Send web requests through an upstream proxy in LAN
You can configure Sophos Firewall to send all web requests to the external network through an upstream proxy in the LAN or DMZ.
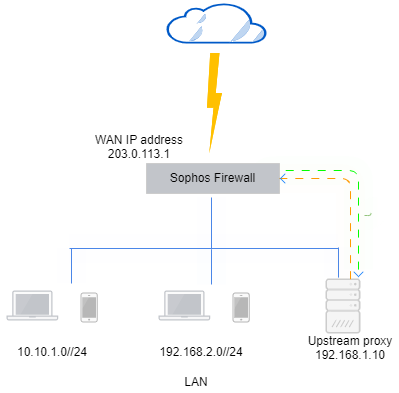
Connect Sophos Firewall to the upstream proxy in LAN
In this example, the upstream proxy is in the LAN zone. The network details are as follows:
Upstream proxy's IP address: 192.168.1.10
WAN IP address of Sophos Firewall: 203.0.113.1
When you deploy an upstream proxy in the LAN or DMZ, you must configure Sophos Firewall as a proxy server.
You must configure the following:
- Adding the upstream proxy to Sophos Firewall.
- Firewall rule for web filtering and scanning in web proxy mode.
- Firewall rule to allow traffic from internal users to the upstream proxy.
- Source NAT rule to masquerade traffic from internal users to the upstream proxy.
- Firewall rule to allow traffic from the upstream proxy to the internet.
Add the upstream proxy to Sophos Firewall
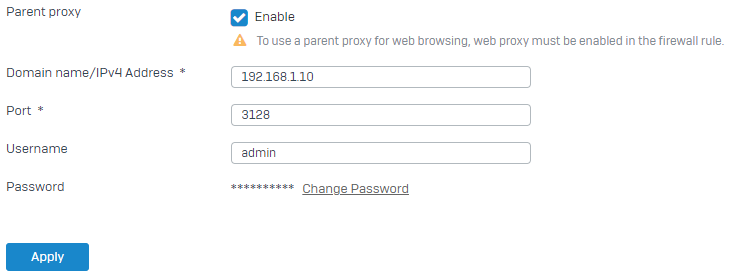
Add the upstream proxy to Sophos Firewall and enter the credentials if the proxy requires authentication.
- Go to Routing > Upstream proxy.
- Select Parent proxy.
- Enter the upstream proxy's IP address (example:
192.168.1.10). - Enter the port number the upstream proxy receives web traffic on (example:
3128). -
Enter the username and password if the upstream proxy requires authentication.
Here's an example:
-
Click Apply.
Create a firewall rule to scan web traffic
Create a firewall rule to scan and allow traffic between the internal users and WAN.
- Go to Rules and policies, click Add firewall rule > New firewall rule.
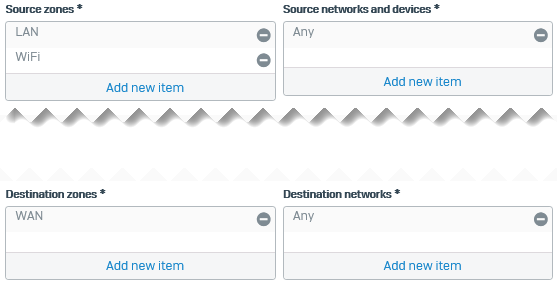
- Set Source zones to
LANandWi-Fi. - Set Source networks and devices to
Any. - Set Destination zones to
WAN. -
Set Destination networks to
Any.Here's an example:
-
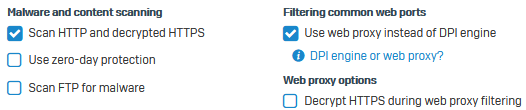
Select Scan HTTP and decrypted HTTPS and Use web proxy instead of DPI engine.
-
Click Save.
Create a firewall rule to allow internal traffic to the upstream proxy
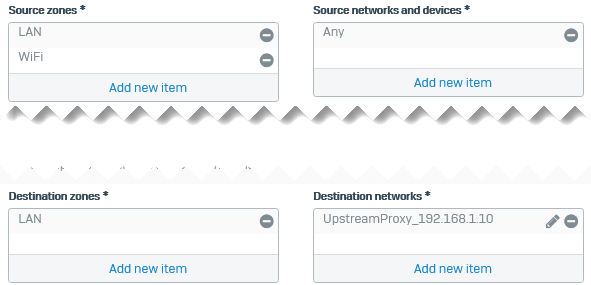
Create a firewall rule to allow traffic from the internal users to the upstream proxy in the LAN zone.
- Go to Rules and policies, click Add firewall rule, and click New firewall rule.
- Set Source zones to
LANandWi-Fi. - Set Source networks and devices to
Any. -
Set Destination zones to
LANsince the upstream proxy is in the LAN zone.If the upstream proxy is in the DMZ, set Destination zones to DMZ.
-
Set Destination networks to the IP host you create for the upstream proxy.
Here's an example:
-
Click Save.
Create an SNAT rule for internal users
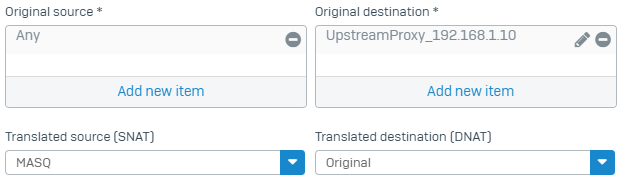
Create a source NAT rule to masquerade web requests from internal users to the upstream proxy.
- Go to Rules and policies, click NAT rules, and click Add NAT rule.
- Set Original source to
Any. - Set Translated source (SNAT) to
MASQ. - Set Original destination to the IP host you've created for the upstream proxy.
-
Set Translated destination (DNAT) to
Original.Here's an example:
-
Click Save.
Create firewall rule to allow traffic from the upstream proxy to WAN
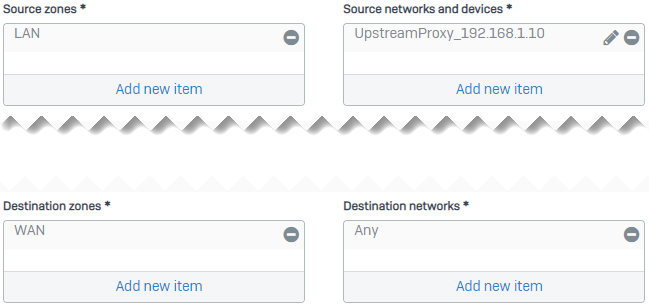
Create a firewall rule to allow traffic from the upstream proxy in the LAN zone to WAN.
- Go to Rules and policies, click Add firewall rule, and click New firewall rule.
-
Set Source zones to
LAN.Alternatively, select DMZ if the upstream proxy is in the DMZ.
-
Set Source networks and devices to the IP host you create for the upstream proxy.
-
Set Destination zones to
WAN.Additionally, select DMZ if you want to allow traffic from the upstream proxy to your web servers in the DMZ.
-
Set Destination networks to
Any.Here's an example:
-
Make sure Web policy is set to
None, and don't select the Malware and content scanning settings. - Select a Detect and prevent exploits (IPS) policy if you want.
- Click Save.
- Drag and drop this rule on the firewall rule list to place it above rules with matching source and destination settings and web proxy mode.
The default SNAT rule (Default SNAT IPv4) at the bottom of the NAT rule list masquerades the private IP address of the upstream proxy for traffic to the WAN zone. The masquerade applies to the upstream proxy in the LAN and DMZ. If you want to specify different translation settings, create an SNAT rule.