RED
A Remote Ethernet Device (RED) provides a secure tunnel between a remote site and Sophos Firewall.
REDs connect remote branch offices to your main offices as if the branch office is part of your local network. Using RED interfaces, you can configure and install RED appliances or create a site-to-site RED tunnel between two Sophos Firewall devices in a client-server configuration.
The RED provisioning service supports RED deployment and provides security options, such as enforcing TLS 1.2. We maintain the RED provisioning servers (example: red.astaro.com). You only need to fill the RED configuration details to register with the provisioning server.
-
RED configuration: To allow Sophos Firewall to offer RED services, you must register it with the RED provisioning server. To register Sophos Firewall, do as follows:
- Turn on RED status.
-
Specify the Organization name, City, Country, and Email.
Note
Do not enter umlaut characters (example: Köln) or special characters for the organization name and city. Sophos Firewall uses these details to generate a certificate for secure RED communication.
Make sure the email address you enter here is up to date and accurate. When you add the RED device to a firewall or move it to another firewall, the provisioning server sends the unlock code to this email address.
-
Accept the license agreement.
-
Click Apply.
You can now see the other RED settings on the page.
-
Click Device access to allow RED traffic from the required zones.
-
TLS version settings: Select a TLS version for RED from the following options:
- TLS v1.0 and later: Includes all protocols except SSLv3.
- TLS v1.2 and later: Includes all protocols except SSLv3, TLS v1.0, and TLS v1.1. It also includes the TLS v1.2 ciphers that aren't recommended for use.
- TLS v1.2 (strict) and later: Includes all protocols except SSLv3, TLS v1.0, and TLS v1.1. It includes only the recommended TLS v1.2 protocol ciphers.
Note
We recommend using TLS v1.2 (strict) and later for enhanced security.
-
Automatic device deauthorization: To automatically remove RED appliances' authorization when they remain disconnected from Sophos Firewall for the specified time, do as follows:
- Turn on Automatic device deauthorization.
- Specify a time.
-
Click Apply.
Tip
We recommend that you turn on this option to prevent an unauthorized RED appliance or Firewall RED Client from connecting to Sophos Firewall.
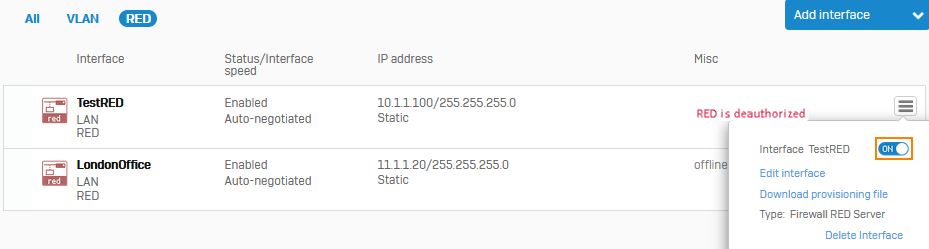
To authorize a deauthorized RED appliance, go to Network > Interfaces. For the RED device you want to authorize, click Menu
 on the right, and turn on the interface.
on the right, and turn on the interface.Here's an example of how to turn on a deauthorized RED appliance:
-
RED unified firmware: RED unified firmware offers the latest features. Some RED devices (example: RED 50) support both legacy firmware and unified firmware. To make sure such devices only use unified firmware, select RED unified firmware.
Note
The RED unified firmware option is only available on RED 15/15w, RED 50, SD-RED 20, and SD-RED 60 devices.
To update the RED firmware, go to Backup and firmware > Pattern updates, and install the RED firmware. RED firmware updates aren't installed automatically. This allows you to schedule downtime.
Note
RED unified firmware is selected by default. If you've migrated Sophos Firewall to a different version, your existing RED setting is migrated. However, if you reset Sophos Firewall to factory configuration, RED unified firmware is selected.
More resources