Troubleshooting - SD-WAN
Troubleshoot SD-WAN route problems.
Routing and connection issues
Traffic between internal networks routed to the WAN interface
Traffic from an internal network to another internal network is routed to a WAN interface when the following conditions occur:
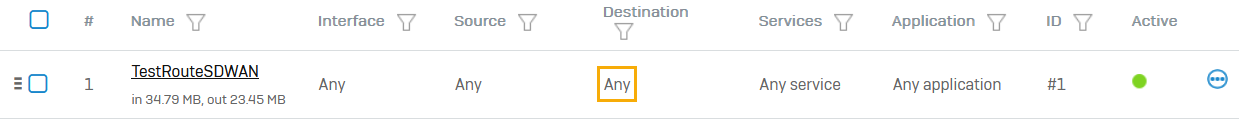
- Destination networks in an SD-WAN route is set to Any.
- Route precedence has SD-WAN route before static route.
Do as follows:
-
Set the Destination networks as follows:
- IPv4 routes: Select the default Internet IPv4 group or the individual internet IPv4 ranges.
- IPv6 routes: Select the specific destination IP hosts.
-
If you want to retain Any, create an SD-WAN route with specific destination IP hosts. Place this route above the Any route. Routes are enforced in the order shown.
-
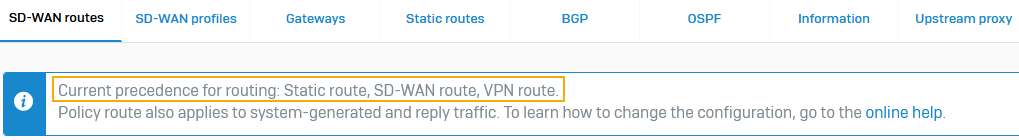
See the route precedence on Routing > SD-WAN routes.
If SD-WAN route is set before static route, a matching SD-WAN route is applied to directly connected network traffic. Static routes include directly connected networks.
Change the route precedence placing static route before SD-WAN route on the CLI.
Example
console> system route_precedence set static sdwan_policyroute vpn
Lost access to Sophos Firewall after creating an SD-WAN route
If you lost access to the web admin and SSH consoles of Sophos Firewall, check if all the following settings apply to your scenario. To regain access, you need to change any one of the settings.
-
Route precedence set to SD-WAN route before static route.
To see the route precedence, go to Routing > SD-WAN routes and see the box below the menu. The route precedence must be static route, then SD-WAN route. You can change the route precedence from the command-line console:
Example
console> system route_precedence set static sdwan_policyroute vpn -
Destination networks set to Any in the newly created SD-WAN route for a specific internal subnet. You can change the setting to a specific choice.
-
SD-WAN routing turned on for system-generated traffic.
Go to the command-line console and use this command:
show routing sd-wan-policy-route system-generate-trafficYou can turn off SD-WAN routing for system-generated traffic.
-
SD-WAN routing turned on for reply packets.
Go to the command-line console and use this command:
show routing sd-wan-policy-route reply-packetYou can turn off SD-WAN routing for reply packets.
If all these scenarios occur, Sophos Firewall enforces the generic SD-WAN route before static routes and implements it on system-generated traffic and reply packets. Access to the web admin and SSH consoles is lost from the internal subnet specified in the route. However, access is available from other subnets.
An SD-WAN route doesn't show up in the route table
If a migrated SD-WAN route or a route you created doesn't show any longer, do as follows:
- Check if you deleted the primary gateway specified in the route. Deleting an SD-WAN route's primary gateway deletes the route.
-
If it's a migrated route, check if you deleted the associated firewall rule.
Routing settings in firewall rules are migrated from 17.5 or earlier as migrated SD-WAN routes. These routes are associated with the original firewall rule. If you delete the firewall rule, the associated route is deleted.
Dead gateway detection in IPv6 routes
For IPv6 SD-WAN routes, dead gateway detection (DGD) doesn't monitor third-party network traffic (example: SNMP).
Web proxy issues
SD-WAN route doesn't match direct web proxy traffic
If you use direct web proxy mode, Sophos Firewall doesn't apply the SD-WAN route to match the following:
- Web traffic on the direct proxy port if you've set Services to HTTP (port 80) and HTTPS (port 443). You must set Services to Any.
Alternatively, do as follows:
- Check the direct proxy port on **Web** > **General settings**, under **Web proxy listening port**.
- On **Routing** > **SD-WAN routes**, add a service for the direct proxy port.
- A source network for reply packets.
- An incoming interface for reply packets.
You must configure at least one WAN interface (default gateway) or static route to match proxy traffic in the reply path for system-generated traffic.
Reporting
SD-WAN route only shows either request or reply traffic
SD-WAN routes only show a route's traffic count for traffic that matches the source and destination settings in the route. To see the request and reply traffic count, make sure the route's source and destination settings match request and reply traffic. See Request and reply traffic.