Use NAT rules in an existing IPsec tunnel to connect a remote network
Suppose you want to use an IPsec tunnel to connect local hosts to remote traffic selectors, and you don't want to specify those hosts in the IPsec configuration. You can use IPsec routes and NAT rules to send the traffic through the tunnel.
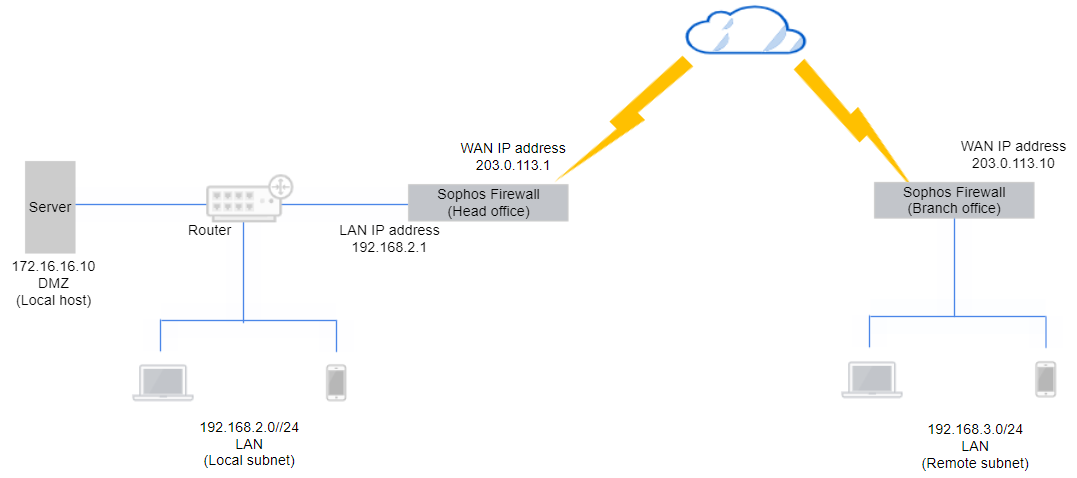
In the example scenario, you've already configured an IPsec connection between the local subnet and remote subnets on the head office and branch office firewalls. See how to configure a site-to-site IPsec VPN.
You must now allow traffic between a local server and the remote subnet through the IPsec connection.
Do as follows on the head office firewall:
- Add an IPsec route from the local server to the IPsec connection.
- Add a DNAT rule with a reflexive (SNAT) rule. When traffic from the remote subnet arrives at the LAN interface (original destination), the DNAT rule translates this destination to the local server (translated destination).
- Edit the SNAT (source NAT) rule to translate the local server (original source) to a LAN host (translated source) that corresponds to the LAN interface. You must create the LAN host in advance because you can't translate to interfaces.
The configuration details are examples based on the following network diagram:
Add an IPsec route
Configure the Sophos Firewall device at the head office to route traffic from the local server to the LAN interface corresponding to the local subnet in the IPsec connection.
- Go to the CLI.
- Enter 4 for Device console.
-
Enter the following command:
system ipsec_route add net <remote subnet> tunnelname <ipsec_tunnel>The command for the example network:
system ipsec_route add net 192.168.3.0/255.255.255.0 tunnelname HO_to_Branch
Add a DNAT rule
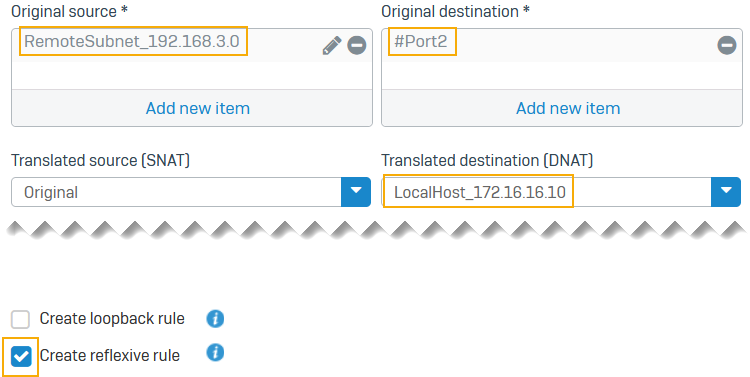
Add a DNAT rule for incoming traffic from the remote subnet to translate the LAN host to the local server.
- Go to Rules and policies > NAT rules.
- Click Add NAT rule and click New NAT rule.
- Enter the rule name.
- Set Original source to the remote subnet (
192.168.3.0). - Set Translated source to
Original. - Set Original destination to the LAN interface (
192.168.2.1). The IP address belongs to the local subnet specified in the IPsec connection. In this example, this IP address has been assigned to Port2, a LAN port. - Set Translated destination to the local server (
172.16.16.10). - Select Create reflexive rule to create a corresponding SNAT rule.
-
Click Save.
Here's an example:
Edit the reflexive (SNAT) rule
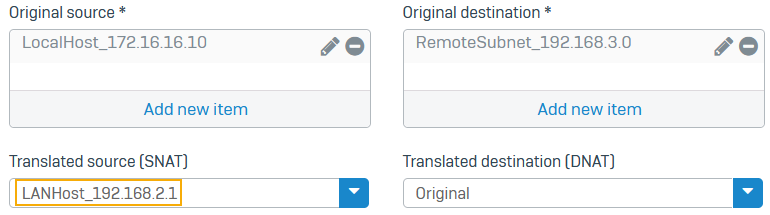
Edit the SNAT rule for outgoing traffic to translate the local server to the LAN host with the LAN interface's IP address.
- Go to Rules and policies > NAT rules.
- Click the reflexive rule you've created.
Example:Reflexive_NAT#_<DNAT rulename> - Set Translated source to the LAN host (
192.168.2.1) with the IP address of the LAN interface.
To be able to select the LAN host, you must create an IP host for this address. -
Click Save.
Here's an example:
You've configured an IPsec route and NAT rules to enable traffic between the local server and the remote subnet to pass through the IPsec connection.