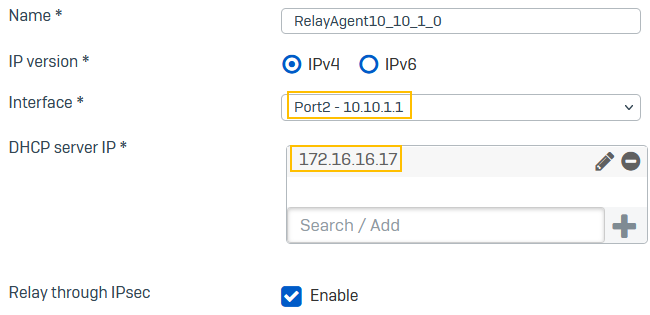
Configure the branch office Sophos Firewall as the DHCP relay agent. In this example, it relays the IP addresses leased by the DHCP server to branch office clients. The DHCP server is deployed at the head office.
- Go to Network > DHCP.
- Under Relay, click Add.
-
For Interface, select the client-side interface. The server responds if the lease range it holds belongs to the subnet of this interface.
Example:
Port2 - 10.10.1.1 -
Enter the IP address for DHCP server IP.
Example:
172.16.16.17 -
Select Relay through IPsec.
Here's an example:
Branch office: Configure an IPsec connection
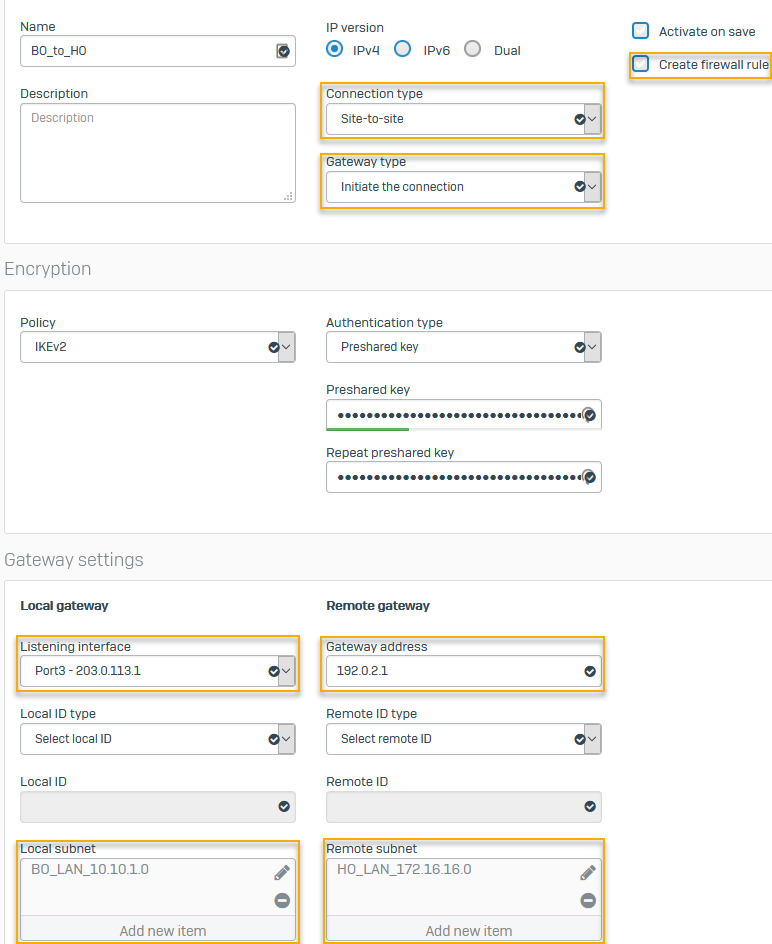
On the branch office firewall, configure a site-to-site IPsec connection to the head office.
- On the web admin console, go to Site-to-site VPN > IPsec > IPsec connections and click Add.
-
The following settings are an example. You must specify your network's settings:
Name Setting Connection type Site-to-siteGateway type Initiate the connectionCreate firewall rule Clear the checkbox.
Firewall rules don't control system-generated traffic.
Authentication type Preshared keyEnter the key you specified in the head office firewall.
Listening interface Port3 - 203.0.113.1Gateway address 192.0.2.1Local subnet 10.10.1.0Remote subnet 172.16.16.0Here's an example:
Branch office: Add an IPsec route
On the branch office firewall, add an IPsec route for system-generated traffic to the DHCP server at the head office. Apply source NAT on the system-generated traffic to translate the internal source IP address at the branch office to the destination IP address (DHCP server at the head office).
- On the CLI, enter 4 for Device console.
-
Add an IPsec route from the branch office firewall to the DHCP server in the head office. Enter the following:
system ipsec_route add host <IP address of host> tunnelname <tunnel>Example
system ipsec_route add host 172.16.16.17 tunnelname BO_to_HO -
Translate the IP address of the LAN port (DHCP relay interface) of the branch office firewall to the DHCP server's IP address at the head office. You must use this command to translate traffic generated by Sophos Firewall. Enter the following:
set advanced-firewall sys-traffic-nat add destination <Destination IP address or network> snatip <Source IP address to translate>Example
set advanced-firewall sys-traffic-nat add destination 172.16.16.17 snatip 10.10.1.1
Head office: Configure a site-to-site IPsec connection
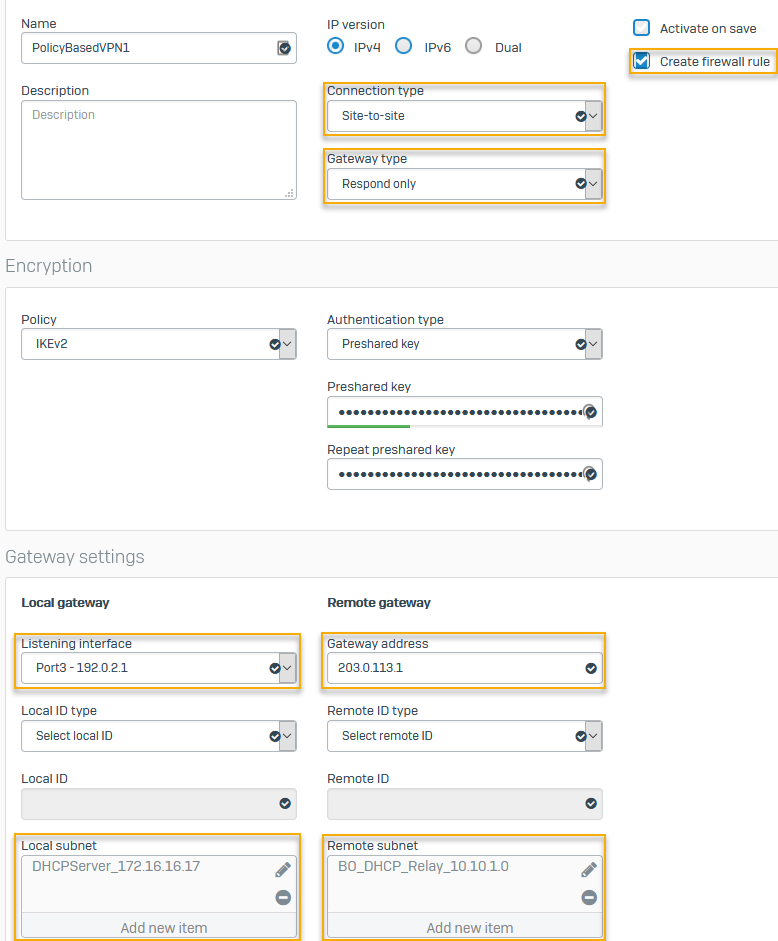
On the head office firewall, configure a site-to-site IPsec connection to the branch office.
- On the web admin console, go to Site-to-site VPN > IPsec > IPsec connections and click Add.
-
The following settings are an example. You must specify your network's settings:
Name Setting Connection type Site-to-siteGateway type Respond onlyTo allow WAN traffic to access the IPsec tunnel, go to Administration > Device access and make sure you select WAN under IPsec.
Create firewall rule Select the checkbox. Authentication type Preshared keyEnter the key you specified in the branch office firewall.
Listening interface Port3 - 192.0.2.1Gateway address 203.0.113.1Local subnet 172.16.16.17Remote subnet 10.10.1.0Here's an example:
Head office: Outbound firewall rule
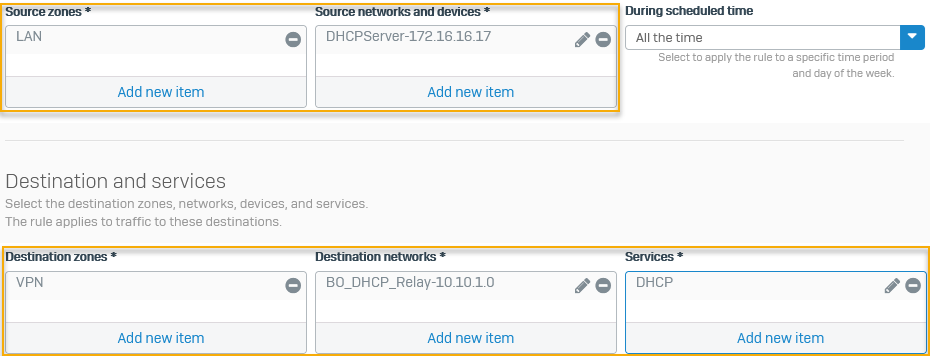
Edit the automatically created firewall rule on the head office firewall to allow outbound DHCP communication from the DHCP server to the branch office's DHCP relay agent.
Select the following:
- Source zones:
LAN - Source networks and devices:
DHCPServer-172.16.16.17 - Destination zones:
VPN - Destination networks:
BO_DHCP_Relay-10.10.1.0 -
Services:
DHCPHere's an example:
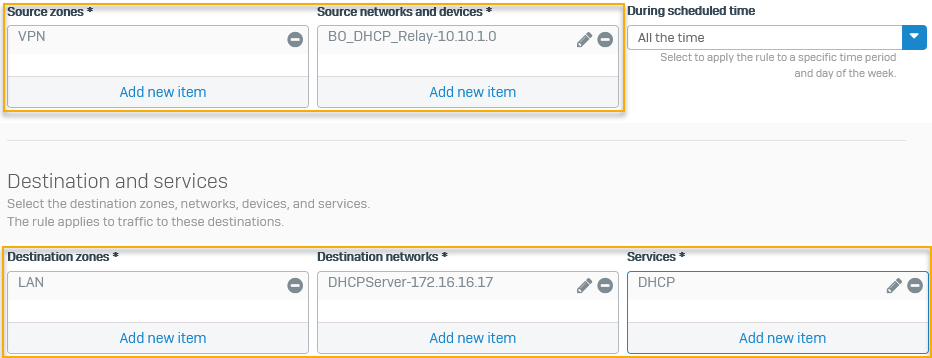
Head office: Inbound firewall rule
Configure a firewall rule on the head office firewall to allow inbound DHCP communication to the DHCP server from the branch office's DHCP relay agent.
Select the following: