Send DHCP traffic over route-based VPN to DHCP servers
Configure Sophos Firewall as the DHCP relay agent to forward DHCP requests from clients to the DHCP server behind the head office firewall. Send DHCP traffic over a route-based IPsec VPN connection.
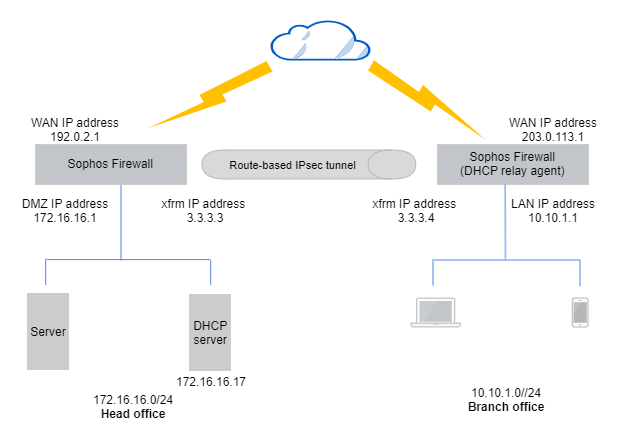
DHCP server and relay agent: Network diagram
The network details and settings are an example. You must use your network settings.
This example uses existing route-based IPsec VPN connections in which the local and remote subnets are set to Any. It also uses existing routes and firewall rules for the VPN traffic.
Head office: The following are example IP addresses.
- WAN IP address:
192.0.2.1 - DHCP server interface:
172.16.16.1
Branch office: The following are example IP addresses.
- WAN IP address:
203.0.113.1 - DHCP relay agent interface:
10.10.1.1 - LAN subnet:
10.10.1.0/24
VPN requirements
Configure the following on the head office and branch office firewalls:
- Configure route-based IPsec VPN connections with local and remote subnets set to Any using the firewalls' WAN interfaces.
- Assign an IP address to the XFRM interface.
- Add a gateway IP address for the XFRM interface.
- Configure static, SD-WAN, or dynamic routes on both firewalls to route the VPN traffic.
- Allow device access from WAN for IPsec VPN tunnels.
-
Configure the following firewall rules to allow VPN traffic:
- Outbound rule in the branch office firewall.
- Inbound rule in the head office firewall.
Head office
In the head office firewall, configure a route and an inbound firewall rule.
Add a route
You can configure a static, SD-WAN, or dynamic route to route the DHCP server's reply traffic from the head office to the branch office using a route-based VPN tunnel.
This example shows how to configure an SD-WAN route.
- Go to Routing > SD-WAN routes.
- Select IPv4 and click Add.
- Enter a name.
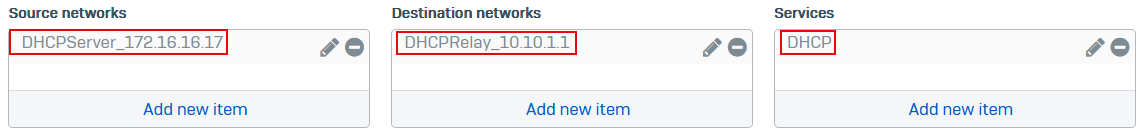
- Under Source networks, select the DHCP server, for example,
DHCPServer_172.16.16.17. - Under Destination networks, select the IP host you create for the DHCP relay agent, for example,
DHCPRelay_10.10.1.1. -
Under Services, select DHCP.
-
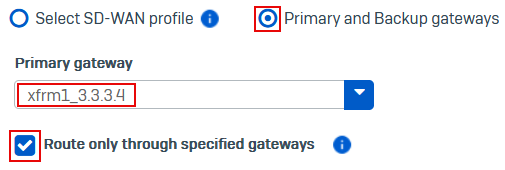
Under Link selection settings, select Primary and backup gateways.
-
Under Primary gateway, select the XFRM gateway, for example,
xfrm1_3.3.3.4. -
(Optional) To drop traffic if the XFRM gateway is unavailable, select Route only through specified gateways.
- Click Save.
Add a firewall rule
Create a firewall rule in the head office firewall to allow inbound DHCP traffic from the relay agent through the VPN as follows:
- Go to Rules and policies > Firewall rules, click Add firewall rule, and click New firewall rule.
- Enter a name.
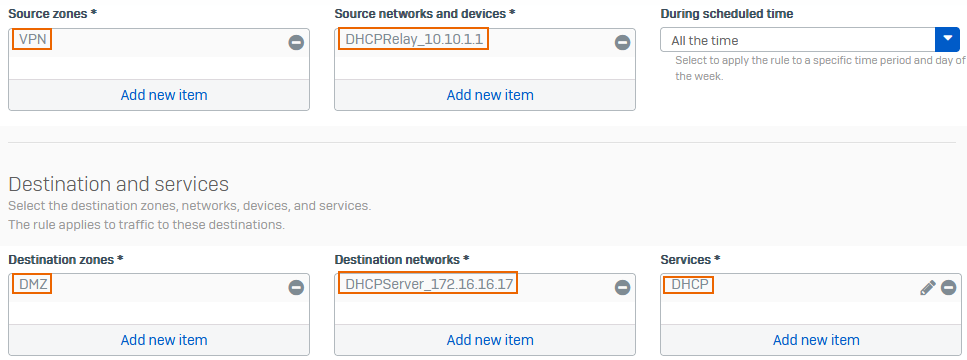
- Under Source zones, select VPN.
- Under Source networks and devices, select the IP host for the branch office firewall's DHCP relay interface, for example,
DHCPRelay_10.10.1.1. - Under Destination zones, select DMZ.
- Under Destination networks, select the DHCP server, for example,
DHCPServer_172.16.16.17. - Under Services, select DHCP.
-
Click Save.
Branch office
In the branch office firewall, configure a DHCP relay agent and a route.
Add a DHCP relay agent
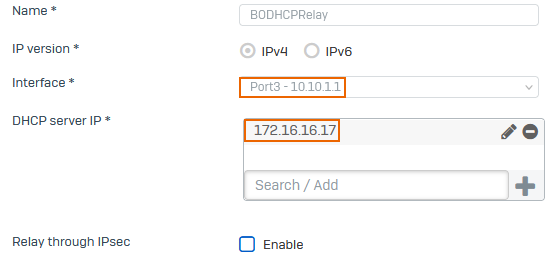
Configure the branch office firewall's interface as the DHCP relay agent. The interface forwards DHCP requests from endpoints in its subnet to the DHCP server behind the head office firewall.
- Go to Network > DHCP.
- Under Relay, click Add.
- Enter a name.
-
Select an Interface, for example,
Port2 - 10.10.1.1.The DHCP clients belong to the same subnet as the interface.
-
Under DHCP server IP, enter the DHCP server's IP address, for example,
172.16.16.17, and click .
. -
Click Save.
Add a route
You can configure a static, SD-WAN, or dynamic route to route the branch office interface's DHCP request traffic to the DHCP server in the head office using a route-based VPN tunnel.
This example shows how to configure an SD-WAN route.
- Go to Routing > SD-WAN routes.
- Select IPv4 and click Add.
- Enter a Name.
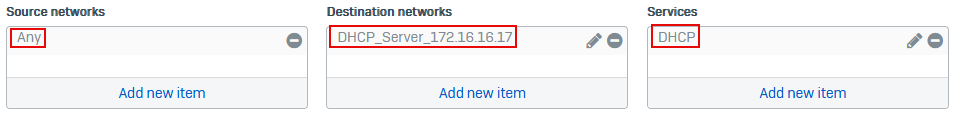
- Under Source networks, select Any.
- Under Destination networks, select the IP host you create for the DHCP server, for example,
DHCP_Server_172.16.16.17. -
Under Services, select DHCP.
-
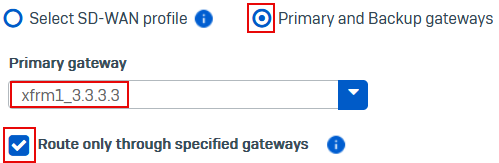
Under Link selection settings, select Primary and backup gateways.
-
Under Primary gateway, select the XFRM gateway, for example,
xfrm1_3.3.3.3. -
(Optional) To drop traffic if the XFRM gateway is unavailable, select Route only through specified gateways.
- Click Save.
More resources