Configure a secure connection to a syslog server
You can use an external certificate to send TLS-encrypted logs to the syslog server from Sophos Firewall. You need to use the default Certificate Authority (CA) of Sophos Firewall.
Introduction
Prerequisite: To establish a TLS connection with the syslog server, you must turn on TLS encryption on the syslog server.
In this example, we use the following:
- Syslog server: syslog-ng
- Client: Sophos Firewall
- External certificate (ExternalCertificate.pem), external key (ExternalPrivateKey.key), and external CA (ExternalCA.pem). You generate these using a third-party CA.
- Default CA certificate (Default.pem) available on Sophos Firewall.
The configuration steps are as follows:
- Specify the attributes and details of the default CA on Sophos Firewall.
- Copy the default and external CA certificates, the external certificate, and the external key to the syslog server.
- On Sophos Firewall, add the syslog server.
- Select the modules for which logs are to be sent to the syslog server.
Configure the attributes for the default CA on Sophos Firewall
To get the CA certificate, specify the attributes for the default CA, and download the file.
-
Go to Certificates > Certificate authorities and click the default CA (Default).
You can't change the CA name.
-
You can change the following attributes:
Name Description Country name Country in which the device is deployed. State The state within the country. Locality name Name of the city. Organization name Name of the certificate owner. Example: Sophos Group Organization unit name Name of the department to which the certificate will be assigned. Example: Marketing Common name Common name or FQDN. Example: marketing.sophos.com Email address Contact person's email address. Private key password If a password was set for the CA, you can change it here. Key type Select from the following options:
- RSA
- Elliptic curve
Key length If you've set the key type to RSA, select the key length. It's the number of bits used to construct the key.
Larger keys offer greater security, but it takes longer to encrypt and decrypt data.Curve name If you've set the key type to Elliptic curve, select the curve name. Secure hash Select the algorithm from the list. -
Click Save.
-
Click download
 for the default CA you updated.
for the default CA you updated.It's a
tar.gzfile. -
Extract the files to get the CA certificate
Default.pem.
Copy the certificate and CA to the syslog server
Copy the default CA certificate of Sophos Firewall and the external certificate and key to the syslog server.
- Go to the syslog server and copy
Default.pemandExternalCA.pemto the/etc/syslog-ng/ca.d/directory. - Copy the syslog server's certificate (
ExternalCertificate.pem) and key (ExternalPrivateKey.key) to the/etc/syslog-ng/cert.d/directory -
Go to the
/etc/syslog-ng/ca.d/directory, and enter the following command to create a hash based onDefault.pem:#openssl x509 -noout -hash -in Default.pemThe result is an alphanumeric hash (example:
52412b66) based on the distinguished name in the CA certificate. -
Enter the following command using the hash with the suffix
.0to create a symbolic link toDefault.pem:#ln -s Default.pem 52412b66.0 -
Edit the
syslog-ng.conffile to point to the certificate (ExternalCertificate.pem), the key (ExternalPrivateKey.key), the third-party CA certificate (ExternalCA.pem), and the CA certificate of Sophos Firewall (Default.pem). Do as follows:- Enter
ExternalCertificate.pemandExternalPrivateKey.keywith the paths for the respective directories. - Enter
ca.dwith the path for the CA directory.
Example
@version: 3.15 @include "scl.conf" source s_src { network(ip(0.0.0.0) port(6514) transport("tls") tls( key-file("/etc/syslog-ng/cert.d/ExternalPrivateKey.key") cert-file("/etc/syslog-ng/cert.d/ExternalCertificate.pem") ca-dir("/etc/syslog-ng/ca.d") peer_verify(required-trusted)) ); }; destination d_local { file("/var/log/messages"); file("/var/log/messages-kv.log" template("$ISODATE $HOST $(format-welf --scope all-nv-pairs)\n") frac-digits(3)); }; log { source(s_src); destination(d_local); }; - Enter
-
Start the syslog-ng server.
Add a syslog server
Add a syslog server to Sophos Firewall, and specify the log settings for the server.
- Go to System services > Log settings and click Add.
-
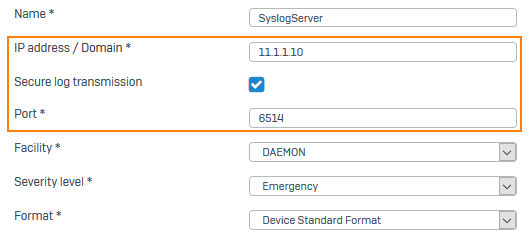
Specify the settings.
Option Description IP address/domain IP address or domain name of the syslog server. Secure log transmission Encrypts logs sent to the syslog server using TLS. Port 6514 -
Click Save.
Here's an example:
-
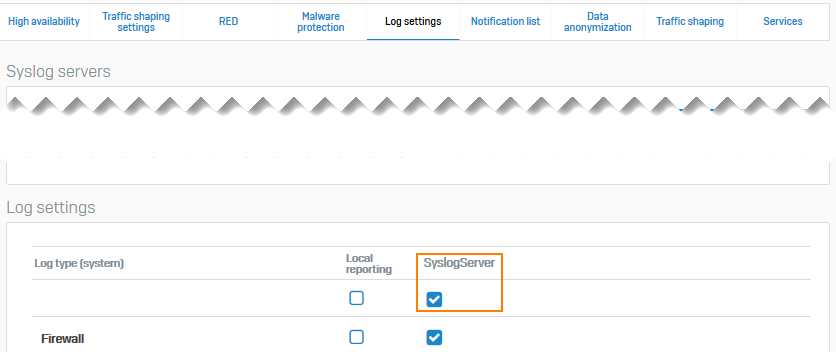
Go to System services > Log settings and scroll down to Log settings. Under Syslog server, select the logs you want to send.
Here's an example: