Configure remote access SSL VPN as a split tunnel
You can configure remote access SSL VPN connections in split tunnel mode. Only traffic to the permitted network resources flows through the firewall.
Users can establish the connection using the Sophos Connect client.
Overview
The Sophos Connect client allows you to enforce advanced security and flexibility settings, such as connecting the tunnel automatically.
Preliminary configurations:
- Configure IP hosts for the local subnets.
- Configure users and groups. Alternatively, configure an authentication server.
- Check the authentication methods.
To configure and establish remote access SSL VPN connections using the Sophos Connect client, do as follows:
- Configure the SSL VPN settings.
- Send the configuration file to users.
- Add a firewall rule.
- Send the Sophos Connect client to users. Alternatively, users can download it from the VPN portal.
Restriction
Currently, the Sophos Connect client doesn't support macOS for SSL VPN. It also doesn't support mobile platforms for IPsec and SSL VPN. For these endpoints, you can use the OpenVPN Connect client. See Sophos Connect client: Compatibility with platforms.
Users must do as follows:
- Install the Sophos Connect client on their endpoint devices.
- Import the configuration file into the client and establish the connection.
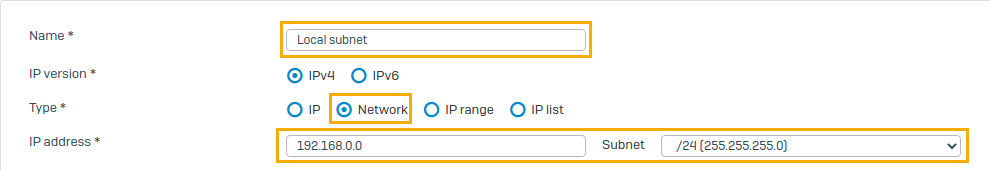
Create an IP host for local subnet
The local subnet defines the network resources that remote clients can access.
- Go to Hosts and services > IP host and click Add.
-
Enter a name and network for the local subnet.
-
Click Save.
Create a user group and add a user
You create a user group for the remote SSL VPN and add a user. The group specifies a surfing quota and access time. In this example, users in the group are allowed unlimited access.
- Go to Authentication > Groups and click Add.
-
Specify the settings.
Name Description Name Remote SSL VPN group Surfing quota Unlimited internet access Access time Allowed all the time -
Click Save.
- Go to Authentication > Users and click Add.
-
Specify the settings.
Name Description Username john.smith Name John Smith Group Remote SSL VPN group -
Click Save.
Check authentication services
In this example, you set the firewall and SSL VPN authentication methods to local authentication. Sophos Firewall then acts as the authentication server.
- Go to Authentication > Services.
-
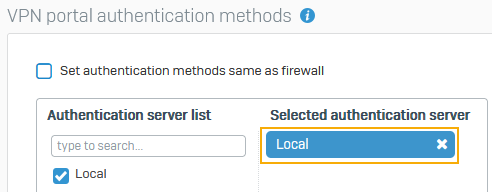
Under VPN portal authentication methods, do as follows:
- Clear Set authentication methods same as firewall.
- Check that the Selected authentication server is set to Local.
-
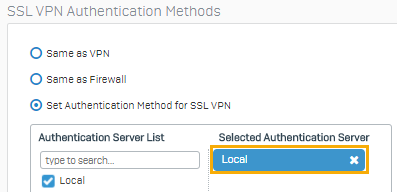
Scroll to SSL VPN authentication methods.
-
Check that the authentication server is set to Local.
Note
Alternatively, you can select an authentication server, such as the Active Directory server you've configured under Authentication > Servers.
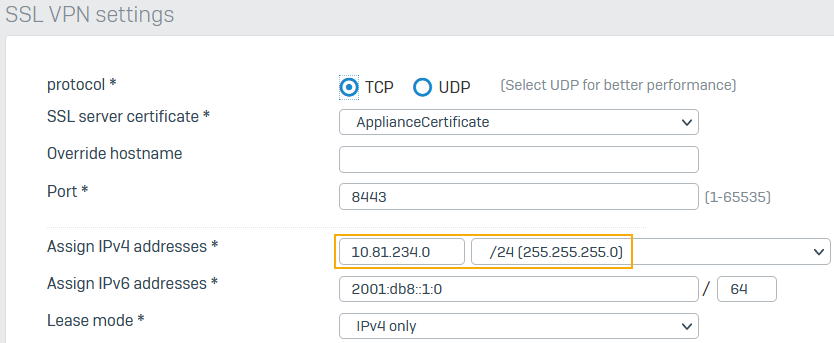
Specify a subnet for SSL VPN clients
When SSL VPN clients connect to Sophos Firewall, it assigns IP addresses from the subnet you specify here. You must use a private address.
-
Go to Remote access VPN > SSL VPN and click SSL VPN global settings.
-
Specify the private IP address and subnet to lease for remote users.
-
Click Apply.
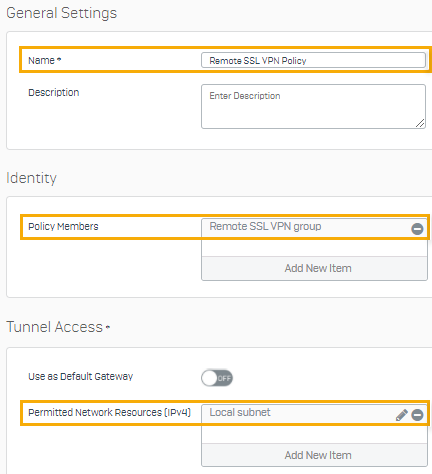
Add an SSL VPN remote access policy
You create a policy that allows users in the remote SSL VPN group to connect. These users are allowed to access resources on the local subnet.
- Go to Remote access VPN > SSL VPN and click Add.
- Click Configure manually.
- Enter a name.
- Select the policy members.
-
Select the permitted network resources that members are allowed to access.
-
Click Apply.
Add a firewall rule
- Go to Rules and policies > Firewall rules.
- Select IPv4 or IPv6.
- Click Add firewall rule and New firewall rule.
- Enter a rule name.
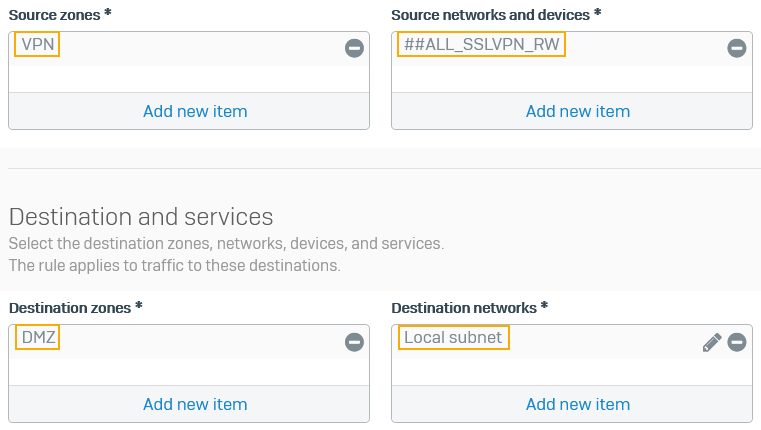
- For Source zone, select VPN.
-
For Source networks and devices, select ##ALL_SSLVPN_RW or ##ALL_SSLVPN_RW6.
These hosts contain the IP addresses leased to remote users who've established a connection.
-
For Destination zones, select the zones of the resources you want to give remote access to.
- For Destination networks, select the IP host you've created for the permitted network resources.
-
Click Save.
Here's an example:
Check device access settings
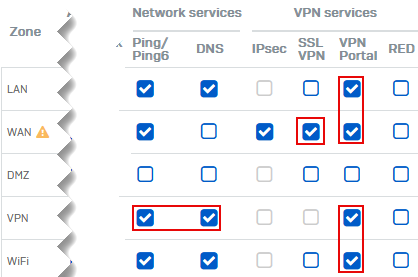
You must give access to some services for remote users from the required zones.
- Go to Administration > Device access.
-
Under SSL VPN, select WAN to allow remote users to establish SSL VPN connections.
-
Under VPN portal, select LAN, WAN, VPN, and Wi-Fi.
Users can access the VPN portal and download the VPN client and configuration files from these zones.
-
(Optional) Under Ping/Ping6, select VPN.
Users can ping the firewall's IP address through VPN to check connectivity.
-
(Optional) Under DNS, select VPN.
Users can resolve domain names through VPN if you've specified the firewall for DNS resolution in VPN settings.
-
Click Apply.
Install and configure Sophos Connect client on endpoints
To establish remote access SSL VPN connections, users must install the Sophos Connect client on their endpoint devices and import the .ovpn file to the client.
You can download the Sophos Connect client installer from the Sophos Firewall web admin console and share these with users. Alternatively, users can download the client from the VPN portal as follows:
- Sign in to the VPN portal.
- Click VPN.
-
Under Sophos Connect client, click Download for Windows.
Note
For information about which endpoint platforms the Sophos Connect client supports, see Sophos Connect client: Compatibility with platforms.
-
Click Download configuration for Windows, macOS, Linux to download the
.ovpnconfiguration file. -
Click the downloaded Sophos Connect client.
You can then see it in the system tray of your endpoint device.
-
Click the three dots button in the upper-right corner, click Import connection, and select the
.ovpnfile you've downloaded. -
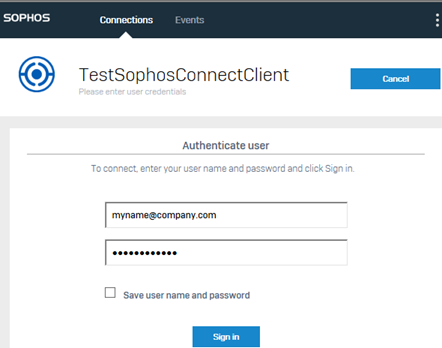
Sign in using your VPN portal credentials.
More resources